READER COMMENTS ON
"HACKED: VIRUS IMPLANTED, SPREAD ON DIEBOLD TOUCH-SCREEN VOTING MACHINE!"
(104 Responses so far...)
COMMENT #1 [Permalink]
...
byland
said on 9/13/2006 @ 5:03 pm PT...
It looks like voting machines may soon become obsolete anyway:
"It's ok...just go on in...take a shower...really, it's ok...do some shopping...go to work...go on in."
Poison Air in NYC
What morality do torturers have? Who's using torture now?
Who's trying to rationalize justifications for its use?
Where does that effort come from? The White House.
Who's now the Attorney General...in charge of US law enforcement?
The people who produced and created 9/11 have zero morals.
That's one thing everyone can agree on.
Would anyone capable of committing the attacks on 9/11 be capable of committing further murder?
What kind of morality is at work in ordering the EPA to lie and tell everyone the air, which was known
to be deadly, was safe to breathe and everyone should return to New York?
Where did that effort come from? The White House.
New Yorkers, rescue workers, clean-up workers and tourists...AMERICANS...were all invited to enter
a defined area that was known to contain a poisonous atmosphere. The EPA and the White House
had FULL KNOWLEDGE of the truth.
It's been long documented folks.
Many have already died. Many are dying now. Many more will die.
Picture another defined area into which people were led that contained a poisonous atmosphere.
What picture came to mind?
There's no difference. NYC may as well have been a massive shower stall filled with poison gas.
It's mass murder.
Would OUR government ever do such a thing?
They already did.
http://www.cbsnews.com/s...ational/main567489.shtml
WAKE YOURSELVES UP.
Ask yourselves some questions:
Would anyone capable of committing 9/11 then turn around and be incapable of destroying evidence?
Would OUR government send an organized squad of goons to someone's home to terrorize them
for speaking out?
http://www.unobserver.co...t5.php?id=2589&blz=2
Feel more secure now?
You CANNOT say "Our own government would never do such a thing" as an excuse to not research
this on your own and come to your own conclusions.
Would OUR government ever do such a thing as plan and carry out the attacks on 9/11?
Don't take ANYBODY'S word for it but YOUR OWN.
First, Communicate.
Second, Stay informed.
Third, Develop very good relationships with any number of LOCAL authorities.
Fourth, only a fool goes down with a sinking ship. Have a lifeboat ready.
Fifth, Make a list of personal priorities just in case the current trends in this country continue to accelerate.
Sixth, Don't deny it to yourself IF (when?) conditions make it completely obvious that you need to act in a
way you've already decided for yourself.
Executive Order 11921
Allows the Federal Emergency Preparedness Agency to develop plans to establish control over the
mechanisms of production and distribution, of energy sources, wages, salaries, credit and flow of
money in the U.S.A. financial institution in any undefined national emergency. It also provides that
when a state of emergency is declared by the President, Congress cannot review the action for six months.
and...
http://www.berkeleydaily...-06-06&storyID=23155
and...
http://www.halliburton.c.../2006/kbrnws_012406.html
Rumsfeld has already issued the warning when he said to America, "You better watch what you say,
watch what you do".
They've gotten away with EVERYTHING so far. They're not about to stop now.
Can anyone pretend that these people will allow the normal operation
of what we believe "the democratic system" to be after the crimes they have committed?
Events clearly show they cannot and it may be past time to think that they might be stopped by
activism within the "system".
WASHINGTON (AP) --- Nonlethal weapons such as high-power microwave devices should be used on
American citizens in crowd-control situations before being used on the battlefield, the Air Force secretary
said Tuesday.
The object is basically public relations. Domestic use would make it easier to avoid questions from
others about possible safety considerations, said Secretary Michael Wynne.
"If we're not willing to use it here against our fellow citizens,
then we should not be willing to use it in a wartime situation," said Wynne.
http://www.rawstory.com/....weapons.ap%2Findex.html
COMMENT #2 [Permalink]
...
Julia Davis
said on 9/13/2006 @ 5:10 pm PT...
It is totally incredible that they expect us to trust election officials when I have seen with my own eyes that we can not do it. I assisted in the recount of the 2004 election in Ohio and the election officials in that state did not even follow their own laws by allowing votes which the machines could not read to still be count by hand.
It is a state law, I did not create it, they did but the election officials refused to follow it even after I pointed it out to them so many votes were not counted. Therefore, these votes were throw out by elected officials. No, we can not trust them with our most important role as citizens nor should we.
COMMENT #3 [Permalink]
...
DIXIECRAT
said on 9/13/2006 @ 5:22 pm PT...
VOTE BY ABSENTEE BALLOT, CREATE A PAPER TRAIL AND COMPLETELY AVOID THE ELECTRONIC VOTING MACHINE MESS.
COMMENT #4 [Permalink]
...
Mark S
said on 9/13/2006 @ 5:45 pm PT...
When an elections official says, "Trust me," shoot first and ask questions later.
COMMENT #5 [Permalink]
...
Grizzly Bear Dancer
said on 9/13/2006 @ 5:46 pm PT...
sURPRISE - sURPRISE - sURPRISE!!!
COMMENT #6 [Permalink]
...
sorseress
said on 9/13/2006 @ 6:00 pm PT...
Gee, I'm so surprised....now if we could only get the various state officials who bought these *%*&%##)^ machines to admit that they a were either duped or complicit in wasting tax payers money.
COMMENT #7 [Permalink]
...
Floridiot
said on 9/13/2006 @ 6:01 pm PT...
Even if they didn't flip 3 (or whatever) out of 100 votes at the county (local machine) level, they could still do it between the county and state level tallys being reported
So to me, any computerized tabulation should be in question
Great reporting Brad
COMMENT #8 [Permalink]
...
JUDGE OF JUDGES
said on 9/13/2006 @ 6:27 pm PT...
Bed voting machines head to foot during sleepovers to prevent virus transmission . . .
COMMENT #9 [Permalink]
...
Agent99
said on 9/13/2006 @ 6:29 pm PT...
ROTFLMARO, JoJ!!!! 
COMMENT #10 [Permalink]
...
Hal Kinchen
said on 9/13/2006 @ 6:35 pm PT...
So, why don't we beat them at their own gam[e]?
COMMENT #11 [Permalink]
...
Robert
said on 9/13/2006 @ 7:12 pm PT...
#10 is right. Why not do as they have done to us. Hack every state. Surely there are patriotic geeks in every state with the ability and the intestinal fortitude to turn this " FIX " around in our favor. Hell, according to what I have read here on Bradblog, just about anyone in California can volunteer to take a voting machine home for a sleep-over. If I had any knowledge of computers at all, I would be doing what I could to reverse this corruption perpetrated by the Repugs. Thing is, here in my county in WV, we're still using lever machines with the old paper ballots. We're a little behind the times, but at least in most counties, we're honest. Can't say that about some of our bigger counties which have switched to ES&S, through the direction of our new Republican SOS, Betty Ireland. Repugs really want Senator Byrd out, and although he is polling at about 60% to 28% against Repug Raese, I just don't feel safe with these machines in Republican control.
COMMENT #12 [Permalink]
...
what now toons
said on 9/13/2006 @ 7:15 pm PT...
We have less than 60 days before the elections, we still have these machines to terrorize our democracy. The law suits coming, but the machines are still there. Time is running out, how can we scrap these technological terrors before it's too late?
Here's a link to my cartoon on the subject, don't expect funny, cause this problem is not funny at all.
http://www.whatnowtoons.com/#034
COMMENT #13 [Permalink]
...
oldturk
said on 9/13/2006 @ 7:22 pm PT...
Again thank-you for sharing this pertinent information with us. One more indication that these BLACK-BOX,.. JUNK-BOX electronic voting machines are not tamper proof as the vendors so soothingly lead us to believe,.. so erroneously. A dishonest person is readily capable of altering the tabulation of the vote count enabling them to change the outcome of an election. We need a system of counting the votes that lends itself to the primary focus of an accurate count,.. a result that has been tampered with or otherwise manipulated in disregard for the will of the voters is simply not acceptable,.. and should no longer be tolerated. Integrity and confidence is absent in the results derived from our elections processes as long as these vote counting computers are involved in this democratic exercise.
COMMENT #14 [Permalink]
...
Nana
said on 9/13/2006 @ 7:24 pm PT...
Well, there you have it, solid evidence that it can (was) done. Can I put my tin-foil hat away now?
Reasonable people do not ignore scientific evidence.
COMMENT #15 [Permalink]
...
Chris Hooten
said on 9/13/2006 @ 9:15 pm PT...
It's so sad that Ann Richards died. What a spunky lady. I loved watching her on politically incorrect and Real Time w/ B. Maher.
COMMENT #16 [Permalink]
...
Arry
said on 9/13/2006 @ 9:22 pm PT...
Question --- Is this the Diebold TSx touchscreen system or is that slightly different?
COMMENT #17 [Permalink]
...
skeptic94514
said on 9/13/2006 @ 10:07 pm PT...
If this hack is possible and the regulations stated below are allowed (sleepovers), the we must demand a full handcount in California.
Email from the Registrar in Constra Costa County. It states:
"Sending voting equipment and supplies home with poll workers is equally secure to the alternative approach of delivering equipment to poll sites in advance of the election where the chain of custody and security cannot be as easily documented or traced."
It looks like sleep overs are ok. See the full document below
California Association of
Clerks and Election Officials
ISSUE PAPER: VOTING EQUIPMENT “SLEEPOVER” PRACTICE
CALIFORNIA ASSOCIATION OF CLERKS AND ELECTION OFFICIALS (CACEO)
July 27, 2006
The reference to voting equipment “sleepover” refers to the practice of election officials distributing secured voting equipment to poll workers in advance of the election. In this model, voting equipment and all election supplies (including paper ballots) are stored at the home of lead poll workers (inspectors) and transported to the poll site on Election Day. Questions have been raised regarding the security and integrity of voting equipment under this practice.
Association Statement
The California Association of Clerks and Election Officials (CACEO) recognizes that distributing secured voting equipment to poll workers prior to Election Day is an efficient, accountable and transparent practice that contributes to the orderly and secure conduct of elections.
The following safeguards associated with this practice ensure that the integrity of the elections process is maintained:
All poll workers take an oath to uphold the integrity of the elections process prior to initiating their duties. Poll workers are essential to ensuring public accountability in the elections process. It is appropriate that they are entrusted with the security of voting equipment and supplies prior to and during the day of the election.
Poll workers are trained to confirm that voting equipment is sealed and that the tamper-evident seals are not broken prior to the opening of the polls on Election Day.
Lead poll workers (inspectors) are required to complete comprehensive training on all election processes which they are legally responsible for administering on Election Day.
Sending voting equipment and supplies home with poll workers is equally secure to the alternative approach of delivering equipment to poll sites in advance of the election where the chain of custody and security cannot be as easily documented or traced.
Memory cards, programming chips and other electronic data storage devices used to record votes are sealed within the voting equipment using tamper-evident seals prior to distribution.
Upon confirming that the seals are intact prior to opening the polls, the poll workers break the seals and run a zero report (or tape) to document and confirm that no votes have been cast or recorded on equipment prior to the first voter appearing at the poll site.
At the close of the polls, a results report (or tape) is run to show the number of ballots cast and votes recorded on the equipment. This report is maintained as part of the comprehensive audit and reconciliation processes associated with the canvassing and certification of the election.
California election law requires all voting systems to produce a physical representation of the ballot, either a paper ballot or a voter verified paper audit trail, which is used to validate vote results recorded on or by the voting system.
As a public and transparent process, elections in the United States historically rely on the checks and balances associated with appointing citizen poll workers to oversee the conduct at the polls. This practice is consistent with that model.
Officium Populi – Office of the People
OFFICERS 2004-2005
CONNY MCCORMACK
PRESIDENT
Los Angeles County
P.O. Box 1024
Norwalk, CA 90650
562-462-2716
cmccorma@rrcc.co.la.ca.us
STEPHEN WEIR
VICE PRESIDENT
Contra Costa County
KATHLEEN MORAN
TREASURER
Colusa County
REBECCA MARTINEZ
SECRETARY
Madera County
BOARD OF DIRECTORS
APPOINTED:
JANICE ATKINSON
Sonoma County
COLLEEN BAKER
Siskiyou County
DARLENE BLOOM
Orange County
CANDACE GRUBBS
Butte County
JOSEPH HOLLAND
Santa Barbara County
TIM JOHNSON
Tuolumne County
JOHN MCKIBBEN
Los Angeles County
MIKEL HAAS
San Diego County
DOLORES PROVENCIO
Imperial County
JOHN TUTEUR
Napa County
LARRY HERRERA*
City Clerk, Long Beach
*non-voting member
ELECTED:
JULIE BUSTAMANTE
Northern Area
Lassen County
JIM MCCAULEY
Mother Lode Area
Placer County
MICHAEL SMITH
Bay Area
Marin County
JULIE RODEWALD
Central Area
San Luis Obispo County
BARBARA DUNMORE
Southern Area
Orange County
ADVISORY COUNCIL
MARSHA WHARFF
Mendocino County
LEGISLATIVE COMMITTEES
CLERK OF THE BOARD:
VIOLET VARONA-LUKENS
Los Angeles County
COUNTY CLERK:
EEVE LEWIS
Sonoma County
COURTS:
PAT CHANDLER
Kern County
ELECTIONS:
JILL LAVINE
Sacramento County
DEBORAH SEILER
Solano County
COMMENT #18 [Permalink]
...
bvac
said on 9/13/2006 @ 10:17 pm PT...
All bradbloggers should create an account at digg.com and get the word out on this story..
link: here
COMMENT #19 [Permalink]
...
xargaw
said on 9/13/2006 @ 10:30 pm PT...
Diebold and others should be required to buy back every machine. They sold them as secure devices, which they are not. This is fraud. Officials are reluctant to critisize the machines because it makes them look stupid and incompetent for buying them. They need to tell the truth, that they were duped and demand a return with refund for the millions spend on these flawed machines. Every election in November should be on paper ballots across the country. Start printing now and count them by hand, if necessary, no matter how long it takes. Democracy that is slow is better than a criminal election.
COMMENT #20 [Permalink]
...
JUDGE OF JUDGES
said on 9/13/2006 @ 10:30 pm PT...
COMMENT #21 [Permalink]
...
whig
said on 9/13/2006 @ 10:53 pm PT...
Byland,
A reasonable administration that had no culpability for the events of 9/11 would have said immediately, do not panic, let our environmental protection agency determine whether it is safe and let our justice department and state and local officials take our time to go through the crime scene for evidence.
Wouldn't that have been better? But they had already sent rescue workers in and they were going to have health problems no matter what. Those who survived the collapse.
But there was no need, none whatsoever, to be sending in crews to clean up the debris and pave over everything, except to cover up whatever was there.
That is still presuming a reasonable administration. Even if George Bush and Dick Cheney were out to lunch, though, we'd have to assume somebody was making rational decisions in the federal government. Somebody would have said, hey, let's not bury this right away, unless there really was something to hide.
So I'm engaging in a little conspiratorial thinking. But I still have no conclusion because it does not reach a proof beyond a reasonable doubt for me. It reaches a strong accusation which deserves a full and fair public airing, however.
COMMENT #22 [Permalink]
...
Graham Clift
said on 9/13/2006 @ 10:58 pm PT...
Currently the Dems are 12% ahead of the Repugs in the polls. I hope that the invalidation of Diebold TS machines at this LATE stage is not going to invalidate the obvious retake of both houses that the Dems are currently on track to achieve. Always remember that the MM is controlled largely by the Neocons in this equation. This report grants them the ability to boost their side OR invalidate an election depending on the extent of the exit polls/vs actual vote differential. Around 6% differential is the max, only 1% beyond the minimum level of accuracy required by other countries!
Please, THINK. THINK REALLY CAREFULLY. The methodology of the power hungry cabal SUCCEEDS THROUGH CONFUSION TO OBSFUCATE FACTS. Most of the attacks against the 9/11 truth movement are based on this principle - Multiple improbabilities hides the probable through confusion: multiple NORAD repsonse times is the classic example.
The timing of this report is critical and must be followed by IMMEDIATE MACHINE REPLACEMENT to prevent an unprecedented disater. How likely is this to happen statewide before November? "Fooled again and again" will be the next 2007 book!
Maybe we'll call it "Irony 2006 election", the democratic election destroyed by democracy.
COMMENT #23 [Permalink]
...
MMIIXX
said on 9/14/2006 @ 12:43 am PT...
Guys ,stop calling America a "democracy" .
President Gore has more than one "Inconvenient Truth" that should be acknowledged ...
COMMENT #24 [Permalink]
...
Mark S
said on 9/14/2006 @ 1:51 am PT...
Brad, you have an excerpt from Democrat Rush Holt's speech above where he cites a Defense Department report that "noted that a total of 1,213 public officials had been federally charged with corruption in 2004, that 1,020 of them had been convicted of corruption, and that 419 cases remained pending."
This might explain not only the reason the voting machines can't tally votes correctly, but also the reason the Defense Dept. is missing a few trillion dollars.
Those numbers don't add up. 1,020 convicted, plus 419 cases still pending, doesn't add up to a total of 1,213 public officials.
Putting two and two together, it is obvious that neither the Defense Department nor Congress can put two and two together.
COMMENT #25 [Permalink]
...
STOP George
said on 9/14/2006 @ 2:12 am PT...
.
.
.
Here's the video at YouTube. Be sure to rate it and make it go viral, guys!
(click pic to rate vid at YouTube)
.
.
.
COMMENT #26 [Permalink]
...
STOP George
said on 9/14/2006 @ 2:13 am PT...
COMMENT #27 [Permalink]
...
phil
said on 9/14/2006 @ 4:13 am PT...
#10 and #11
If you crack these machines you are no better than your enemy. At that point you may have denied me the right to vote.
The answer is to get rid of all electronics, digitized data, and networks from our elections. It's an abuse of technology, and none of it can be validated because of the physics of electronics itself. It's not just the software that's vulnerable, it's every single component from point a to point b. All can be "specially crafted." It doesn't matter what whiz-bang new box they create, or the version of software. It's all no good.
I have been screaming (sometimes most vulgarly) this since I first learned of this issue in 2004.
What you want to do to replace this abusive technology, I am not entirely clear on. But it must be changed nationally because it has in effect destroyed everyone's constitutional right to vote.
Now if someone was to give me LEGAL access to any machine, or any part of the network, or data device. I could destroy it in 1 second. My point is it won't count right, and you can't validate it. This is the problem all down the line. Are you watching every single telephone pole, and vault down the line simultanously? Have you destructively reverse-engineered every memory card, every component, every eeprom, every circuitboard, every capacitor,, every power-supply. Who is to say that what your looking at e.g. chip number is what it say's it is, it could have been crafted at the doping level to hide logic. It could be entirely something else. There could be an rf receiver hidden in something that sets of a logic bomb. You will never know, and you can not validate it. What is going on is outragous. It's ciminal, and unconstitutional.
My personal opinion is that we need to use paper in the light of the day, with all parties present to count, and watch and store the paper for a hell of a lot more than two years.
Seems like that would be several trillions of dollars cheaper than the current system being used, not to mention all the lives that would have been saved, and civil rights.
We have terrorists in the world. But the real enemy is a domestic enemy right now. Nobody sees it, electricity is invisible.
COMMENT #28 [Permalink]
...
plunger
said on 9/14/2006 @ 4:52 am PT...
.
If the Dems fail to adopt this as their NUMBER ONE PRIORITY, we will know for a fact that the "Two Party System" is merely an illusion.
There should be NO electronic machines in use on election day in America.
Given the necessity of another Cheney-led False Flag attack on US shores in order to serve as the pretext for Martial Law, Bush will be happy to use this as an excuse to cancel all elections until further notice.
That's Fascism you smell.
.
COMMENT #29 [Permalink]
...
plunger
said on 9/14/2006 @ 4:56 am PT...
COMMENT #30 [Permalink]
...
alwaysfree
said on 9/14/2006 @ 5:36 am PT...
re #17:
email sent to Conny McCormack:
RE: Sleepovers
Would give the bank clerk your money to take home with them?
Think about it.
COMMENT #31 [Permalink]
...
happydance
said on 9/14/2006 @ 6:46 am PT...
If the Dems fail to adopt this as their NUMBER ONE PRIORITY, we will know for a fact that the "Two Party System" is merely an illusion.
Why should dems adopt this - even the so-called-liberal blogs won't talk about it (actually flame, ban, and delete it).
And this blog deletes and bans any talk about why the "superblogs" that proclaim to speak for "liberals" will not cover it?
Go figure - if this is as important and brad and gang say - why doesn't the blogosphere cover it?
Are they wrong for ignoring it (which we should then be allowed to discuss) or is brad just blowing smoke (not my opinion - just has to be one of the other).
COMMENT #32 [Permalink]
...
JonH
said on 9/14/2006 @ 6:49 am PT...
Regarding the idea of Democrats fighting fire with fire and rigging the vote in our favor, I think we should, but not in order to win. We should just make the outcomes all across the board so ridiculous as to have the machines and election results make our point for us. "Republicans win with 200% of the vote! 20,000 votes for the Republican candidate out of 10,000 total votes! Dems get 1 vote, wooohooo!!!"
It's going to be fubar'd regardless, so we might as well make it bad enough so that everyone has to agree that these machines are democracy killers.
Then, we can have another election, on the following SATURDAY, and do so with pencils and paper ballots.
COMMENT #33 [Permalink]
...
molly
said on 9/14/2006 @ 6:53 am PT...
#28 Plunger...Isn't it about time for RFK Jr.'s lawsuit to go to court? There was a 60 day waiting period. Look for another "hold" until after the elections. Maybe we should print this article out and send it to all the MSM outlets we can. That seems to be the only thing that has worked so far. Public awareness. Olympia Snowe is falling so fast in the polls...she is beatable up here in Maine. Her opponent isn't getting a penny from the democrats. Proof's in the behavior not the words.
COMMENT #34 [Permalink]
...
HopeSpringsATurtle
said on 9/14/2006 @ 6:54 am PT...
Brad...I just emailed this to Christy over at FDL. We need to post on this and spread it to the MSM.
THIS IS WAR!!!!
COMMENT #35 [Permalink]
...
Aaron S.
said on 9/14/2006 @ 7:38 am PT...
The report to congress about the 1000+ pulbic officials being convicted was issued by the Department of Justice, not the Department of Defense, which doesn't exist anymore anyway, remember?
Just FYI.
COMMENT #36 [Permalink]
...
big dan
said on 9/14/2006 @ 7:50 am PT...
I have been saying, for close to 2 years, that just to PROVE e-vote fraud, Dem operatives should hack into the machines. Or should I say, "anti-Republican" operatives...
COMMENT #37 [Permalink]
...
Rosencrantz
said on 9/14/2006 @ 8:07 am PT...
Okay, these flaws have to be intentional. I refuse to believe that voting machine companies are unable to make vote-counting machines that work properly and secure.
How hard can it honestly be? I mean, it's basically a calculator and flawless, hack-free calculator technology has been around for as long as I can remember.
There is no way I can even imagine this kind of incompetance without it being intentional.
COMMENT #38 [Permalink]
...
Joan
said on 9/14/2006 @ 8:27 am PT...
#31 Happydance,
"...And this blog deletes and bans any talk about why the "superblogs" that proclaim to speak for "liberals" will not cover it..."
I've read several posts on Bradblog that discuss this subject. They weren't deleted as far as I know.
I don't recall this blog ever deleting a post or banning someone for this reason. I've only seen disinformation & negative personal attacks deleted, and people have been banned for repeatedly breaking the few rules here.
Maybe you need to sit a few out. You sound a bit dizzy.
COMMENT #39 [Permalink]
...
KestrelBrighteyes
said on 9/14/2006 @ 8:29 am PT...
Anybody contacted Lou Dobbs about this yet?
I'm thinking a copy of this video should be sent to every single candidate BEFORE November. Sure a lot of them will ignore it - but a lot of them WON'T.
Wouldn't hurt to send some copies to CSPAN, NPR, and every local and national media outlet as well.
Any copyrights to be concerned about?
COMMENT #40 [Permalink]
...
JonH
said on 9/14/2006 @ 8:47 am PT...
COMMENT #37 [Permalink]
... Rosencrantz said on 9/14/2006 @ 8:07 am PT...
It could be that the companies really didn't try very hard to make the electronic voting machines secure, but I still don't think that a machine can be engineered or code can be, um, coded, that can't be hacked or manipulated.
I want to be able to fill out a paper ballot, insert it into the official "scanner/counting machine"myself to verify that it was read and counted properly, and then get a reciept for my vote.
Either that or just go back to all paper and pen ballots that are hand counted. I'd gladly wait a week or more for results I can trust.
COMMENT #41 [Permalink]
...
Rosencrantz
said on 9/14/2006 @ 9:36 am PT...
JonH:
I'm Canadian and all our elections are paper and pen style. Even during a National, Federal election, we have results by 10 or 11 pm that same night. It doesn't take a week...nor should it.
This is also a further cause of my confusion. In the time it takes to plan and program and learn these machines, then to fight with them, fight the media and voters rights groups, meet with voting companies for re-assurance, etc, etc, etc....you could probably hold dozens of federal elections on paper ballots.
COMMENT #42 [Permalink]
...
Hank McCann
said on 9/14/2006 @ 9:39 am PT...
The NY Times, Washington Post, Miami Herald, LA Times, etc---all the major newspapers, including TIME, NEWSWEEK, etc. need to be sent Youtube site and attach letters demanding that this news be covered. TIME TO PUT THE HEAT ON...
COMMENT #43 [Permalink]
...
phil
said on 9/14/2006 @ 9:42 am PT...
Who cares if some anti-voter rights bastard is rm -rf'd
We are talking about our votes and the time has ran out!
Were gonna be stuck with these cracked boxen!
Now what the fuck are you going to do about it?!
COMMENT #44 [Permalink]
...
Puddle Jumper
said on 9/14/2006 @ 10:06 am PT...
The underlying design of Diebold's program is not designed in any way shape or form to offer even the slightest bit of data safety. I remember when the story first broke and I explained to a fellow programmer their technical issues, he dismissed the story out of hand because he could not fathom how any program designed for something as critical as vote casting and counting could be put together so poorly. On the one hand it is hard to believe that the programming team was really that stupid and incompentent - especially since Diebold makes ATMs which require a great deal of security and accuracy. On the other hand, it seems to me if you want to secretly fix elections there would be many elegant and hard to detect ways to allow for that in a program do so with out making such a big obviouse.
It is really sad that this machines are in use. It is hard to believe that if they had actually been examined by a competent programmer prior to purchase, any of them would be in operation.
COMMENT #45 [Permalink]
...
HopeSpringsATurtle
said on 9/14/2006 @ 10:19 am PT...
Brad...I just posted on this at my site. I have contacts for Senate, Congress and CNN to make the mainstream media sit up and DO THEIR FUCKING JOB. I quoted you and linked your site. Thank you for NEVER dropping the ball on the voter fraud which is argueably the most important issue of our time. If we have institutional vote fraud our voices will never be heard again.
COMMENT #46 [Permalink]
...
STOP George
said on 9/14/2006 @ 11:37 am PT...
.
.
.
Diebold's rebuttal to this study is HERE.
Rebuts:
- this software they tested was 2 generations old.
- the computers are not networked.
Discuss...
.
.
.
COMMENT #47 [Permalink]
...
Miss P
said on 9/14/2006 @ 11:57 am PT...
I keep hearing, vote by absentee ballot. Let me just say, if you do then you won't be counted in the exit polls that we rely on, and at least here in Maryland they use the AccuVote Opscan for absentee ballot counting. We already know how easy they are to hack. And with absentee ballots, who's watching? Check your local procedures.
COMMENT #48 [Permalink]
...
BigJohn
said on 9/14/2006 @ 12:07 pm PT...
All bradbloggers should create an account at digg.com and get the word out on this story..
Yes, good idea - BUT WHY DO WE HAVE TO DO THIS? WHY DOES THE REST OF THE "ADVERTISE LIBERALLY GROUP" flame, delete,a nd ban dialog about this?
And why does talking about this silence get deleted and banned here?
COMMENT #49 [Permalink]
...
bvac
said on 9/14/2006 @ 12:25 pm PT...
Good fucking lord, shut the hell up about the advertise liberally crowd and DO SOMETHING ABOUT IT! LIKE DIGGING THE ARTICLE!
COMMENT #50 [Permalink]
...
Grizzly Bear Dancer
said on 9/14/2006 @ 12:29 pm PT...
Comment #20: Yeh bebe and the old boy could sing pretty well too.
Plunger: For all your in depth knowledge about a lot of 911 and Bushit administration criminal issues, i find it entirely interesting that you still suscribe to the idea that we have a 2 party system at work.
The quote Democratic majority in CONGRESS are REPUBLIDEM enablers installed minority party robots and if they put up Clinton as there poster spokes person, they will lose the Presidency again against any candidate even if their name is Benedict Arnold Bushit.
COMMENT #51 [Permalink]
...
des
said on 9/14/2006 @ 1:03 pm PT...
BigJohn #48 --- what are you talking about? there has been ZERO banning and ZERO deleting of posts here regarding the lack of coverage elsewhere. If someone has been banned or their posts deleted, it's because they violated the very few rules we have here. If you want to know why the other blogs have been afraid to cover this topic in the past, why don't you ask them???
BE THE MEDIA, dude. Spread the word to those who haven't heard yet. Or don't. It's up to you.
COMMENT #52 [Permalink]
...
Grizzly Bear Dancer
said on 9/14/2006 @ 1:04 pm PT...
Goes the same for Benedict Arnold KERRY. Nows he's gonna kick Swift Boat's ace because he ran out of da money during the campaign.
How much does it cost to speak into a MICROPHONE when you are the Demo Candidate for Presidency John???
Bushit enabler.
Did you get the back issue by Robert Kennedy Jr. about the stolen Ohio election???
Seems i recall you were pretty damn quiet when Blackwell's rigged recount that produced 285 additional votes for you. A recount you didn't spend one dime to help out Green Party candidate David Cobb or Independent candidate Michael Badnarik who asked for the recount although you had a warchest of money at your disposal. Motto on OH Dem website with your face: WILL COUNT EVERY VOTE. Sure...
I also saw a copy of an email that you sent out Senator which said you were not contesting the hijacked electoral votes from OH, FL, NM, or NV on January 6th,2005. YOU was in IIIIIIIIIIIraq.
Thank you Mr. Scull and Bonesman for a desire to stand up and kick some assss.
COMMENT #53 [Permalink]
...
BigJohn
said on 9/14/2006 @ 1:31 pm PT...
Good fucking lord, shut the hell up about the advertise liberally crowd and DO SOMETHING ABOUT IT! LIKE DIGGING THE ARTICLE!
I am - I REGULARLY DO! Just saying it gets deleted. Why is it considered "wrong" to talk about this? How can we spread the word when it gets ignored in MSM, both political parties, and even the "liberal" superblogs?
Why are you so hostile about this dialog?
COMMENT #54 [Permalink]
...
BigJohn
said on 9/14/2006 @ 1:33 pm PT...
... desm you are WRONG, but how would you know? Like I said - it gets deleted and banned. I would show you links to this, but, like, its been deleted, get it?
COMMENT #55 [Permalink]
...
Grizzly Bear Dancer
said on 9/14/2006 @ 1:37 pm PT...
Can Brad or Winter Patriot answer Big John poh-leez.
COMMENT #56 [Permalink]
...
Mark S
said on 9/14/2006 @ 1:43 pm PT...
#31 Happydance:
Among progressives, most of the superblogs are known as left gatekeeper sites. BradBlog is an exception and so is opednews.
A friend of mine was watching TV with his wife and he pointed out some lies on the news. His wife said, "If it wasn't true, it wouldn't be on TV."
There are still a few people with that mentality. But according to the recent Zogby poll, 92% of the American public believe that we have a right to free, fair, open elections, so even the brainwashed still care about democracy.
Getting the truth out when the right-wing controls the mass media (and the left gatekeeper sites, despite their progressive facade) isn't easy. Last year one of the supersites deleted any comments I made about election integrity. This year they permit such comments, but delete anything about 9/11 truth.
The two-party system is indeed an illusion. Democrats would never graciously concede to Republicans without a fight if they were truly opposed to Republican policies. Or continue to vote with the Republicans and further their policies after conceding to them.
My personal policy is that any party or candidate who doesn't care about my vote, won't get my vote, and I don't care if their opponent is Satan himself. Satan has been running the country for six years now, so I'm no longer terrorized at the thought of him in charge. And I'm downright tired of voting for the lesser devil, only to watch him graciously concede to Satan. Enough is enough! All my money and energy is now going into election integrity activities rather than to political campaigns. Before I can worry about who to vote for, I have to make sure that my vote will count.
COMMENT #57 [Permalink]
...
KestrelBrighteyes
said on 9/14/2006 @ 1:47 pm PT...
IF someone gets a wild hair and decides to turn the tables just to make a point....
Since Diebold is so all-fired sure that there's no problem with the machines, let's go for it! The BEST way to shake them up would be to have it zero out EVERY SINGLE VOTE TOTAL for Republicans - you know, the party for which Diebold promised to "deliver the vote" back in 2004? Don't mess with Democratic or any other vote totals, just the Republican. Any way to do that?
Of course, no one will believe that either of the two major political parties got zero votes, but when there's no way to verify the count, what choice do they have but to either fall back on the precedent they've already set - "the machines are secure enough" - or to publicly raise hell? Either way, the machines go down.
In the meantime, Congress can go ahead and swear in the Democrats, which will make the vote official even if it's not been certified, and investigations and impeachment proceedings can begin!
(Hey, I can dream can't I?)
COMMENT #58 [Permalink]
...
frogmarchbush
said on 9/14/2006 @ 1:52 pm PT...
Is there anyone (FEC?) that can show up on election day and perform a checksum test on these systems? Is there any random testing of machines to ensure that they're running the "approved" code?
COMMENT #59 [Permalink]
...
Grizzly Bear Dancer
said on 9/14/2006 @ 1:59 pm PT...
Before, during or AFTER undetected vote switching occurs altering votes without a verifiable paper trail???
COMMENT #60 [Permalink]
...
Bluebear2
said on 9/14/2006 @ 2:01 pm PT...
Big John #54
Here is but one example of negativity regarding KOS I have found by typing KOS in the Bradblog Search Pane near the upper right hand corner of this thread.
In fact, of the first 10 links that came up, 6 were negative. So I really don't know what you are talking about. There has been lots of talk here about how many of the so called progressive blogs are ignoring major issues or in fact degrading them.
Even the fact that you are still here bashing us would seem to disprove your allegations.
COMMENT #61 [Permalink]
...
Grizzly Bear Dancer
said on 9/14/2006 @ 2:12 pm PT...
Did you see the neo-con voting pill commercial.
Gets rid of any desire to question ANY election results. "Feel confident and put your trust in us."
Paid for office holdes held by U.S. Fascists.
Side effects may cause memory loss, stomach worms which will eat your gastro-intestinal tract, and a craving to re-elect George W. Bush one more time with Arnold Benedict Swartznigger as his new mate.
COMMENT #62 [Permalink]
...
larry
said on 9/14/2006 @ 2:14 pm PT...
COMMENT #63 [Permalink]
...
Brad
said on 9/14/2006 @ 2:15 pm PT...
There is absolutely nothing wrong with bashing the Liberal Advertising Network if you wish to. Presuming you follow the few rules for commenting here. Namely: Don't post under multiple user names, don't post (knowing) disinformation, don't personally attack other commenters, don't spam the comment threads over and over with identical off-topic posts/thoughts, etc.
Beyond that, we don't ban or moderate anyone here for content. Even content that I (or the admins) may disagree with.
Now that that's been said, I hope BigJohn (who has had several posts, incorrectly stating that we ban comments for content, and yet those comments were allowed to stay!) moves on to whatever interests him. As long as it follows the above guidelines.
COMMENT #64 [Permalink]
...
des
said on 9/14/2006 @ 2:34 pm PT...
maybe Bigjohn isn't following the posting instructions correctly, so his posts don't show up --- mistakenly believing they were 'deleted"...
COMMENT #65 [Permalink]
...
bvac
said on 9/14/2006 @ 2:44 pm PT...
BigJohn: Dialog? What dialog do you want to have? In recent weeks I've seen folks (or folk, there seems to be only one person doing it) showing up, bashing the "advertise liberally" crowd and disappearing. Examples:
https://bradblog.com/?p=3364#comment-104681
https://bradblog.com/?p=3325#comment-102660
https://bradblog.com/?p=3315#comment-102492
In each of those instances, our cyber-Paul Revere rides through the blog warning us of the threat posed by Advertising Liberally. In each, he compels bradblog to drop the Advertise Liberally banner, in one he rips into brad for posting photos from a conference. I asked him if it was brads participation in the conference that he took issue with, or just the article about it. No response, no dialog. It's clear that your circle wants to attack daily kos, firedoglake, crooks and liars et c. Fine, go do it. Start up your own blog and have at it. Trying to discuss these issues on daily kos is like going over to freerepublic to expose the crimes of the bush administration. Coming here to yell at people and criticize other sites isn't going to get you very far either.
COMMENT #66 [Permalink]
...
Agent99
said on 9/14/2006 @ 3:09 pm PT...
"BigJohn", under another name, came in bashing Advertize Liberally, and a bunch of other blogs... in fairly vivid terms.... Then kept it up, using identical, and nearly identical, terms on every popular thread he/she found, completely without regard to the subject of the thread. Then I realized some of the points made were disinformation, accusing Amato of deleting people's comments about election integrity, when I have made a number of them, and seen a number of them on Amato's blog. I know C&L deletes off-topic comments on certain threads, but there are plenty of open threads. I told "BigJohn" he/she was spreading disinformation, that this blog is not a vehicle for blog bashing campaigns and so cut it out. It kept up. I banned him/her for spamming and disinformation spreading.
He/she has changed names, email addresses, IPs, a number of times to keep wailing on other blogs and Advertize Liberally, always on popular threads, this one for instance, still trying to create his/her own megaphone. I have deleted some of these and/or answered some, and banned the new identities as they come along. If Brad wants to give this maniac a chance to quit spamming and lying, that is fine with me, but, if it keeps up... guess what!
[PS... Here's another example of the supposed non-coverage of election fraud issues and the supposed deleting of comments on this issue at one of the blogs he/she spam-bashes. Lookee here. --99]
COMMENT #67 [Permalink]
...
Bluebear2
said on 9/14/2006 @ 3:17 pm PT...
Even if the MSM isn't picking up on this story, at least one techie site has: ZDnet.com
has posted an article on their website. They let Diebold have the last word though!
I left a plug for Bradblog in their comment section!
COMMENT #68 [Permalink]
...
larry
said on 9/14/2006 @ 3:18 pm PT...
COMMENT #69 [Permalink]
...
wilywascal
said on 9/14/2006 @ 3:29 pm PT...
{Ed note: The following comment comes from a "professional". Remember our friend "Wally O'Diebold"? I'm leaving it up, however, so folks can see the "official" unofficial response from Diebold and friends. So take it with the grain of salt it's worth. As a sidenote, in reply to some of the obfuscation below, the memory cards in Diebold systems used are typically moved into "aggregator machines" at the end of the day, where viruses can then be spread to the rest of the system. As well, many jurisdictions have their machines hooked up to modems, as Maryland does for example, and they are vulnerable to spreading of viruses at that point, and many others. -BF}
First of all, I am of the opinion that all DRE’s MUST be decertified until it can be determined that DRE vulnerabilities are corrected and tested. Additionally, the design, coding and testing must all be open to review before recertification. The manufacturer should not be the one hiring the independent testing lab. Before use, proper safe practice procedures must be certified, as well, with adequate training of all election officials regarding those procedures a requirement. One very basic procedure is that these machines are never left unsecured (no sleepovers). DRE’s should not be able to record votes without properly functioning paper audit trails monitored in real time. Those were my beliefs even before this latest crack, because there was already ample evidence for the need that these requirements be met.
Nevertheless, I’d like to point out some apparent limitations to this crack. From watching the Princeton demonstration of the crack, the infected memory card must be passed among different machines. It does not appear to propagate itself from an infected machine to new or different memory cards. Why it couldn’t, I’m not sure, although I have some idea, but that isn’t what the video shows. Therefore, unless the virus was loaded separately on multiple memory cards, the only way of infecting other DRE’s is by using that same infected memory card. There does not appear any way for machines to pass malicious code directly otherwise amongst themselves, as they are not networked. (I’m wading through the technical report now, so somebody correct me here if I’m getting any of this wrong.)
However, I believe the guidelines for using DRE’s call for each memory card to be matched to a DRE, a typical common sense safe practice procedure which would prevent any malicious code from propagating itself into other machines. There is no real justification or reason for swapping these memory cards, anyway. If a memory card becomes defective or full, I believe the machine is presently taken out of service. Possibly, as a back-up, a new memory card in a sealed package could be freshly labeled for use with that DRE, formatted and loaded in preparation for that election. That way, voting delays could be avoided or minimized, or as a cost-effective, yet secure, means of reducing the number of extra DRE’s desired for that purpose. On the other hand, protocols probably do demand that DRE's be taken out of service until a complete inspection is done to rule out tampering and so that problems can be properly documented, analyzed, and corrected, even when it is reasonably certain fault lies with just the memory card.
It is my understanding these cards are formatted and loaded with ballot data in preparation for each election, and that this is done from a PC. This is done with proprietary software from Diebold and other vendors. There is no indication from the video that malicious code is passed to the PC and from there on to other memory cards being prepared. Moreover, any malicious code that had previously been on the memory card and not automatically erased by the malicious code itself to prevent detection after a previous election would be removed upon reformatting. Nor is there any indication that malicious code is passed to or through any tabulating device to another memory card.
Again, correct me if any of these particulars are mistaken. My knowledge of the procedures and workings of DRE's is admittedly limited, and election officials trained on DRE's could provide much more needed insight into actual current practices. The suppositions provided here are done so in the interest of determining the scope of the vulnerabilities of this particular crack.
It is likely that malicious code would erase itself from the DRE after an election to prevent detection. Although malicious code could be retained on an infected machine, it would have to be generically programmed for use in multiple elections, and it seems unlikely a cracker would want to take that increased risk of detection. It is not clear, either, whether or not any such code left on a DRE would become disabled or erased upon loading new data from the next elections memory card.
One possible limitation is that should DRE’s and their corresponding memory cards be separated or marked for consistent use in specific districts or individual polling stations, the risk of any contamination spreading is minimized. This may be handled differently in different places; but it is potentially a factor.
Another possible limitation of this crack is that anti-virus software specialized to detect malicious code on both memory cards and DRE’s could be developed to expose its presence, and that could quickly lead to charges against the cracker and/or accomplices. Particularly if a routine to virus scan all the memory cards at each polling station before they are ever inserted into their corresponding DRE’s is done in conjunction with a policy of always keeping the memory cards in a secure separate location from the corresponding DRE’s until election day. I believe the latter procedure is standard policy in some locations. At any rate, limiting access to the memory cards until needed would seem just plain common sense safe practice procedure. As is normal chain-of-custody records. It may be impractical to lock all DRE’s into a vault, but it is a simple matter to keep all the memory cards in a safe or safety deposit box with strictly limited access when not actively in use.
The Princeton study does not appear to make the claim that their malicious code could not be detected upon the memory card; the inference is that it escapes detection by erasing itself, which could only be after the memory card is inserted into the DRE and it installs itself. But it would be unable to achieve its advertised ability to propagate itself to other machines if it erased itself from the memory card.
It should also be possible to detect malicious code on the DRE itself, since it could not accomplish what it is intended to do if it erased itself before completing its task. This could be determined by testing for malicious code in actual run-time mode, instead of the test mode initially run. For example, after setting up the machines and testing, election officials set it to record actual votes. Then, entering in votes for various candidates, they could pull the memory card and compare its results to what was actually entered. If everything checks out, they could reformat or reset the memory card and either mark and initial any paper audit trail as test votes, or discard. Alternatively, possibly a substitute test memory card could be temporarily used between setting to voting mode and before actual voting.
Security patches will probably be created and installed on these and other machines in response to this latest revelation. Undoubtedly, present security protocols will be reexamined, and new ones implemented, possibly the virus scan mentioned. I don’t think that is nearly enough; they shouldn’t be used until all the conditions first set forth above have been met. Call me cynical, but I wouldn’t bet any money on a nationwide ban or refund, though.
Granted, the exposed vulnerability is a serious matter, no doubt about it. And Brad is performing a vital public service in helping bring people’s attention to the work done at Princeton and elsewhere in that regard. This particular article of Brad’s is an informative, comprehensive and scathing indictment of the DRE’s now used. But to retain credibility and avoid the appearance of bias, hyperbole, or undue alarmism, it is important to stay objective. Reporting the limitations of the threat or extent of the vulnerability would help accomplish that. Such objectivity need not detract from stressing the importance of immediately discontinuing the use of DRE’s until they can be reasonably ascertained by outside parties to be secure. I would have felt an obligation to make inquiries about—and subsequently report—vulnerability limitations. I would have also been extremely curious to know if this crack could have been made more malicious, and hence more capable of throwing an election. I would have been interested enough to know what Diebold now planned to do to ask them. Their response, or lack thereof, could have been reported. Ditto for election officials around the country.
To some extent, this crack of DRE’s is made possible in large part by not following common sense safe practices. Not following proper procedures with any voting method—not just with DRE’s—is a recipe for disaster. That should be emphasized as well if we are truly interested in securing integrity for the electoral process. Emphasis and focus should also always be squarely placed upon voting integrity. Such emphasis serves as further proof of objectivity. That is the big picture, and it can become counterproductive if there is too much obsession with punishing Diebold, DRE’s in general, or the partisan side of it, and we lose sight of that. Even where not true, care must be taken to avoid any appearance of such bias.
For what it’s worth, although I felt there were a few things that might have improved it, Brad’s article nevertheless gave a pretty fair assessment overall. And I trust Brad and others will be following up on some of these questions and issues in the near future.
COMMENT #70 [Permalink]
...
bvac
said on 9/14/2006 @ 4:25 pm PT...
Wily: my understanding is that the virus, once loaded onto a machine, can replicate and infect any memory card inserted thereafter. Should this virus find its way onto the central machine(s) responsible for programming the initial ballot data, it is plausible that every machine could be infected. There are any number of scenarios where machines can be infected on a widespread basis. Every time a security vulnerability is found, Diebold claims that their latest software is more secure than ever. It's fair enough to fall for that line the first time, but election officials should be onto their game by now. Remember the Ohio recount, when a Triad employee showed up, posted a cheat sheet on the wall, swapped out a few hard drives, and claimed all he was doing was fixing a battery? All it takes is a bit of social engineering, and someone could have access to a central tabulator, claiming they have to update the software. So the premise of trusting election officials and proper procedure to safeguard against gaping holes in security is a "shoot now, ask questions later" approach to the problem, and is inevitably going to lead to problems.
COMMENT #71 [Permalink]
...
Bluebear2
said on 9/14/2006 @ 5:12 pm PT...
Off Topic, but part of the problem:
Lawyer says FCC ordered study destroyed
"The Federal Communications Commission ordered its staff to destroy all copies of a draft study that suggested greater concentration of media ownership would hurt local TV news coverage, a former lawyer at the agency says."
COMMENT #72 [Permalink]
...
Robert Sawdey
said on 9/14/2006 @ 5:38 pm PT...
Mark S - you're incorrect saying the totals of fraud cases don't add up... you're comparing apples & oranges... consider that each official may have MORE THAN ONE CASE! Doesn't DeLay currently have 4? And Noe has 43 counts in state court alone!
WileyWascal - I understand your point of view, but as someone who's progammed for 38 years I've got to tell you you are out of your depth here... for the professionals, like the ACM (Association for Computing Machinery), we've know that computers are not appropriate for this use because they CAN NOT be secured, NO ONE can look at one and tell if it's doing what it should. The ACM has warned about this for nearly 20 years. Some technical flaws in your logic... there are TWO memory card slots on each machine, usually one sits empty... but EITHER can perform an 'update' of the system software in minutes... and then the code resides in the battery backed memory of the machine. The machines ARE often networked as authorities update all machines operating software at the same time. While you're correct that a memory card can't usually infect a PC used to program it, the PC can easily infect all memory cards it's configuring. Security patches are NOT sent out, it's not legal to change the software without the revised software being revalidated by authorities. Diebold's response to our compaints of 'you can't prove it's secure' is 'you can't prove fraud' - and that is a major issue... there's no way to prove these types of exploits ever did OR didn't occur! There is even a known case where a central tabulator PC was connected to the Internet so a Diebold operative could provide 'support & maintenance' DURING AN ELECTION! For lots of details on the problems & discussions of what can or can't be done about it, visit www.blackboxvoting.org - I love their video of a CHIMP hacking a Diebold central tabulator...
As to the early question if the TS was the same model as the TSx, no it's not... the TS is an earlier model, but it's been show the VAST majority of vulnerabilities still exist in the newer model.
COMMENT #73 [Permalink]
...
Vulture Man
said on 9/14/2006 @ 5:50 pm PT...
Byland COMMENT #1
You da man. Be very afraid folks. The prophet speaks.
Don't get caught with your pants down.
ALTHOUGH i DISAGREE WITH GET CLOSE TO LOCAL AUTHORITIES. tHOSE BASTARDS ARE GOING DOWN TO.
COMMENT #74 [Permalink]
...
Sally
said on 9/14/2006 @ 6:27 pm PT...
#72 Robert Sawdey
That was a very informative post! Do you have a website or article about the real specifics of these e-voting machines.
COMMENT #75 [Permalink]
...
alwaysfree
said on 9/14/2006 @ 6:30 pm PT...
Following is my email exchange with Conny McCormack, president of the The California Association of Clerks and Election Officials
September 14, 2006
Subject: regarding sleepovers
from me to Conny:
Would you give the bank clerk your money to take home with them?
Think about it.
from Conny to me (asterisks indicate my responses):
To continue your analogy, would you rather drop the money off at a location (polling place) and just leave it there unattended for several days/nights before the election? This is what happens when voting equipment is delivered to polling places in advance of an election comparerd with delivery to pollworkers who take an oath
***Tom Delay took an oath. Duke Cunningham took an oath. Bob Noe took an oath. Kenneth Blackwell took an oath.
Your own Tony Anchundo took an oath.
Oaths mean nothing, absolutely nothing, to criminals who believe they are justified in what they are doing.
Vote counting is an auditing procedure. Oaths and trust have nothing whatsoever to do with it.
and are a part of the process of known chain of custody of voting equipment, ballots and supplies.
***When machines can be tampered with, and fraudulent viruses introduced, with absolutely no trace that anything untoward has occurred, the question of "chain of custody" never comes up.
http://itpolicy.princeton.edu/voting/videos.html
Pollworkers have always had possession of the BALLOTS at their homes for days before every election.
***Did they have the ballot boxes??
Paper is different. You can see it. You can see someone stuffing a ballot box.
Stuffing a ballot box is small in the scale of its effect. Computer hacking can influence millions of votes with one action.
The election equipment that will be used at the 5,028 voting precincts in L.A. County on Nov. 7, 2006 is all a part of the PAPER ballot voting system, InkaVote Plus. All of the InkaVote ballots cast at each precinct have always been, and will continue to be, reconciled against the number of voters' signatures in the precinct rosters along with a further reconciliation of unusesd ballots at each precinct. All of this reconciliation process is open to public inspection and observation both at the voting locations after the polls close on election night and also at our headquarters in Norwalk during the period of the official canvass in the days/weeks after the election prior to certification of official results when we conduct a complete audit of each precinct's ballots, # of voters' signatures, etc.
***You are (deliberately?) missing the point. It's not the paper ballots where the tampering is likely to occur. It is the feeding of them into the black box tabulating system that turns over control of the results to persons and parties unknown.
I hope this information will help you to be more knowledgeable about the process and the meticulous checks and balances that go into it.
***Don't patronize me. I'll go head to head with you on "knowledge" at any venue you choose.
It is time the public officials all across the country who allowed themselves to be duped by a ruthless group of profiteers and criminals admit their mistake, file a massive class action suit, and begin taking some real personal care and concern about the accurate outcome of our elections. The time for protecting your pride is past: the public is way, way ahead of you.
http://www.wtopnews.com/...909548&comments=true
from Conny to me (asterisks indicate my responses):
Repeat: we have a paper ballot voting system in L.A. County. It is completely recountable by hand.
***Given the facts of events over the last two years, nationwide, those paper ballots will never, ever be examined by anyone, much less counted in toto.
The computer count, which can't be presumed to be accurate, will stand.
People will be sworn into office before the computer count is even certified, as was Bilbray.
When elections are meaningless, we have descended into tyranny.
You are not addressing the issues I, and others a lot smarter than I, have raised, and that is destroying our democracy and our country.
k
As I have a major election to conduct for the largest electoral jurisdiction in the U.S. in less than 8 weeks, I'm going back to preparing for that event now in order to insure the 3.8 million voters in our County receive legal and appropriate public service. This will conclude my responses to your emails.
COMMENT #76 [Permalink]
...
Grizzly Bear Dancer
said on 9/14/2006 @ 6:34 pm PT...
Thank you #72.
50 ways to leave your lover.
Could be re-sung 50 ways to rig an E-Election.
Back near the top someone took the pirate attitude of why don't we steal the votes for arrrrrh man? Years ago i saw a movie called Hackers. The only good part was the fact that these kids were so inventive at hacking into computers. So when it comes to hacking the vote, why not pirate our way into electronic voting computers and make say Green party candidate DAVID COBB (granted he planned to run again) AS PRESIDENT? Bush proclaimed himself kING in the last 2 and look where America is today? WE got World Crisis from 9/10 angles.
The argument that we can't because it's not a Democratic election then in 2006 Bush Fascist America is about as thick a fabric as that worn by a strip club stripper.
Bottom line is 22 U.S. states DO NOT even have a verifiable paper trail for their e-voting machines and if there are 50 ways for 1 person to change the outcome today, there's another 50 more which haven't been discovered yet. Don't kid yourself these neo-con bastard terrorists are SMART criminals and preservation at the top is key.
How many Democrats/Republicans in the House of Representatives or the Senate (because we don't want to leave these Congresssional robots out either) stood up to disagree with the Dennis Hastert swearing in of Brian Bilbray under the circumstance known about this election at ANY POINT after the facts surrounding Judge Yuri Hoffman's decision were revealed?
Claiming no expertise in law or laws which govern the Legislative branch, there can be a reasons outside the swore duty as AMERICANs representing us "the people" why NO OUTRAGE OCCURED WHICH WOULD HAVE BEEN THE PROPER RESPONSE to another obvious theft of U.S. Democracy by the Bushit administration.
But Noooooooooooooooooooooh!!!
MY POINT: i'm for democracy. If we had DEMOCRACY, DEMOCRATS WOULD BE UP IN ARMS DECLARING WE NEED TO USE PAPER BALLOTS IN NOVEMBER.
THIS HAS NOT HAPPENED PIRATES AND WHEN EYE SEAS IT AYES BELIEVES IT. RRRRRRRRrrrrrrrrrrrr
COMMENT #77 [Permalink]
...
Chris Hooten
said on 9/14/2006 @ 7:05 pm PT...
#76 If all domestic calls can be monitored (which they can and are, I don't care what you say), what's to keep them from *manipulating* the central tabulator data, by modifying or injecting their own data during the phone call that downloads the data. (heck, what is to keep them from blocking the correct call, and making their own with falsified results?) That is, have one computer "apparently" tabulating the votes from the machines, giving all the proper responses to the input, while a completely different machine uploads *different* data to the central tabulator. This is more than possible with current technology. I think the phone system itself could be a problem when using any computerized vote counter.
Hand counted paper ballots!!
COMMENT #78 [Permalink]
...
Chris Hooten
said on 9/14/2006 @ 7:07 pm PT...
BTW, I don't think Grizz has ever tried to suggest that domestic calls are not monitored, and that comment was not directed at him/her.
COMMENT #79 [Permalink]
...
larry
said on 9/14/2006 @ 7:10 pm PT...
COMMENT #80 [Permalink]
...
Brad
said on 9/14/2006 @ 7:20 pm PT...
Thanks for sharing that conversation AlwaysFree (#69).
Beware Wilywascal's comment (#64).
COMMENT #81 [Permalink]
...
Lisa B
said on 9/14/2006 @ 7:38 pm PT...
Sanchos, is a good man, I saw him at one of Greg Palast’s events when he was promoting his book. Diebold is evil they know what they’re doing. They know they could give us a paper trail very easily because they do it for ATM’s. If they wanted to put an end to all this they would supply everyone with two little pieces of paper after they voted and people could drop one in a box at the voting place and the other they could take home just incase they steal the box. So now what do we do? How in the hell do I get my vote to COUNT for the guy I vote for? This is freakin crazy.
Great report. Thanks.
COMMENT #82 [Permalink]
...
bvac
said on 9/14/2006 @ 8:31 pm PT...
Beware Wilywascal's comment
I feel dirty all of a sudden
COMMENT #83 [Permalink]
...
Freeyourcrt
said on 9/14/2006 @ 9:01 pm PT...
This just goes to show you how quickly we can go from democracy to demonocracy. The USA is a constitutional republic first and foremost and with good reason. I would put my trust behind the Bill of Rights before Diebold any day.
COMMENT #84 [Permalink]
...
wilywascal
said on 9/14/2006 @ 9:06 pm PT...
Followup to #69
A study of the full Princeton report gives a better perspective of the dangers and vulnerabilities, as well as possible limitations. Many of the suppositions given turned out to be correct, some key ones turned out to be erroneous. Some of the processes for DRE’s and memory cards in an election are not detailed enough in the report to make other determinations. Other possibilities for evading detection were detailed in the report. Some key findings:
Paper audit trails (VVPAT) expose vote stealing with this crack. Obviously, VVPAT is not equipped for detecting Denial of Service attacks from this crack, but presumably, once the machine became inoperable, it is subsequently removed from service, anyway. The report does not specify if DoS cracks are therefore then susceptible to detection by other means, but the logical assumption is that is likely.
Malicious code can be written onto another memory card, vastly increasing chances for the virus to widely propagate itself.
Malicious code could erase itself from the memory card as well as the machine in order to avoid detection.
Some of the report’s findings appear contradictory. Memory cards with the malicious code upon it are used for propagation, but this also makes the code vulnerable to detection.
Malicious code can be written from an infected DRE onto a memory card containing software updates for that DRE. The report is a little vague, but it appears certain that the malicious code could then subsequently be passed to a large number of other DRE’s and their memory cards, allowing a large population of DRE’s to become quickly infected with the virus. The likely installation of software updates from only one or several memory cards would appears to make them the most likely carrier of the virus and pose the greatest threat of widespread contamination.
All software updates are affected: bootloader, OS, and application. Apparently, only bootloader updates are not installed, but simulated to prevent detection; this is to prevent the virus, residing in the DRE bootloader sector, from being overwritten.
Once a DRE is infected, the only way of assuring that malicious code is removed is through installation of a special EPROM chip in place of the EPROM chip present. Every DRE suspected of infection would have to have the special EPROM chip installed and subsequently removed after rebooting to clear and reload flash memory. Without a patch, disinfected DRE’s are still vulnerable.
Tabulation of votes can be done through a PC or a single DRE, where all other memory cards are sequentially loaded to obtain a total. This could apparently propagate malicious code, if it had not deleted itself after voting is terminated on the originating DRE’s to avoid detection. This possibility is not discussed in the report, however.
Testing is now all that is required for certification, but only thorough analysis of hardware and software is able to detect different security flaws and vulnerabilities.
With the system architecture on the pre-2005 Diebold Accu-VoteTS used, it may be impossible to detect unauthorized modifications to the system software. This is a requirement under 2005 guidelines for certification, which, according to the report, are not mandatory, at any rate. Confused? I think this means that States may use these guidelines to set mandatory requirements.
Safe practices are emphasized in the report. Oddly, although recommended in the ESI report to Cuyahoga County, Ohio, no mention is made of strict pairing of memory cards to DRE’s in this report.
In the conclusion of this report, the authors state in part that,
“Nevertheless, the practical question facing public officials is whether DREs provide better security than other election technologies, which have their own history of failure and fraud. DREs may resist small-scale fraud as well as, or better than, older voting technologies; but DREs are much more vulnerable to large-scale fraud.”
#72 – I’ve done my share of programming, and spent many a late-night hour examining hex dumps after a full day. I knew about the two memory slots. It appears the other one can only be accessed from inside the machine. Is that correct? According to BlackBoxVoting, they don’t know what the second slot is used for. I’ve seen many of the videos, but I missed the chimp. The Princeton report didn’t have much to say about spreading malicious code via the PC, although they did compare the vulnerabilities of DRE’s to PC’s, and I have been curious about that. Seems like the easiest way to insert a virus. The Princeton report doesn’t have much to say on that topic. Any links about vulnerabilities between DRE’s and PC’s would be appreciated. I know about the ‘support and maintenance’ issues during voting, and I agree; that is plainly just as stupid as you can get. Your response, however, indicates you don’t understand my point of view.
#70—I agree.
COMMENT #85 [Permalink]
...
wilywascal
said on 9/14/2006 @ 11:11 pm PT...
The Princeton report doesn't offer much hope for the 2006 election. Kind of a 'damned if you do, damned if you don't' prognosis. At this point in the game, it appears many districts may well be forced to applying whatever fixes they can to DRE's and crossing their fingers, as for many, there isn't enough time to revert back to former methods.
After 9/11, and even before, we have been trading rights like privacy, due process, etc. for things like convenience and security. With the push towards DRE's, I think we have been trading convenience and false promises for the security and integrity of our electoral process.
Diebold and other manufacturers deserve their share of blame for shoddy products and practices. As Brad pointed out, their rush to make a profit exceeded their sense of responsibility to the public on a vital component of our democracy. But it should also be seen that government at all levels deserves as much, or more blame. They rushed to purchase new technologies without bothering to fully understand what they were getting into, and without making sure adequate safeguards were put into place and maintained. They have repeatedly ignored the input of concerned citizens and experts. Politicians from the local level on up from all across the political spectrum also abdicated their responsibility to the public they purportedly serve. I expect some social responsibility from corporations, but I expect much more from our public servants.
DRE's are just one symptom of the disease, however. Other than a small minority of principled elected officials, like Russ Feingold, few are serious about reforming our electoral process in any meaningful way.
COMMENT #86 [Permalink]
...
wilywascal
said on 9/15/2006 @ 12:26 am PT...
Brad,
There has been some kind of serious mistake. I have been accused of being someone else and blocked from posting comments to your blog. I had just sent you an email the other day about concerns I had on another article and some of the comments there. If you look at that email and all the comments I have posted to date, I think you will agree that the moderator had no justification for rushing to make the judgment they did. Here is the comment posted over one of my postings:
{Ed note: The following comment comes from a "professional". Remember our friend "Wally O'Diebold"? I'm leaving it up, however, so folks can see the "official" unofficial response from Diebold and friends. So take it with the grain of salt it's worth. As a sidenote, in reply to some of the obfuscation below, the memory cards in Diebold systems used are typically moved into "aggregator machines" at the end of the day, where viruses can then be spread to the rest of the system. As well, many jurisdictions have their machines hooked up to modems, as Maryland does for example, and they are vulnerable to spreading of viruses at that point, and many others. -BF}
I can assure you, I am no "professional". I have no connection to Diebold whatsoever. In fact, as can clearly be seen from my postings, I am opposed to them. The posting this referred to, #69, was done before a full reading of the Princeton report, and was followed up by another posting, #84, which admitted error and corrected those misunderstandings. Admittedly, #69 was posted prematurely, but it also presented itself as supposition, told that I was still reading the report, and requested that other posters correct any mistaken impressions regarding the scope of the vulnerability. Posting #84 does not misrepresent the report, and was labeled as a followup to #69. In fact, #84 noted the same thing about tabulating all DRE's into one as did the moderator above. So why leave #69 and delete #84? Numerous postings to this blog, including #69, expressed my unqualified support for decertifying all DRE's and discontinuing their use until they can be made secure. #69 concluded by saying that I thought your article was a fair assessment overall. Does that sound like someone working for Diebold? None of that makes any logical sense. It feels kind of like I'm being unjustly discredited because of my views, which really aren't much different than those expressed on your blog. I realize their are people out their getting paid to shill. I am not one of them, and that should have been obvious from my postings. This is a case of senseless paranoia run amok. Isn't that what Bush and those around him are trying to sell the public?
If you need something from me, a phone number, whatever, let me know. I think it only fair to be given a chance to clear up this misconception.
COMMENT #87 [Permalink]
...
BOB YOUNG
said on 9/15/2006 @ 3:33 am PT...
#72 ROBERT SAWDEY
“we've know that computers are not appropriate for this use because they CAN NOT be secured, NO ONE can look at one and tell if it's doing what it should.”
Because what you say is true pre testing the computers can never be the answer to the problems we have been having with the computers being used to “count” our votes. That does not lead me to the conclusion that computers can not be used in honest elections. Here is how computers could be reliably implemented in our elections if only everybody out there really wanted honest elections:
Neither hand counted paper ballots nor EVM’s (Electronoc Voting Machines) with verified paper trails are the answer to the vote counting problems we have had in our recent elections. Even if all voters were to verify a paper trail those in control of the EVMs can replace that “verified” paper trail with one that matches the “results” they chose to arrive at. We thus still have to trust those who have access to the paper trail until the results are finally certified.
The correct answer to eliminate vote fraud is verified voting. That would solve our problems. Everybody associated with our elections wants to test the EVM’s prior to elections, test them after the elections or eliminate their use altogether. None of these options will likely result in verifiable election “results”. The only time our votes need to be counted correctly is during our elections. So why not verify that our votes are being counted correctly during our elections? If we can do this we then have a correct answer to the problems we are having with fraudulent election “results”.
As they are used now EVM’s are a big part of the problem. That is so because the corrupt people who control our elections are taking advantage of the weaknesses of the EVM’s rather than taking advantage of their strengths. We are already using EVM’s that can memorize every vote cast. Why not have them remember where that vote came from as well? They can very easily do so if we want them to. Then everybody could check to see that their vote was really and truly counted as cast. For the purpose of keeping the vote secret every voter could be given a uniquely numbered receipt of their selections. A second copy of that uniquely numbered ballot could be securely stored by each precinct in case a recount was needed. Before leaving the polling place the voter could verify that the receipts were both correct. The machine could easily order all the ballots it memorized in order of the unique numbers they were assigned. It could publish that list on the internet and elsewhere so that those who want to know if there votes were counted as cast could check and see if they were. If nobody can find any discrepancies the votes were clearly counted as cast. If we also insure that extra ballots were not added to control the “results”, then we arrive at verified voting. That is somewhere that we may never have visited before.
There should rarely be any errors found if the EVM’s are really trying to get the count correct. Therefore if any candidate can demonstrate that there is less than 99.9% accuracy in the published list a recount is clearly required. The EVM’s have clearly failed badly if this does happen anyway. Therefore, the cost of a hand count of the receipts the precinct secured must be covered by the company that contracted the counting. The outcome of this monitored recount determines the winner of the election.
It is not that difficult to get to where we want to go if verified voting is our goal. The big problem we have left to solve is that those who have been controlling the outcomes of our elections don’t want to venture anywhere near verified voting.
The Wally O'Diebold’s of this world clearly do not want to venture anywhere near verified voting!
COMMENT #88 [Permalink]
...
MMIIXX
said on 9/15/2006 @ 4:08 am PT...
COMMENT #89 [Permalink]
...
bvac
said on 9/15/2006 @ 12:18 pm PT...
Agent 99: Read the top of post #69
COMMENT #90 [Permalink]
...
Agent99
said on 9/15/2006 @ 12:39 pm PT...
Thanks, bvac, I did.... Brad is handling it.... Oh, never mind, he's too slow.... I fixed it.
COMMENT #91 [Permalink]
...
bvac
said on 9/15/2006 @ 12:58 pm PT...
I'd like to point out that BigJohn has not come back to continue the dialog he desires. Is anyone surprised?
COMMENT #92 [Permalink]
...
JUDGE OF JUDGES
said on 9/15/2006 @ 9:53 pm PT...
COMMENT #93 [Permalink]
...
Larry Bergan
said on 9/16/2006 @ 3:17 am PT...
alwaysfree #75
Interesting conversation. It's always surprising when the officials answer back, but they are always very guarded in what they say. I wonder if they wish the systems really were secure, so they could have a sincere exchange or if they don't care and think it's funny. I guess there's the possibility that some of them actually believe what they say, but I doubt that last one!
Thanks for sharing!
COMMENT #94 [Permalink]
...
Larry Bergan
said on 9/16/2006 @ 3:23 am PT...
Hope a lot of newcomer's read your excellent recap of the multi tiered malaise Brad!
COMMENT #95 [Permalink]
...
wilywascal
said on 9/16/2006 @ 2:22 pm PT...
RE#87
Found your Silent Majority quite interesting, Bob.
I've had some ideas along those same lines as yours; 'trust, but verify'. It pertained to online voting, but perhaps the mechanics could be applied to any form of voting. Similar to what you said, you get a unique number that corresponds to the ballot. Except, all the unique numbers are posted online by district, county, state. Since the unique numbers can't be personally identified to you, they display how that ballot was voted. Visiting the web site, privacy is maintained because it can't be determined which unique number you are checking—if any—since all the votes for your voting district or precinct are listed. You can verify that your ballot was recorded correctly. Anyone can independently tally the totals in any category for any candidate or issue, comparing them to both the totals provided and published figures for the outcome. This might eliminate the need for costly recounts. If votes are not recorded, or not recorded correctly, this may enable voters and election officials to rectify the problem. Absentee ballots could also receive unique numbers.
Attempts to change or delete votes to throw an election could not succeed, because voters would take notice if their votes weren't being recorded or recorded correctly. Just as it is the citizens responsibility to vote, it would be their responsibility to verify. Even if, as seems likely, mostly votes on the losing side get verified, that would still serve its purpose. Normal measures to prevent ballot box stuffing would be employed, and the number of unique numbers issued should correlate to the number of ballots issued. Perhaps it is possible to use or configure unique numbers in such a way as to serve as an auxiliary security measure to protect against adding votes. Attempts to crack sites would be pointless because votes and tallies are only posted there from the source for verification. Changing web pages couldn’t actually affect anything, and any corrupted pages would just be reloaded. Online data base integrity could be maintained by periodic comparisons to the source backup.
Possibly, an algorithm could be used to create unique numbers containing all the ballot data. This unique number could then be scanned by a device before leaving the polling place as immediate visual proof the ballot was correctly recorded. That would enhance accuracy and help to prevent disputes later. All data could be verified by using the same algorithm and applying it to the unique numbers. The algorithm would be placed in the public domain to insure the integrity of the process. You might be able to go to an independent site and punch in your unique number to produce a facsimile of your voted ballot; or you might download a small utility. Mathematicians can best determine the feasibility of all that, but I think it could work. Perhaps just a simple algorithm used in conjunction with a interchangeable ballot data base would suffice. Even should algorithmic unique numbers prove feasible, a vital component would still be visual verification using the online data base of votes.
It seems such a scheme could be adaptable to any vote—small or large, propositions or presidential elections. It would add a strong auxiliary layer of security. Problems could be more quickly identified and corrected. The complete breakdown of voting might serve as a public historical electoral record; a resource that could be easily accessed online by anyone for analysis. Best of all, it would offer voters a feature they have never had—a way to independently confirm that their votes actually were counted as intended. That sure would have inspired more confidence back in 2000 and 2004. And, as the DRE vulnerability demonstrates, what good to know if your vote counted if you can’t tell if your vote has been stolen? Regardless of how transparent each step in the voting process is made or might be, if in the end the results aren’t transparent to the voter, it can’t fairly be said transparency is achieved. Whatever one's political affiliation, such a scheme would likely make the voting process more democratic and participatory.
I can’t say what the expense or time involved to implement such a scheme might be. Those might be offset somewhat by its benefits and integration. Presumably storage space for individual ballot data would be recycled after the vote can no longer be contested, leaving just the totals breakdown, as that data would become superfluous. Another potential problem might be posting data online in a timely manner. Perhaps algorithmic unique numbers and/or integration could help facilitate that. In sum, I am unqualified to determine how feasible such a scheme might be; it is offered primarily to inspire ideas and give pause for thought.
COMMENT #96 [Permalink]
...
wilywascal
said on 9/16/2006 @ 2:48 pm PT...
#92-Judge of Judges
Judge yourself. Instead of using innuendo, try logic. Instead of submitting to hysteria, try reason. How does wanting to shut down DRE’s and speculation on the scope of the vulnerability in any way equate to being a shill? Check out what happens to the neighbor in the Rod Serling clip towards the end of this.
COMMENT #97 [Permalink]
...
JUDGE OF JUDGES
said on 9/17/2006 @ 3:49 am PT...
The only way electronic voting can ever work is with 100% current
published source code of all internal devices ahead of time.
Agreed encription by parties
Publish all current hardware documentation.
Real time Registries at both party headquarter.
Multipal real time Remote registries.
Constant and numerous automatic cross checking of
registries by an agreed independant parties.
Real time feedback at each and every machine of a vote registered.
Multipal hard records of every vote cast with an individual serial id #.
Mutually exclucive redundant data pathways to and from machines and registries.
NO open air optics (IR) or RF links.
Complete 100% paper trails with recipts.
I don't think that asking too much . . .
COMMENT #98 [Permalink]
...
czaragorn
said on 9/17/2006 @ 5:51 am PT...
Why not just count the damn ballots by hand, in public, the first time, saving lots of money, eliminating all doubt? These idiots arte probably letting their teeth rot out while they wait for computerized toothbrushes! Disgusting!
COMMENT #99 [Permalink]
...
Barbara Bellows-TerraNova
said on 9/17/2006 @ 1:28 pm PT...
Brad, I'm sorry to see that the excellent article you've written here fails to mention Bruce Funk, our Emery County Clerk whose questions brought about the Hursti Report you do bring up, and which the Princeton fellows reference in their own report.
Just two weeks ago, Avi Rubin was on NPR's Diane Rehm Show. I called in and related the story of Bruce Funk, including the airplane swooping in from Salt Lake City with both Diebold officials and officials from the Lt. Governor's office, the closed-door meeting, and Bruce's subsequent strong-arming out of office --- to make sure listeners understand the nature of the Diebold when it thinks it can get away with it.
Mr. Rubin was good enough to confirm the validity of the Hursti information, and then pointed out that the story I related should cause Diane's listeners to feel a chill up their spines at the intimidation practices of Diebold and their connections in many a partisan election official.
Bruce should not be forgotten. He remains an American hero who is still being punished for his efforts. Just last week, a hearing at the State Archives to get the transcript or audio tape of the illegal closed-door hearing of the Emery County Commissioners with Diebold and State elections officials in late March, ruled against him, while accepting a 44 page affadavit from the County Commissioners slamming Bruce for his "incompetence" --- a strange complaint for a man elected to serve for 23 years before being ousted.
I am grateful for the Princeton report and video. At this point in the game it seems like it might be the only way to demand attention be paid to this horrific problem of Diebold hackability.
COMMENT #100 [Permalink]
...
bvac
said on 9/17/2006 @ 4:43 pm PT...
I for one welcome our electronic voting overlords.
COMMENT #101 [Permalink]
...
wilywascal
said on 9/17/2006 @ 10:21 pm PT...
RE-#97
I think those are generally desirable objectives.
However, unless you are advocating an open source OS, Microsoft might take exception to publishing proprietary copyrighted source code of their OS. I believe one of the DRE vulnerabilities involves manipulation through the database manager, JET, present on all MS OS, including CE. I have suggested going to an open source OS, for two reasons: transparency, and it better represents the ideals of democracy.
Irrespective of the OS, why not make the application software open source? Wouldn't publishing proprietary software amount to pretty much the same thing?
You reference 'both parties' for having real time registries. What about others who may be present on a ballot?
COMMENT #102 [Permalink]
...
JUDGE OF JUDGES
said on 9/18/2006 @ 1:00 am PT...
re- #97/101
Is a simplified basic example of a system WITHOUT
details, only to highlight a few concepts.
All parties would have their own redundant registries.
Why use M.S OS ? & yes every thing open soures code.
COMMENT #103 [Permalink]
...
Larry Bergan
said on 9/18/2006 @ 4:26 am PT...
Barbara Bellows-TerraNova #99
So that WAS you on the Diane Rehm show!
I thought that was the best treatment yet of the voting machine problem on NPR and couldn't believe they didn't include the usual panel of naysayers to refute Mr. Rubin.
I couldn't remember any callers being against him either. It was as if nobody's willing to tell lies about our terrible election system anymore!
COMMENT #104 [Permalink]
...
wilywascal
said on 9/18/2006 @ 5:18 pm PT...
RE-#99
Thanks for pointing that out. First video includes detailed explanation by Bruce Funk. Disclaimer: contains plug for this blog (which I am not affiliated with). Mr. Funk states this issue is not about him. It might have been more concise, but the informal layout gives a good sense of Mr. Funk and the situation. The two-hour length unfortunately confines access to those with high-speed connections.
Second link has a briefer interview with Bruce Funk and Computer Science Professor Dill at Stanford. It offers video, audio or a transcript for those with dial-up.
http://video.google.com/...ocid=1396271232701024595
http://www.democracynow.....pl?sid=06/05/31/1330240

 A vote for George Washington could easily be converted to a vote for Benedict Arnold on an electronic voting machine and neither the voter, nor the election officials administering the election would ever know what happened. It wouldn't require a "conspiracy theory" or a "conspiracy" at all. It could be done by a single person with just a few moments of access to the voting systems.
A vote for George Washington could easily be converted to a vote for Benedict Arnold on an electronic voting machine and neither the voter, nor the election officials administering the election would ever know what happened. It wouldn't require a "conspiracy theory" or a "conspiracy" at all. It could be done by a single person with just a few moments of access to the voting systems.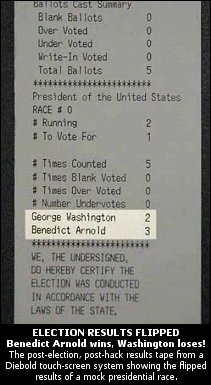 "We've demonstrated that malicious code can spread like a virus from one voting machine to another," said Felten in an exclusive interview, "which means that a bad guy who can get access to a few machines --- or only one --- can infect one machine, which could infect another, stealing a few votes on each in order to steal an entire election."
"We've demonstrated that malicious code can spread like a virus from one voting machine to another," said Felten in an exclusive interview, "which means that a bad guy who can get access to a few machines --- or only one --- can infect one machine, which could infect another, stealing a few votes on each in order to steal an entire election." When San Diego County Registrar of Voters Mikel Haas was asked about the security breaches in the Busby/Bilbray election and whether they might have put the election at risk, he downplayed the dangers.
When San Diego County Registrar of Voters Mikel Haas was asked about the security breaches in the Busby/Bilbray election and whether they might have put the election at risk, he downplayed the dangers.  Unfortunately, such "evil elections people" do exist. During a radio interview I conducted with Monterey County, California Registrar of Voters Tony Anchundo prior to the November 2005 election, the 13-year election official explained, when asked which results would be official in the event that their new voting machine "paper trails" didn't match up with the machine-reported totals that, "There is obviously going to have to be some trust and faith in the elections official, or in this case, it's me."
Unfortunately, such "evil elections people" do exist. During a radio interview I conducted with Monterey County, California Registrar of Voters Tony Anchundo prior to the November 2005 election, the 13-year election official explained, when asked which results would be official in the event that their new voting machine "paper trails" didn't match up with the machine-reported totals that, "There is obviously going to have to be some trust and faith in the elections official, or in this case, it's me." Deborah Hench, Registrar of Voters in San Joaquin County, California has gone on record denying the vulnerabilities and failures of the systems even after California conducted the largest mock-election test ever held in her own warehouse, on her own Diebold touch-screen voting systems. That test, conducted in July of 2005 found that the systems failed to operate properly nearly 30% of the time.
Deborah Hench, Registrar of Voters in San Joaquin County, California has gone on record denying the vulnerabilities and failures of the systems even after California conducted the largest mock-election test ever held in her own warehouse, on her own Diebold touch-screen voting systems. That test, conducted in July of 2005 found that the systems failed to operate properly nearly 30% of the time. Sancho, who was forced by the state of Florida to use Diebold voting machines even after he allowed computer hackers the opportunity to test – successfully – their theoretical hack, which flipped a mock election on an optical scan paper ballot system manufactured by Diebold told an election integrity gathering last May that the public should "Trust no one," when it comes to our electoral system. "If it can't be verified, it can't be used," he told the enthusiastic crowd.
Sancho, who was forced by the state of Florida to use Diebold voting machines even after he allowed computer hackers the opportunity to test – successfully – their theoretical hack, which flipped a mock election on an optical scan paper ballot system manufactured by Diebold told an election integrity gathering last May that the public should "Trust no one," when it comes to our electoral system. "If it can't be verified, it can't be used," he told the enthusiastic crowd. Oakley was even more to the point in an email sent to The BRAD BLOG as the "sleepover" controversy erupted after the June elections in California: "If, as a practical matter," she wrote about the Diebold electronic voting machines used in the election, they "can't be secured, then perhaps they ought not be used at all. Period."
Oakley was even more to the point in an email sent to The BRAD BLOG as the "sleepover" controversy erupted after the June elections in California: "If, as a practical matter," she wrote about the Diebold electronic voting machines used in the election, they "can't be secured, then perhaps they ought not be used at all. Period."

 It's About Elections and the Windmills of His Mind: 'BradCast' 1/29/26
It's About Elections and the Windmills of His Mind: 'BradCast' 1/29/26 'Green News Report' 1/29/26
'Green News Report' 1/29/26
 Govt Shutdown Over ICE Funding Near Certain This Weekend: 'BradCast' 1/28/26
Govt Shutdown Over ICE Funding Near Certain This Weekend: 'BradCast' 1/28/26 Trump Blinks, Bovino Out, MN Op Falters but Continues as Midterm Accountability Looms: 'BradCast' 1/27/26
Trump Blinks, Bovino Out, MN Op Falters but Continues as Midterm Accountability Looms: 'BradCast' 1/27/26 'Green News Report' 1/27/26
'Green News Report' 1/27/26 The ICE Murder of ICU Nurse Alex Pretti and the Heroes of Minneapolis: 'BradCast' 1/26/26
The ICE Murder of ICU Nurse Alex Pretti and the Heroes of Minneapolis: 'BradCast' 1/26/26  The BRAD BLOG: 22 Years and Still Counting
The BRAD BLOG: 22 Years and Still Counting Sunday 'Worth a Thousand Words' Toons
Sunday 'Worth a Thousand Words' Toons Mr. Smith Testifies (Publicly) in Washington: 'BradCast' 1/22/26
Mr. Smith Testifies (Publicly) in Washington: 'BradCast' 1/22/26 'Green News Report' 1/22/26
'Green News Report' 1/22/26 World Turning Against Self-Destructing U.S. Under Trump: 'BradCast' 1/21/26
World Turning Against Self-Destructing U.S. Under Trump: 'BradCast' 1/21/26 Trump Admin Waste, Fraud, Abuse on Voting, at DOJ, by DOGE: 'BradCast' 1/20/26
Trump Admin Waste, Fraud, Abuse on Voting, at DOJ, by DOGE: 'BradCast' 1/20/26 'Green News Report' 1/20/26
'Green News Report' 1/20/26 Sunday 'Domestic Terrorist' Toons
Sunday 'Domestic Terrorist' Toons 'Green News Report' 1/15/26
'Green News Report' 1/15/26 'A Cornered Rat': Trump Terrorizes Minneapolis, Menaces NATO, World: 'BradCast' 1/15/26
'A Cornered Rat': Trump Terrorizes Minneapolis, Menaces NATO, World: 'BradCast' 1/15/26 'Not Close to Over': Mad King Trump in Venezuela (& Beyond): 'BradCast' 1/14
'Not Close to Over': Mad King Trump in Venezuela (& Beyond): 'BradCast' 1/14 Things Getting Weirder as Trump Keeps Losing: 'BradCast' 1/13/26
Things Getting Weirder as Trump Keeps Losing: 'BradCast' 1/13/26 After ICE Murder in MN, Local Cops Disown Fed Policing Practices: 'BradCast' 1/12/26
After ICE Murder in MN, Local Cops Disown Fed Policing Practices: 'BradCast' 1/12/26 Trump to Congress, Climate, U.N., Rule of Law: DROP DEAD - 'BradCast' 1/8/26
Trump to Congress, Climate, U.N., Rule of Law: DROP DEAD - 'BradCast' 1/8/26 'Nonsense': Trumpers Claim 315k Fraudulent GA Votes in 2020: 'BradCast' 1/7/26
'Nonsense': Trumpers Claim 315k Fraudulent GA Votes in 2020: 'BradCast' 1/7/26 Jack Smith Testimony on Trump J6 Crimes, DOJ Weaponization: 'BradCast' 1/6/26
Jack Smith Testimony on Trump J6 Crimes, DOJ Weaponization: 'BradCast' 1/6/26 Trump War on Venez. is About Ego, Power, 'Alien Enemies Act': 'BradCast' 1/5/26
Trump War on Venez. is About Ego, Power, 'Alien Enemies Act': 'BradCast' 1/5/26
 VA GOP VOTER REG FRAUDSTER OFF HOOK
VA GOP VOTER REG FRAUDSTER OFF HOOK Criminal GOP Voter Registration Fraud Probe Expanding in VA
Criminal GOP Voter Registration Fraud Probe Expanding in VA DOJ PROBE SOUGHT AFTER VA ARREST
DOJ PROBE SOUGHT AFTER VA ARREST Arrest in VA: GOP Voter Reg Scandal Widens
Arrest in VA: GOP Voter Reg Scandal Widens ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC
ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States'
LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States' 'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States
'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States FINALLY: FOX ON GOP REG FRAUD SCANDAL
FINALLY: FOX ON GOP REG FRAUD SCANDAL COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION
COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL
CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV
Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV  CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM
CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM
CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL
RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV
VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD
RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud
EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud GOP REGISTRATION FRAUD FOUND IN FL
GOP REGISTRATION FRAUD FOUND IN FL

































