READER COMMENTS ON
"DIEBOLD VOTING MACHINE KEY COPIED FROM PHOTO AT COMPANY'S OWN ONLINE STORE!"
(67 Responses so far...)
COMMENT #1 [Permalink]
...
leftisbest
said on 1/24/2007 @ 6:18 am PT...
How stupid can you be? The limits are never quite passed, there is always more stupidity when it comes to Diebold and the e-voting companies in general.
However, you might want to know that nothing like that could ever happen in Riverside County, because we use Sequoia, and they are impenetrable (or spelling to that effect!).
Hah!
COMMENT #2 [Permalink]
...
Floridiot
said on 1/24/2007 @ 6:19 am PT...
'Diebold keys, only available to Republican hackers/operatives'
BTW, that key is so short, and I'm no locksmith but if a guy was to learn how, this would be the easiest lock to pick, no?
COMMENT #3 [Permalink]
...
Dredd
said on 1/24/2007 @ 7:25 am PT...
Aha, now we know the key component of Diebold election security ...
COMMENT #4 [Permalink]
...
big dan
said on 1/24/2007 @ 7:36 am PT...
Let's have fun with the "spin" their front men & women come out with on this one.
"We have to trust that no one would do such a thing as copy a key. Therefore, they are still safe. For your accusations to hold any water, you'd have to assume someone would be copying the key. Trust us, no one is copying the key."
COMMENT #5 [Permalink]
...
big dan
said on 1/24/2007 @ 7:39 am PT...
...and we're expected to believe, that Bush won in 2000 & 2004! Now, let's revisit BOTH exit polls that said that Gore & Kerry won! Schmidt/Hackett, Bilbray/Busby. Bilbray, who voted AGAINST helping college loan interest.
COMMENT #6 [Permalink]
...
big dan
said on 1/24/2007 @ 7:46 am PT...
So someone could go down to "Crazy Uncle Joe's Key-O-Rama" and have a key made to ruin our democracy and get people killed with a lunatic president, if they wanted?
COMMENT #7 [Permalink]
...
david porter
said on 1/24/2007 @ 8:11 am PT...
Diebold isn't dumb at all. This gives them plausible deniability in the event that some "evil doer" makes copies of the key and rigs election results.
COMMENT #8 [Permalink]
...
hairy potthedd
said on 1/24/2007 @ 8:20 am PT...
It's troubling to me as a Canuck to see that their key sets are priced in Canadian dollars, also...eh.
COMMENT #9 [Permalink]
...
James M Otos
said on 1/24/2007 @ 8:56 am PT...
If we suspend the war in Iraq for one week we can use the 2 billion dollars to buy a new voting machine for each of us! Not from Diebold, obviously.
COMMENT #10 [Permalink]
...
patginsd
said on 1/24/2007 @ 9:31 am PT...
Did you see that Diebold has been rewarded with a GSA certification for Homeland Security contracts?
Here's the sorry news: sorry news
COMMENT #11 [Permalink]
...
Mr. Freedom
said on 1/24/2007 @ 10:51 am PT...
I think someone should scour their website real good because they probably have posted a videotape of themselves setting the machines so they only count republican votes. "Mwah, hah, hah... let's put this on YouTube so we can show George!"
COMMENT #12 [Permalink]
...
Mark S
said on 1/24/2007 @ 11:47 am PT...
Diebold may be a lot of things, but dumb ain't one of 'em.
They've had several years of experience using these machines in actual elections.
They know that the only way anyone can prove that the machines were rigged, is to audit them. They also know that Congress, the courts, and State and local elections officials have set things up so that the Diebold candidate can be sworn in before any audit can take place, after which there is no way to remove them from office. (See CA50 case info elsewhere on this site.)
Since there is no chance at all of them getting caught before the damage is done and it is too late to change the results, they have no reason at all not to make it as easy as possible for people to do the damage.
And in the unlikely event that they get taken to court for negligence, the possible penalties would be no more than an infinitesimal fraction of their profits, which is an acceptable business expense.
C'mon, people, you know the score. Diebold elects the candidate, the candidate then makes the laws and appoints the judges to protect Diebold from liability, and Diebold continues to elect more candidates.
But it isn't just Diebold or proprietary vendors. Open source software can also be hacked without leaving a trace (google Chuck Herrin and check his "archives" page for details). As long as we have machines counting our votes, our votes won't count. The only way to ensure that we get the candidates we vote for, is to get rid of the machines and have hand-counted paper ballots at the precincts, with full citizen oversight including videotaping of the entire process.
It also happens to be the least expensive way to hold elections.
It is fun, as an academic exercise, to prove that there was election fraud in 2000 and 2004, as so many people have done. But last time I checked, Bush was still in office. People say he's dumb too. Maybe. But if his stock portfolio was on microfiche, I wonder if a professional weightlifter could benchpress it.
COMMENT #13 [Permalink]
...
phil
said on 1/24/2007 @ 1:02 pm PT...
Anyone can pick a lock, just need some (different size) cut up steak knives and something to cause tension. A simple search for "lockpicking" +"pdf" shows a whoping amazing amount of hits for anyone wanting to learn. A key that is photographed is a simple matter to recreate! Easier that pin tumbling (where you "tumble the pins" and tension bar (so you can turn the lock once all the pins are lined up / or down.) Faster too!
The simple fact that these kind of tools are illegal to posess, deters nobody, e.g. they're already going to commit a crime why should they care the tools are illegal?
I'd have to agree that EVM's (Electronic Voting Machine Manufacture's) know exactly what they are doing. They are genius! They have taken over the will of the people.
Anyone catch the other article by John Gideon about An Illinois Representative doing a study for online voting by 2010!!!
I wonder how many times that US representative's SERVERS have been cracked!? They're probably still using HTML mail for god sake.
My current state of mind on this issue.
Just when you get done painting one side of your Truck, the CORPORATE US representatives are again throwing rocks at the other side again. I feel like these corporate bastards are the equal to occupying the United States. How much more of this are we going to put up with? Oh that's right, people still don't understand electronics has no place in our elections, because they are not aware of the problem, because the corporate media will not open their mouths.
What we all need is a giant grassroots wrench to put into these corporate interests gears. Once and for all, end it for them. Make metal shavings out of them.
I sure hope I hear something BIG come from Debra Bowen pretty soon. I am tired of this war on our constitutional right to vote.
I HATE THE CORPORATE MEDIA! HATE!!!
THIS IS A NATIONAL SECURITY ISSUE!
COMMENT #14 [Permalink]
...
Mozart
said on 1/24/2007 @ 1:22 pm PT...
Regarding the Original Constitution made of hemp paper--the REAL one has been taken away and no one knows where it really is, if it still exists.
The one there now is a FAKE ONE!
This info is from a highly-reliable intel source. Nothing is as it seems.
COMMENT #15 [Permalink]
...
howdy
said on 1/24/2007 @ 1:52 pm PT...
So, umm, a poll worker could "...launch a "denial of service" attack simply by breaching the "security seals" of each machine and forcing it immediately offline..." and get away with it?
COMMENT #16 [Permalink]
...
big dan
said on 1/24/2007 @ 2:14 pm PT...
Slightly OT...but, did you notice in all the articles about Bob Ney getting the slammer, they never mention that he was also behind HAVA? Which was majorly responsible for e-vote machine proliferation, as it stands today?
Are YOU telling ME, that all these slammer articles about Bob Ney, the writers of these articles did not know he was behind HAVA? Do you think I'm STUPID???
The ONLY place I saw a headline with "Ney/Jail/HAVA" all in the same article, was this one at Black Box Voting:
"""(US) HAVA sponsor Bob Ney sentenced t... """
http://www.bbvforums.org...h.cgi?file=/8/46466.html
Are YOU telling ME...that Bev Harris...and ME...know this...but the corporate mainstream media DOES NOT???
So....EITHER...
1. The corporate mainstream media STINKS!
or
2. They PURPOSELY made sure NOT TO MENTION in the same breathe/article, that a guy WHO IS NOW IN JAIL is RESPONSIBLE FOR PROLIFERATING E-VOTE MACHINES THROUGHTOUT OUR COUNTRY!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
COMMENT #17 [Permalink]
...
Shii
said on 1/24/2007 @ 2:16 pm PT...
We wouldn't keep the Consitution locked up with a minibar key.
So why is it the only thing protecting democracy from malicious hackers?
COMMENT #18 [Permalink]
...
big dan
said on 1/24/2007 @ 2:16 pm PT...
...OR...
3. They stink AND they purposely did this.
...OR...
4. (there is no #4)
COMMENT #19 [Permalink]
...
cv
said on 1/24/2007 @ 2:22 pm PT...
I used to be a locksmith --- software engineer now --- and I can tell you that security is security and that the my locksmithing past has been highly informative when it comes to writing secure code.
... and to see that key... O.M.G. ... and to hear they had a picture of it on the web... O.M.F.G...
These guys obviously don't know crap about security.
A child can pick that type of lock with a couple paper clips. You can buy this type of lock in bulk for under a dollar each --- they aren't a secure lock, they're a convenience lock. Any locksmith worth his salt can look at that picture, name the keyway, and punch out an exact duplicate with a key clipper.
This is corporate neglegence and these people should be prosecuted. Neglegent in posting that picture, and even more neglegent in choosing to use that type of cheap lock on these devices.
To those that don't understand software and software security, and all the experiments and tests and blackbox's claims and etc.: I would take this as physical evidence that Diebold either doesn't understand or care about basic security on these devices. If they cut corners (or just plain screwed up) on security for the device's hardware itself, I would highly doubt they did a much better job securing the software running inside.
COMMENT #20 [Permalink]
...
cv
said on 1/24/2007 @ 2:29 pm PT...
PHIL:
"Anyone can pick a lock, just need some... "
Anyone can pick this type of lock, sure, but the point is that they could have used a lock that wasn't pickable (there's several choices).
Also --- point of fact, I don't think it's actually illegal to posess lock picks.
COMMENT #21 [Permalink]
...
the_zapkitty
said on 1/24/2007 @ 3:56 pm PT...
... howdy said...
"So, umm, a poll worker could "...launch a "denial of service" attack simply by breaching the "security seals" of each machine and forcing it immediately offline..." and get away with it?"
Well, yes... assuming that the election workers actually treated the breached seals as a matter of security.
But then, as you well know by now, election workers across the nation have been told repeatedly in the past to ignore breached seals.
As for your "they couldn't get away with ignoring something like that!"? The reality is "yes they have gotten away with ignoring things like that"... repeatedly.
COMMENT #22 [Permalink]
...
phil
said on 1/24/2007 @ 6:11 pm PT...
cv
I stand corrected. And yeah I was gonna say paperclip and nailfile ;o)
But, this is a pattern with electronic voting machines.
The fact remains you can not validate the electronic signals inside the box 24/7. (You can't validate the actual chips inside the box either, they could be specially crafted in the doping process)
Therefore you can not validate the vote, and if you can't validate the vote, then you have denied people their constitutional right to vote.
A hammer is about the only thing I can think of to fix this problem. But that is a felony.
COMMENT #23 [Permalink]
...
dodgeit
said on 1/24/2007 @ 6:25 pm PT...
I can not believe what I am seeing. this is deeply concerning. what can be done to make sure people know about this? if word gets out to the masses maybe they will have no choice to revert to video recorded paper ballot counting. dugg
COMMENT #24 [Permalink]
...
Nigel Russel
said on 1/24/2007 @ 7:43 pm PT...
Maybe it was put up by some employee who is sick with Diebold and the horrid security. With leaks like this eventually they're bound to collapse under the weight against them.
It would certainly be something I would hope a just employee would do while working for an unjust company.
COMMENT #25 [Permalink]
...
LakshmiNarayanan
said on 1/24/2007 @ 9:30 pm PT...
Its sorry to know abt this.I think we have a beter secure Electronic voting machine here in india.Its simple and robust built by the Govt itself and not external firms.
COMMENT #26 [Permalink]
...
phil
said on 1/24/2007 @ 9:55 pm PT...
It's a NATIONAL SECURITY ISSUE!
DHS is so full of crap, they can suck my sweaty balls.
DO YOU HEAR ME!? SUCK THEM!
#25 LakshmiNarayanan
With all due respect, screw India and it's god damn electronic voting machines. They're not any better than any other electronic voting box. They still can not be validated. If you believe they can you've been misled. If you *say they can* your lieing.
Dear corporate media, BURN IN HELL, THE HELL YOU'VE CREATED.
COMMENT #27 [Permalink]
...
the_zapkitty
said on 1/24/2007 @ 10:00 pm PT...
... LakshmiNarayanan said...
"Its sorry to know abt this.I think we have a beter secure Electronic voting machine here in india.Its simple and robust built by the Govt itself and not external firms."
And the software is a government secret, the chips are as subject to built-in tampering as chips anywhere else, and there is no backup... no paper ballot... nothing... if the machine goes south the ballots are lost forever.
Sure. Let's have Rep. Holt submit that proposal...
(The zapkitty extends his claws)
... at least it would all be over with rather quickly 
COMMENT #28 [Permalink]
...
phil
said on 1/24/2007 @ 10:02 pm PT...
It's clear nobody and mean NOBODY except for us on a couple blogs cares about national security, so what are we going to do about this.
How are we going to RAISE awareness?! beyond this stupid web?
COMMENT #29 [Permalink]
...
cdb
said on 1/25/2007 @ 12:27 am PT...
Accountability is dead, long live "getting away with it, and ignoring the consequences if you stop getting away with it".
Yay..! There used to be a saying that went something like "fool me once, shame on you, fool me twice, I'm the dork". How many times has this company fooled the public officers and representatives of the USA? How many times have those officers and representatives been held accountable for their being fooled?
So when are they going to learn not to do this again? No one that they care about is trying to teach them that what they have done is a bad thing, and that they should have some responsibility. That applies to the companies and to the officers and representatives.
C'mon people, be angry about this. Hold someone to account. It's your job to do that, no-one elses.
COMMENT #30 [Permalink]
...
vento mareiro
said on 1/25/2007 @ 3:01 am PT...
Why do the folks in the U.S. always try to do things so complicated? In Spain, we use the good old envelope with the vote inside. After showing your ID, you put it in a glass ballot box and you're done. When the election is over, votes are counted and that night the results are avaliable. That's all, as simple as it can be, with enough police and observers from all political parties to assure fairness.
COMMENT #31 [Permalink]
...
Rumple Stiltskin
said on 1/25/2007 @ 5:01 am PT...
A Chinese abacus would be more accurate, and secure.
COMMENT #32 [Permalink]
...
big dan
said on 1/25/2007 @ 5:50 am PT...
Why doesn't Brad start a donation to have this guy make 1 million keys and mail them out to 1 million people across the country? To make a point?
COMMENT #33 [Permalink]
...
samL75
said on 1/25/2007 @ 6:12 am PT...
Get active. Tell all your family about this and have them tell as many people as possible and all together flood your local news agencies with this information about the security frauds. With not just complaints, but also the solution, papre ballots that can be recounted until the cows come home.
COMMENT #34 [Permalink]
...
joe college
said on 1/25/2007 @ 7:55 am PT...
COMMENT #35 [Permalink]
...
M-3
said on 1/25/2007 @ 8:21 am PT...
You should have kept your mouth shut about this one. You probably could have used the key to get into Diebold's headquarters and into their safe where you could have stolen all of their great security secrets... and then used it to get away in one of their company cars!
COMMENT #36 [Permalink]
...
Shaper
said on 1/25/2007 @ 8:48 am PT...
Great work reporting, and always nice to see Diebold get a solid nut-kicking from us mere proles.
OTOH, nothing does more to harm your cause than the constant "oh my, aren't we the only people in the world who know and/or care about this" crowing.
Plenty of people know about Diebold's disgraceful "security", and their suspicious political dealings with the Republican party, and the fraud during the last two US presidential elections - it's all over the net, and finally the mainstream media is beginning to wake up and pay attention (where doing so wouldn't unduly compromise their corporate interests, naturally).
However, nothing makes it easier for people new to the issue to dismiss your writing as the rabid frothings of a conspiracy nut like the constant "poor little me" or unnecessarily-smug comments like "subsequently ignored by all media except for The BRAD BLOG, natch".
If you want to be taken seriously, tone down the unprofessional smugness and write like a professional - recognise the pioneering work being done by other online groups like Black Box Voting, and stop claiming al lthe credit for yourself. People need to hear what you're saying, but the way you say it ruins your chance of being taken seriously.
COMMENT #37 [Permalink]
...
Johnny Freedom
said on 1/25/2007 @ 8:48 am PT...
Why don't people just rig the vote themselves (hopefully for a third party) if it is so easy to do? If the vote is already being rigged then it is not like they would be doing an injustice to other voters (who would not have gotten their vote counted anyways). That would be a way of taking things back into the peoples' hands (sorta).
COMMENT #38 [Permalink]
...
Shadowslay
said on 1/25/2007 @ 9:35 am PT...
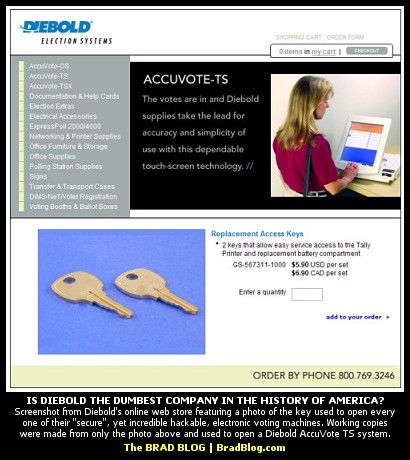
You guys have no idea what you are talking about! That key is not to the TSX touchscreen voting unit at all. That is an old key used in the Accu-vote OS (Optical Scan) machine. The optical scan machines use paper ballots. I work for an Election Commission in TN. We have had optical scan machines since 1998, way before touchscreen voting was even around I have an Accu-vote TSX key sitting right in front of me right now. It looks nothing like it. You can't just walk up to a touchscreen and open the memory card compartment mess with it. The memory cards that contain the ballot information leave the election commission preprogrammed and have a security encryption key of 16 letters and numbers long. Unless the security key programmed from the memory card matches the security key on the Touchscreen the touchscreen will not even read the memory card. I know touchscreen units from top to bottom, it's my job, it's what I make a living doing. You people need to do some research before you start spreading negative rumors around. If you have any questions regarding security please email me at
nathanielfoster@boxbe.com
I will be more than happy to ease your security concerns.
COMMENT #39 [Permalink]
...
jose
said on 1/25/2007 @ 9:37 am PT...
OK, I just joined the dots. Or you can call it the X files. Venezuela and the USA are not in the best of terms, nothing that lots of cash will fix (in this case Venezuelan Cash). I think Venezuelan Voting machines have been hack, by the company who makes them, I knew that someone in Venezuela owned a voting machine company in the states. Maybe this was the purpose of this machines, to create mis information. dono which voting machine company.
COMMENT #40 [Permalink]
...
Brad
said on 1/25/2007 @ 10:43 am PT...
Replying to Shadowslay:
First, the folks at Princeton used the key on the Diebold AccuVote TS (paperless, touch-screen) machine. Furthermore, I can independently confirm that the same key is used for every AccuVote TSx (touch-screen w/ so-called "paper trail") as well.
Next, while I don't know if the key also opens the AccuVote OS (op-scan) as you suggest, it would hardly surprise me. Since you claim to be a pro with these things then, certainly you also know then that the AccuVote OS is as hackable (if not more so) than the TS series. (The HBO documentary Hacking Democracy covered the hack of a Diebold OS system in Leon County, FL in Dec. 2005 which flipped the results of a mock election without leaving a trace behind).
As to the encryption that is or isn't used on the various systems, the encryption used on the TS is different from the TSx. Furthermore, passwords to the systems are usually the default "1111" and finally, since you're an insider and your note suggests you're familiar with the 16 character encryption key you mention, what's to stop you from rigging an entire election with that access to your county's voting machines?
Appreciate your comments, Nathaniel.
COMMENT #41 [Permalink]
...
DaveMac
said on 1/25/2007 @ 11:00 am PT...
I disagree with comment #38. I formerly worked for a local Board of Elections and worked quite closely with these exact machines. Although I could never be 100% sure, that photo certainly looks like the key I remember using. Additionally, that article was correct... there is one key for all machines nationwide. Inside this compartment is a PCMCIA card which holds both the election data and the tabulated results.
So far as his comment of "Unless the security key programmed from the memory card matches the security key on the Touchscreen the touchscreen will not even read the memory card." I am unsure of that. I am pretty sure in testing we swapped PCMCIA cards from one machine to another without issue.
Perhaps they have only one encryption key. PCMCIA cards from Micro Center would not work, cards bearing the key would. That is worth drilling down on.
COMMENT #42 [Permalink]
...
valeriob
said on 1/25/2007 @ 11:07 am PT...
Has anyone here actually keyed into the computers, uploaded viruses, or done anything to change the outcome of the number of votes during the elections?
Does anyone here even know of anyone who has, or heard of someone specific who has done this?
Did everyone here with a witty comment even vote in 2004 or for any other state/local elections?
We should all stop trying to make up ridiculous stories and fairy tales. Until someone can give me an exact person/place/time this happened, its all bullsh*t.
And the "corporate media" everyone is referring to is overwhelmingly liberal. For you to accuse the liberal media of not exposing scandal is irresponsible and make you hypocrites.
COMMENT #43 [Permalink]
...
the_zapkitty
said on 1/25/2007 @ 11:45 am PT...
... Shadowslay said on 1/25/2007 @ 9:35 am PT...
"You guys have no idea what you are talking about!"
Actually, we do. And we have reliable sources of information...as opposed to, let's say, EVM vendors' handouts.
http://www.freedom-to-tinker.com/?p=1113
"That key is not to the TSX touchscreen voting unit at all. That is an old key used in the Accu-vote OS (Optical Scan) machine."
http://www.freedom-to-tinker.com/?p=1113
"The optical scan machines use paper ballots."
Optical scan machines are as hackable as DRE's... the only difference is that the ballot is actually there to recount when the machine srews up.
"I work for an Election Commission in TN. We have had optical scan machines since 1998, way before touchscreen voting was even around I have an Accu-vote TSX key sitting right in front of me right now. It looks nothing like it."
http://www.freedom-to-tinker.com/?p=1113
The Princeton University team says otherwise... now which shall we believe?...
... and why don't you bring this up with them? I know commentary from sommeone who actually works with the machines would be most welcome 
"You can't just walk up to a touchscreen and open the memory card compartment mess with it."
Reality says different.
"The memory cards that contain the ballot information leave the election commission preprogrammed and have a security encryption key of 16 letters and numbers long. Unless the security key programmed from the memory card matches the security key on the Touchscreen the touchscreen will not even read the memory card."
Many assumptions on your part. You are assuming that Diebold actually implemented the encryption correctly, and history says "probably not", and you're assuming a hack would have to go through the encryption to get at the code... and again Diebold's history says "probably not".
http://www.freedom-to-tinker.com has several articles on precisely that subject, and they illustrate that Diebold's security claims for the encryption are pretty much irrelevant to preventing an actual hack.
"I know touchscreen units from top to bottom, it's my job, it's what I make a living doing. You people need to do some research before you start spreading negative rumors around."
We do. Princeton did. Have you? Aside from reading EVM vendor handouts, that is?
"If you have any questions regarding security please email me at
nathanielfoster@boxbe.com
I will be more than happy to ease your security concerns."
Yes. "Easing security concerns" might be in your interest.
But if you're an election worker then your job is ensuring ballot security. Your job is not blindly defending Diebold while trying to PR spin another of their disasters at the expense of honesty with your voters.
After all, you can't rely on Diebold to do your job for you... as they sure as hell haven't shown any intrest in ensuring ballot security.
http://www.freedom-to-tinker.com/?p=1113
COMMENT #44 [Permalink]
...
the_zapkitty
said on 1/25/2007 @ 12:02 pm PT...
... valeriob said on 1/25/2007 @ 11:07 am PT...
"Has anyone here actually keyed into the computers, uploaded viruses, or done anything to change the outcome of the number of votes during the elections? Does anyone here even know of anyone who has, or heard of someone specific who has done this?"
Google "Hursti Hack" and "Princeton Virus Video"
"Did everyone here with a witty comment even vote in 2004 or for any other state/local elections?"
Nah. We aren't concernined with voting. Why do you ask?
"We should all stop trying to make up ridiculous stories and fairy tales."
We are trying to put a stop to it, but for now the e-voting corporations insist on telling the same old ridiculous stories and fairy tales.
"Until someone can give me an exact person/place/time this happened, its all bullsh*t."
Google "Hursti Hack" and "Princeton Virus Video"
And the "corporate media" everyone is referring to is overwhelmingly liberal. For you to accuse the liberal media of not exposing scandal is irresponsible and make you hypocrites.
And just which variety of LSD were you taste-teasting?
COMMENT #45 [Permalink]
...
the_zapkitty
said on 1/25/2007 @ 12:25 pm PT...
... jose said on 1/25/2007 @ 9:37 am PT...
"... I think Venezuelan Voting machines have been hack, by the company who makes them, I knew that someone in Venezuela owned a voting machine company in the states. Maybe this was the purpose of this machines, to create mis information. dono which voting machine company."
Lessee... the "you're all conspiracy loonies" shill, the perhaps-really-an-honest-election-worker-but-still-a-shill, the "the poll workers would never allow that" shill, and now the "let's try to confuse them with Sequoia" shtick.
All present and accounted for.
BTW... considering the somewhat incestuous links between Diebold and Sequoia isn't the last variety kind of like they're eating their own young or something?
COMMENT #46 [Permalink]
...
Brad
said on 1/25/2007 @ 12:36 pm PT...
Time to play whack-a-mole with Valeriob!:
We should all stop trying to make up ridiculous stories and fairy tales. Until someone can give me an exact person/place/time this happened, its all bullsh*t.
Good plan! Think of all the money we could save on bank vaults and homeland security and stuff if we just waited for the bank to be robbed before installing security.
The fact that Electronic Voting Machines have been shown, in no uncertain terms, to be hackable in dozens of ways which would likely never be discovered, is hardly either "ridiculous" or a "fairy tale".
Unless you consider dozens of computer science and security experts from Princeton University to Johns Hopkins to UC Berkley to NYU's Brennan Center of Justice, or reports from the GAO, NIST, NASED Baker/Carter National Election Reform Comm. (okay, an imperfect example), or the actual live hacks performed by computer experts from Harri Hursti to Dr. Hugh Thompson to Dr. Michael Shamos, et al to be "ridiculous". Then you are truly living in the all-spin world of Bill O'Reilly.
And the "corporate media" everyone is referring to is overwhelmingly liberal.
Aha, thanks for clearing that up. You are living in the all-spin world of Bill O'Reilly. Careful you don't get too dizzy and trip over your own uninformed horse-shit.
But have a great day!
COMMENT #47 [Permalink]
...
Allen
said on 1/25/2007 @ 12:41 pm PT...
valeriob says,
"the "corporate media" everyone is referring to is overwhelmingly liberal."
That's a common misconception. I believe that you are parroting comments. The people you hear that from know how effective that lie is. It is an easy deception of conflation. Faces on TV are probably what some would call liberal but more actually are people who would vote Democrat (if they vote and some don't to maintain objectivity). They are probably not "liberal" on say, gun control.  Anyway, any college graduate is more likely to vote Democrat so ANY profession is "liberal." if you squeeze the numbers hard enough.
Anyway, any college graduate is more likely to vote Democrat so ANY profession is "liberal." if you squeeze the numbers hard enough.
Whereas the owners and managers of those organizations are deeply tied to (Sorry, I have no better way to put it) the military/industrial complex.
The confusion comes here: The MOST powerful corporations (oil, pharmaceuticals, so on) are not supportive of the majority of the Democrat's platform. Yet, as enlightened worldly types (such as the Cheneys) they are highly tolerant of being gay (for example).
When you listen to Rush L. and such, they confuse liberalism (government getting out of your face: pro-gun, pro-gay, pro-choice) with the platforms of the two major U.S. parties. The Dems are not liberal on many issues. The Reps are liberal leaning on many issues.
Wealthy people (anti-tax) love the Republican party and USE the religious dupes (a preselected gullible audience*) to get their agenda's through --- their own kids get abortions in other countries or live as gay couples in enlightened wealthy communities.
"You can fool some of the people all of the time, and those are the ones you want to concentrate on."
GWB, March, 2001
COMMENT #48 [Permalink]
...
saskboy
said on 1/25/2007 @ 2:07 pm PT...
I don't want to believe that the reason why people don't understand how "video voting" is a fraud in our democracy, is because they are stupid. Maybe if the TV media explained it to them, they'd get it. Man of the Year was a movie that tried in a little way at least.
COMMENT #49 [Permalink]
...
Brandon Walters
said on 1/25/2007 @ 3:18 pm PT...
That is pretty sad. How much crap like this has to happen before something is done? I can't believe we put our trust in this company (or any other private company for that matter). Any voting system we trust should be built by the government by people with security knowledge, not the morons currently building these machines.
COMMENT #50 [Permalink]
...
Nobody
said on 1/25/2007 @ 5:02 pm PT...
National Lock Company D8785 blank, hardware store equivalents RO-3. Cuts look to be 1-2-4-2-5. Trivial to pick, impression, or duplicate.
Sheesh! They probably saved all of $3 per machine by not going to a Medeco cylinder. And they're all keyed alike!!! WTF?
At a bare minimum, a Medeco cylinder keyed differently for each customer would be expected. And how about a microswitch that shuts down the machine when the compartment is opened, requiring a code or the like to restart the box?
COMMENT #51 [Permalink]
...
phil
said on 1/25/2007 @ 6:47 pm PT...
#42 valeriob
There are five main sources of corporate media. Wikipedia lists (ABC, CBS, NBC) and (I add FOX, AND PBS) all of which do not serve the public interest! I know this because I do a show on Public Access Public access television is one type of PEG access, short for Public, Educational, and Governmental, the three traditional structures of access within a municpality.
The fact remains, Corporate Media does not serve the public interest.
The big Telcos would like to see Public Access disappear. But that's a whole other can of worms that slowly attempting to rot PEG tv by not playing by the existing franchising rules. They say it's not fair to them, while I'd say removing the Public's First amendment right is unfair as well. There's other spins on this, but that's my opinion.
As far as Liberal Media or Conservative media goes I think your trying to confuse issues about Media Bias. Basically you are using a term that some psyop dingbat has used.
As far as cracking electronic voting machines, I say to you: Prove these machines have not been cracked! Anyone with the knowledge of the physics of electronics knows that this is an abusive technology that can not be validated because of the physics of electricity itself.
As far as witty comments go, a lot of concerned citizens and nice folks have been fighting this war on our constitutional right to vote for many years now. I consider myself a voter rights advocate and I personally am at my wits end, literally one event away from totally snapping. I don't like oath breakers, and have had it with the destruction of our constitution. You should be glad that there are other folks around that have a cooler head than myself. I personally won't tolerate anything but the total removal of electronics from the election process. e.g. From end to end.
I've crpssed paths with you before, either here or on DU a couple years ago, I Know what your doing, "stirring the pot" It's a good tactic, but your not going to get far here. Folks here are hip to these games. And clearly if you were being honest (which you were not) with your questions you yourself are the hipocrit in that you say you haven't heard these issues before, yet it's the "liberal media" (your words not mine) that would expose them.
I'll just straighten this out, forget liberal media, think CORPORATE MEDIA. The CORPORATE MEDIA HAS NOT SHOWN THE PUBLIC THESE ISSUES OR IT WOULD BE TOP OF THE NEWS EVERY NIGHT.
Furthermore, not just these stupid ass keys, but the whole of all the sum of the parts of all these electronic voting machines, tabulators, networks, and digitized data is the cause of all our constitutional problems, including the war in Iraq and these unvalidatable, vulnerable systems, networks and devices are the greatest national security issue this country has ever seen in history.
COMMENT #52 [Permalink]
...
big dan
said on 1/25/2007 @ 8:05 pm PT...
valoriob: YOU'RE a f***ing fairy tale...
...and I wrote to nathanielfoster@boxbe.com , and it asked me for my credit card number...
COMMENT #53 [Permalink]
...
big dan
said on 1/25/2007 @ 8:06 pm PT...
Maybe Nathaniel would like to take a "million-to-one" bet on this one, like that guy who's sweating his balls off now!
COMMENT #54 [Permalink]
...
big dan
said on 1/25/2007 @ 8:13 pm PT...
Brad, ever notice that whenever you post an article catching DIEBOLD with their pants down to the point where they can't even "spin" it, you get mysterious one-time/first-time-ever commenters, siding with DIEBOLD? How much is DIEBOLD payin' these creeps? That's exactly how the CMSM works, and it's a tribute to your site, these trolls/shills/paid misinformation artists.
valeriob & nathaniel are regular Brad Blog readers, who have always disagreed with your blog, but never posted before...but yet read a blog they totally disagree with...and they "came out" today! CONGRADULATIONS TO YOU TWO!
COMMENT #55 [Permalink]
...
Bev Harris
said on 1/25/2007 @ 10:02 pm PT...
Brilliant article, again, Brad.
Makes this scene from the HBO film "Hacking Democracy" even more a theatre of the absurd:
The scene: April 21, 2004, Calif. VSPP member David Jefferson grilling then-president of Diebold Election Systems, Inc Bob Urosevich:
[referring to using the same 1111 password for every voting machine in America and then leaving the source code on the Internet showing the password:
"It's as if you used the same key for every house in America, and PUBLISHED THE PICTURE ON THE WALL. This is below even the minimum standards of security..."
[Urosevich] busies himself brushing imaginary specks of dust off his podium
* * * *
Little did Jefferson know his analogy would turn literal.
Love your work, and besides being hilarious, this story truly is journalistically important and in a sane world, would have made the evening news on every network.
Bev Harris
Founder
Black Box Voting
COMMENT #56 [Permalink]
...
WayneB
said on 1/25/2007 @ 11:21 pm PT...
There's very little left to do after hearing news like this other than stockpiling food, water and guns, imho, but maybe that's just me.
This kind of corrupt nonsense seems to be running rampant throughout our government, not just in the voting process. And there seems to be no end in sight because apparently no one of any authority seems willing to do anything about this or the hundreds of other political atrocities that occur in the US government every day.
COMMENT #57 [Permalink]
...
Albert
said on 1/25/2007 @ 11:50 pm PT...
COMMENT #58 [Permalink]
...
Please Compare
said on 1/26/2007 @ 9:48 am PT...
Could someone start hacking the old mechanical machines as a comparison to see if Diebold has improved over the current state of the art? The old mechanical machines look extremely insecure to me, so maybe Diebold is an improvement?
COMMENT #59 [Permalink]
...
Mike
said on 1/26/2007 @ 9:53 am PT...
Relax.. its just a key to the printer and battery storage. Not the unit itself. Clicking on the screen shot shows you that access to the machine's memory is done via magnetic card, not key.
COMMENT #60 [Permalink]
...
Barry
said on 1/26/2007 @ 10:25 am PT...
Hmm... Students of Princeton have 1. the key to access the location to insert a virus and 2. the virus to reprogram all the machines from a single one. Why do I get the feeling our next president will be Joseph David Oznot?
COMMENT #61 [Permalink]
...
dinsdale
said on 1/26/2007 @ 11:11 am PT...
Enough is enough. America needs a paper BALLOT --- not "trail" or "record" --- for every vote cast. Period.
Make sure it's not a butterfly ballot, tho. They tend to be migrate-tory. Use coconuts instead.
I guess in order to secede in Murica anymore, you have to be not only white, but as dumb as shrub, as well.
COMMENT #62 [Permalink]
...
the_zapkitty
said on 1/26/2007 @ 12:00 pm PT...
... Please Compare said...
"Could someone start hacking the old mechanical machines as a comparison to see if Diebold has improved over the current state of the art? The old mechanical machines look extremely insecure to me, so maybe Diebold is an improvement?"
You couldn't... without a hacksaw 
The old lever machines could be compromised 1 by 1... and this was known, the methods known, and everyone could watch out for those methods, and a compromised machine could be identified by inspection.
E-voting machines, being computers running Windows, can be hacked en masse by an exceptionally wide variety of means by just compromising one machine somewhere in the chain of custody (whenever there even is a chain of custody given the haphazard security surrounding e-voting machines), the methods are not especially obvious except to those who deal with computers, and the evidence of tampering can be made to disappear tracelessly after the election is over.
BTW, calling all shills...
Whatever happened to the shill line that ran "Diebold will be getting out of the elections business soon so please stop talking about these amazingly egregious security lapses!"
It was nice dream... but of course Diebold has no intention of ever letting go of the near-infinite money and power granted by owning an e-voting disenfranchise, right?
COMMENT #63 [Permalink]
...
the_zapkitty
said on 1/26/2007 @ 12:26 pm PT...
... Albert said...
"Looking for an image of keys in diebold site?
Try this;"
But that google image links back to the Diebold site... where they have now replaced the damning image of the key with a completely unrelated "security card" ad.
Diebold finally removed it.
Diebold finally removed it after a month of ignoring repeated warnings about the security risk the key posed.
Diebold finally removed it after how many years of the image just sitting there while literally compromising our entire democracy?
COMMENT #64 [Permalink]
...
the_zapkitty
said on 1/26/2007 @ 12:44 pm PT...
... Mike said...
"Relax.. its just a key to the printer and battery storage. Not the unit itself."
No. It's the key to the unit itself... but of course you knew that.
http://www.freedom-to-tinker.com/?p=1113
"Clicking on the screen shot shows you that access to the machine's memory is done via magnetic card, not key."
No, it is not and it never was. Diebold would not put anything so expensive as a card lock on their cheaply built voting machines. It would have cut into their profit margin.
The card ad now shown on that page is new and is unrelated to the memory card door key that was there for... how many years?
So clicking on the google image linked to by Albert takes you back to the Diebold site where they have finally removed the image of the key after a month of repeated warnings... and after just how many years of the picture of the key sitting there and handing our democracy over to anyone who looked at it?
But of course you knew that as well... didn't you? But let's be charitable and assume that you just failed to actually read...
http://www.freedom-to-tinker.com/?p=1113
It won't go away no matter how much spin Diebold shills try to put on it.
COMMENT #65 [Permalink]
...
John
said on 1/27/2007 @ 11:49 am PT...
You don't have to hack the key. It's a standard alarm panel key, and anyone who's ever serviced alarm systems has several.
COMMENT #66 [Permalink]
...
Breton Philip
said on 1/27/2007 @ 2:26 pm PT...
Diebold might get the message if people refuse to use their bank's Diebold ATMs based on the premise Diebold should not be trusted with money if they can not be trusted with votes.
COMMENT #67 [Permalink]
...
the_zapkitty
said on 1/27/2007 @ 8:28 pm PT...
... John said...
"You don't have to hack the key. It's a standard alarm panel key, and anyone who's ever serviced alarm systems has several."
... and it's a standard jukebox key... ...and it's a standard file cabinet key... ... and it's a standard hotel minibar key... ... the list is long...
 Good lord in heaven. How dumb are these guys at Diebold?! Can you believe the United States has actually entrusted them to build a security system for the original U.S. Constitution, the Declaration of Independence and the Bill of Rights?!
Good lord in heaven. How dumb are these guys at Diebold?! Can you believe the United States has actually entrusted them to build a security system for the original U.S. Constitution, the Declaration of Independence and the Bill of Rights?! FURTHER UPDATE 7:39pm PT: Diebold pulls a bait and switch...
FURTHER UPDATE 7:39pm PT: Diebold pulls a bait and switch...

 Trump Labor Dept. Warns Trump Policies Sparking Food Shortage, Farmworker Crisis: 'BradCast' 10/9/25
Trump Labor Dept. Warns Trump Policies Sparking Food Shortage, Farmworker Crisis: 'BradCast' 10/9/25 'Green News Report' 10/9/25
'Green News Report' 10/9/25
 Trump's Losing Battles: 'BradCast' 10/8/25
Trump's Losing Battles: 'BradCast' 10/8/25 'Supreme Arrogance': Trump, John Roberts and His Stacked, Packed and Captured SCOTUS: 'BradCast' 10/7/25
'Supreme Arrogance': Trump, John Roberts and His Stacked, Packed and Captured SCOTUS: 'BradCast' 10/7/25 'Green News Report' 10/7/25
'Green News Report' 10/7/25 Trump Attempting His
Trump Attempting His Sunday 'Shutshow' Toons
Sunday 'Shutshow' Toons Biden Budget Expert: Mass Firings in Shutdown 'Extremely Illegal': 'BradCast' 10/2/25
Biden Budget Expert: Mass Firings in Shutdown 'Extremely Illegal': 'BradCast' 10/2/25 'Green News Report' 10/2/25
'Green News Report' 10/2/25 Why is DOJ Suing 'Blue' States for Their Voter Databases?: 'BradCast' 10/1/25
Why is DOJ Suing 'Blue' States for Their Voter Databases?: 'BradCast' 10/1/25 'A War from Within' Trump's Twisted Mind: 'BradCast' 9/30/25
'A War from Within' Trump's Twisted Mind: 'BradCast' 9/30/25 'Green News Report' 9/30/25
'Green News Report' 9/30/25 'Fear is the Tool of a Tyrant':
'Fear is the Tool of a Tyrant': Sunday 'Long Arm/Small Man' Toons
Sunday 'Long Arm/Small Man' Toons 'Green News Report' 9/25/25
'Green News Report' 9/25/25 I Don't Know What This Means, But I Thought You Should Know: 'BradCast' 9/25/25
I Don't Know What This Means, But I Thought You Should Know: 'BradCast' 9/25/25 Gov't Shutdown Looms as Dems Fight to Save Healthcare Subsidies: 'BradCast' 9/24/25
Gov't Shutdown Looms as Dems Fight to Save Healthcare Subsidies: 'BradCast' 9/24/25 Updates: Homan Bribery; Kimmel Censorship; Our Insane Prez at U.N.: 'BradCast' 9/23/25
Updates: Homan Bribery; Kimmel Censorship; Our Insane Prez at U.N.: 'BradCast' 9/23/25 Trump 'Border Czar' Took $50k in Sting, DOJ Dropped the Case: 'BradCast' 9/22/25
Trump 'Border Czar' Took $50k in Sting, DOJ Dropped the Case: 'BradCast' 9/22/25 MAGA Exploiting Kirk's Death as Their 9/11: 'BradCast' 9/17/25
MAGA Exploiting Kirk's Death as Their 9/11: 'BradCast' 9/17/25 Our Crumbling Courts and Withering Rule of Law: 'BradCast' 9/16/25
Our Crumbling Courts and Withering Rule of Law: 'BradCast' 9/16/25 After Kirk Murder, 1st Amendment, Not 2nd, Under Attack: 'BradCast' 9/15/25
After Kirk Murder, 1st Amendment, Not 2nd, Under Attack: 'BradCast' 9/15/25 SCOTUS Suspension of 4th Amendment an Ominous Threat to Constitutional Republic
SCOTUS Suspension of 4th Amendment an Ominous Threat to Constitutional Republic
 VA GOP VOTER REG FRAUDSTER OFF HOOK
VA GOP VOTER REG FRAUDSTER OFF HOOK Criminal GOP Voter Registration Fraud Probe Expanding in VA
Criminal GOP Voter Registration Fraud Probe Expanding in VA DOJ PROBE SOUGHT AFTER VA ARREST
DOJ PROBE SOUGHT AFTER VA ARREST Arrest in VA: GOP Voter Reg Scandal Widens
Arrest in VA: GOP Voter Reg Scandal Widens ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC
ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States'
LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States' 'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States
'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States FINALLY: FOX ON GOP REG FRAUD SCANDAL
FINALLY: FOX ON GOP REG FRAUD SCANDAL COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION
COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL
CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV
Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV  CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM
CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM
CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL
RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV
VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD
RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud
EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud GOP REGISTRATION FRAUD FOUND IN FL
GOP REGISTRATION FRAUD FOUND IN FL