Hack team leader: 'Can do similar things on pretty much every e-voting machine'...
[UPDATE 9/28/11: I interviewed Argonne National Lab's Roger Johnston on my Pacific Radio show on KPFK today. In the interview, Johnston concedes that it's not only touch-screen systems of the type described below which are vulnerable to this newly developed hack, but that paper-ballot based optical-scan systems can likely be manipulated by the same techniques. My interview with Johnson is now posted here. - BF]
* * *
 The Vulnerability Assessment Team (VAT) at the U.S. Dept. of Energy's Argonne National Laboratory in Illinois has managed to hack a Diebold Accuvote touch-screen voting machine in what I describe at my exclusive today at Salon as perhaps "one of the most disturbing e-voting machine hacks to date."
The Vulnerability Assessment Team (VAT) at the U.S. Dept. of Energy's Argonne National Laboratory in Illinois has managed to hack a Diebold Accuvote touch-screen voting machine in what I describe at my exclusive today at Salon as perhaps "one of the most disturbing e-voting machine hacks to date."
As noted by the computer scientists and security experts at Argonne's VAT, largely all that's needed to accomplish this hack is about $26 and an 8th grade science education.
"This is a national security issue," VAT team leader Dr. Roger Johnston told me, echoing what I've been reporting other computer scientists and security experts telling me for years. "It should really be handled by the Department of Homeland Security."
Johnston should know. While the VAT folks have been dabbling in the security (or lack thereof) of e-voting systems in their spare time of late, most of the work they do is related to issues like nuclear safeguards and non-proliferation.
What makes this hack so troubling --- and different from those which have come before it --- is that it doesn't require any actual changes to, or even knowledge of, the voting system software or its memory card programming. It's not a cyberattack. It's a "Man-in-the-middle" attack where a tiny, $10.50 piece of electronics is inserted into the system between the voter and the main circuit board of the voting system allowing for complete control over the touch-screen system and the entire voting process along with it.
 Add an optional $15 radio frequency remote control device, and votes can be changed, without the knowledge of the voter, from up to half a mile away. Without the remote, the attack can be turned on and off at certain times, or by other triggers. The voter would have no idea that their votes have been changed after they've already approved them as "correct" on the various confirmation screens, and even on the so-called "paper-trail" (on e-voting machines which offer them --- though VAT has learned how to manipulate those as well, see photo at right.)
Add an optional $15 radio frequency remote control device, and votes can be changed, without the knowledge of the voter, from up to half a mile away. Without the remote, the attack can be turned on and off at certain times, or by other triggers. The voter would have no idea that their votes have been changed after they've already approved them as "correct" on the various confirmation screens, and even on the so-called "paper-trail" (on e-voting machines which offer them --- though VAT has learned how to manipulate those as well, see photo at right.)
The inserted chip can later be removed after the election without there being any way to ever know that someone had completely manipulated the system. But since election officials rarely --- if ever --- examine the inside of their voting machines, it doesn't much matter, in truth.
"The level of sophistication it took to develop the circuit board" used in the attack "was that of basically an 8th grade science shop," says Argonne's John Warner. "Anybody with an electronics workbench could put this together."
The team, he says, had no knowledge of the voting machine's computer circuit diagram or owner's manual when they devised the attack. Moreover, VAT team leader Roger Johnston told me they believe they "can do similar things on pretty much every electronic voting machine." Indeed, in 2009, with little fanfare, they were able to carry out a similar manipulation of a Seqouia AVC Advantage e-voting system (as used across most of the state of New Jersey, for example). You can see that video demo here.
The team at Argonne has shared their demo video of the new Diebold Accuvote hack exclusively with The BRAD BLOG, as posted below. But please go check out the full details over at Salon (where we've embedded the video as well). The full details are chilling --- particularly as about 20% to 30% of U.S. voters are still set to use Diebold touch-screen systems, and others very similar to it, across the nation in the 2012 election cycle, no matter how many years The BRAD BLOG has been desperately trying to illustrate that these systems are simply antithetical to American democracy.
Among the states where voters will use these systems on Election Day in 2012, according to VerifiedVoting.org: Georgia, Maryland, Utah, Nevada, New Jersey, Pennsylvania, Indiana, Missouri, Texas and many more.
Almost five years ago to the day, I broke the story of Princeton's landmark Diebold Virus Hack in another exclusive for Salon. So while I'm delighted to break the news of this new type of hack over there today, it's somewhat frustrating that it's even necessary at this point, as we head into yet another Presidential election cycle having changed so little despite all that we've learned. Nonetheless, please go check out my story over there today.
* * *
Beyond that, the video demonstration itself from Argonne, of the remote hack of a Diebold Accuvote touch-screen system follows below...
--- Click here for REST OF STORY!... ---
 Now THIS is what democracy looks like. Some really great news via Ian Millhiser at ThinkProgress...
Now THIS is what democracy looks like. Some really great news via Ian Millhiser at ThinkProgress...

 Is MAGA Finally Beginning to Fall Apart?: 'BradCast' 11/19/25
Is MAGA Finally Beginning to Fall Apart?: 'BradCast' 11/19/25 Trump's Terrible, Horrible,
Trump's Terrible, Horrible, 'Green News Report' 11/18/25
'Green News Report' 11/18/25
 A Kaleidoscope of Trump Corruption: 'BradCast' 11/17/25
A Kaleidoscope of Trump Corruption: 'BradCast' 11/17/25  Sunday 'Back to Business' Toons
Sunday 'Back to Business' Toons Trump DOJ Takes Stand
Trump DOJ Takes Stand 'Green News Report' 11/13/25
'Green News Report' 11/13/25 Mamdani's 'Surprisingly Affordable' Afford-ability Agenda for NYC: 'BradCast' 11/12
Mamdani's 'Surprisingly Affordable' Afford-ability Agenda for NYC: 'BradCast' 11/12 After the Shutdown and Before the Next One: 'BradCast' 11/11/25
After the Shutdown and Before the Next One: 'BradCast' 11/11/25 'Green News Report' 11/11/25
'Green News Report' 11/11/25 Victories for Democracy in Election 2025; Also: 7 Dems, 1 Indie Vote to End Shutdown in Senate: 'BradCast' 11/10/25
Victories for Democracy in Election 2025; Also: 7 Dems, 1 Indie Vote to End Shutdown in Senate: 'BradCast' 11/10/25 Sunday 'Ass Kicking' Toons
Sunday 'Ass Kicking' Toons 'We Can See Light at the End of the Tunnel' After Election 2025: 'BradCast' 11/6/25
'We Can See Light at the End of the Tunnel' After Election 2025: 'BradCast' 11/6/25 'Green News Report' 11/6/25
'Green News Report' 11/6/25 BLUE WAVE! Dems Win Everything Everywhere All at Once: 'BradCast' 11/5/25
BLUE WAVE! Dems Win Everything Everywhere All at Once: 'BradCast' 11/5/25 Repub Thuggery As Americans Vote: 'BradCast' 11/4/25
Repub Thuggery As Americans Vote: 'BradCast' 11/4/25 Last Call(s) Before Election Day 2025: 'BradCast' 11/3/25
Last Call(s) Before Election Day 2025: 'BradCast' 11/3/25 A Pretty Weak 'Strongman': 'BradCast' 10/30/25
A Pretty Weak 'Strongman': 'BradCast' 10/30/25 Proposal for 'Politically Viable Wealth Tax' Takes Shape in CA: 'BradCast' 10/29
Proposal for 'Politically Viable Wealth Tax' Takes Shape in CA: 'BradCast' 10/29 Monster Storm, Endless Wars, Gamed Elections: 'BradCast' 10/28/25
Monster Storm, Endless Wars, Gamed Elections: 'BradCast' 10/28/25 Let's Play 'Who Wants to Be a U.S. Citizen?'!: 'BradCast' 10/27/25
Let's Play 'Who Wants to Be a U.S. Citizen?'!: 'BradCast' 10/27/25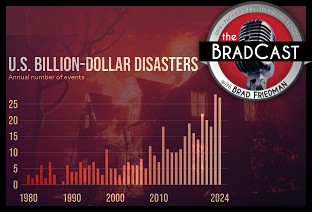 Exiled NOAA Scientists Resurrect Critical Disaster Database: 'BradCast' 10/23/25
Exiled NOAA Scientists Resurrect Critical Disaster Database: 'BradCast' 10/23/25
 VA GOP VOTER REG FRAUDSTER OFF HOOK
VA GOP VOTER REG FRAUDSTER OFF HOOK Criminal GOP Voter Registration Fraud Probe Expanding in VA
Criminal GOP Voter Registration Fraud Probe Expanding in VA DOJ PROBE SOUGHT AFTER VA ARREST
DOJ PROBE SOUGHT AFTER VA ARREST Arrest in VA: GOP Voter Reg Scandal Widens
Arrest in VA: GOP Voter Reg Scandal Widens ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC
ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States'
LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States' 'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States
'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States FINALLY: FOX ON GOP REG FRAUD SCANDAL
FINALLY: FOX ON GOP REG FRAUD SCANDAL COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION
COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL
CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV
Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV  CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM
CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM
CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL
RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV
VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD
RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud
EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud GOP REGISTRATION FRAUD FOUND IN FL
GOP REGISTRATION FRAUD FOUND IN FL



















 The
The 


 This afternoon on my Pacifica Radio show on
This afternoon on my Pacifica Radio show on 
 The
The  Add an optional $15 radio frequency remote control device, and votes can be changed, without the knowledge of the voter, from up to half a mile away. Without the remote, the attack can be turned on and off at certain times, or by other triggers. The voter would have no idea that their votes have been changed after they've already approved them as "correct" on the various confirmation screens, and even on the so-called "paper-trail" (on e-voting machines which offer them --- though VAT has learned how to manipulate those as well, see photo at right.)
Add an optional $15 radio frequency remote control device, and votes can be changed, without the knowledge of the voter, from up to half a mile away. Without the remote, the attack can be turned on and off at certain times, or by other triggers. The voter would have no idea that their votes have been changed after they've already approved them as "correct" on the various confirmation screens, and even on the so-called "paper-trail" (on e-voting machines which offer them --- though VAT has learned how to manipulate those as well, see photo at right.)
 Since taking power in statehouses across the nation in 2010, Republicans have been feverishly implementing new restrictions on democracy in advance of the 2012 Presidential election. A number of those laws, clearly --- and often deceptively --- designed to carve out blatant partisan advantage for the GOP next year, were examined during a recent hearing by the U.S. Senate Judiciary Subcommittee on the Constitution, Civil Rights and Human Rights. The video of the hearing on "New State Voting Laws: Barriers to the Ballot" can be
Since taking power in statehouses across the nation in 2010, Republicans have been feverishly implementing new restrictions on democracy in advance of the 2012 Presidential election. A number of those laws, clearly --- and often deceptively --- designed to carve out blatant partisan advantage for the GOP next year, were examined during a recent hearing by the U.S. Senate Judiciary Subcommittee on the Constitution, Civil Rights and Human Rights. The video of the hearing on "New State Voting Laws: Barriers to the Ballot" can be 
 First, hearty congratulations are in order to the Koch brothers who, according to Forbes, are now
First, hearty congratulations are in order to the Koch brothers who, according to Forbes, are now 
 There are two important late Friday announcements from the newly revived, post-Bush Voting Unit at U.S. Dept. of Justice's Civil Rights Division this afternoon. In both cases, they've raised serious concerns about discrimination by Republican Presidential front-runner Rick Perry's Texas against Hispanic and African-American voters.
There are two important late Friday announcements from the newly revived, post-Bush Voting Unit at U.S. Dept. of Justice's Civil Rights Division this afternoon. In both cases, they've raised serious concerns about discrimination by Republican Presidential front-runner Rick Perry's Texas against Hispanic and African-American voters.
 Guest blogged by Ernest A. Canning
Guest blogged by Ernest A. Canning












