 On today's BradCast, we've got an exclusive interview with CHRIS VICKERY, Director of Cyber Risk Research at the cyber security firm UpGuard. Vickery revealed late last week on Twitter that he discovered files, including administrative master passwords for voting systems, at the North Carolina State Board of Elections website that were left vulnerable and available online for anyone to download, prior to the 2018 election. Today he explains the evidence that suggests these files may have been available as early as February of 2016, months before that year's controversial Presidential election. [Audio link to full show is posted at bottom of article.]
On today's BradCast, we've got an exclusive interview with CHRIS VICKERY, Director of Cyber Risk Research at the cyber security firm UpGuard. Vickery revealed late last week on Twitter that he discovered files, including administrative master passwords for voting systems, at the North Carolina State Board of Elections website that were left vulnerable and available online for anyone to download, prior to the 2018 election. Today he explains the evidence that suggests these files may have been available as early as February of 2016, months before that year's controversial Presidential election. [Audio link to full show is posted at bottom of article.]
The files were found by Vickery unencrypted and with no password needed to retrieve them from the site. He tells me today that there were so many files and screenshots (see a redacted snippet from one of the password screenshots in the graphic above), that he's not even sure if they number in the hundreds or thousands.
The longtime cyber security researcher says he promptly notified state officials of the discovery last year, before the 2018 elections, and that the state, shortly thereafter, set the files in question and their directories to "private". In response to a commenter on his short Twitter thread revealing the potential security breech late last Friday, however, he notes that "someone would have had to actively choose to make the file repository available to the entire world. It is not unprotected by default."
He tells me today that he is "very concerned" about the exposure and would "like to know who the data was intended for. If you put it up somewhere, you're intending it to be accessed by somebody. So who did they aim this for? I would love to know that." Indeed, he also shared an email with me over the weekend that was posted in the same directory as the passwords screenshot, in which a State Board of Elections official notes: "The attached screen shots should show just about all of the settings you will need for contests and candidates" in the ES&S iVotronic Image Management program, part of the computer voting system which defines where candidates selected by voters are placed on the electronic ballots and optical-scan systems.
Vickery says he decided to go public with the disclosure following the Washington Post exclusive last week reporting that federal investigators at the Dept. of Homeland Security have finally agreed to work with NC on a forensic investigation of the state's voter registration computers which inexplicably failed during the 2016 Presidential Election, on Election Day, in parts of the state. That announcement via the Post comes on the heels of Robert Mueller's redacted report [PDF] (see Volume 2, page 50, "Intrusions Targeting the Administration of U.S. Elections"), in which the Special Counsel briefly details how Russian Military Intelligence operatives were able to penetrate the voter registration systems of "at least one" county in Florida. Just over a week ago, the new Republican Governor of Florida announced he was notified by the FBI that, in fact, two counties had, in fact, been penetrated via a spearphishing attack on VR Systems, the private vendor contracted to run those voter registration systems.
VR Systems also supplies similar systems in about half a dozen other U.S. states, one of them being North Carolina. But, as Vickery notes, the password files that he found exposed on the Internet last year were not for registration systems, but for the state's computer voting machines, scanners and tabulation systems made by private vendor ES&S (the nation's largest), as used across most of the state of North Carolina. And ALL of this comes after we have been trying to point out on The BradCast for the last two and a half years that nobody --- not the FBI, not DHS, not the states themselves, nor even Mueller's Special Counsel team, as he admits --- ever carried out a forensic investigation of the computer voting, registration or tabulation systems in use in any of the states in 2016, despite that election's surprise ending in which Donald Trump purportedly won by a razor thin margin.
In his first broadcast interview on these new revelations, Vickery explains how he discovered the files, how the state responded when he told them about the vulnerability last year, whether the DHS has contacted him since he revealed his findings on Friday, and how serious of a potential security breech this is, especially given the extraordinary effort that the U.S. Intelligence Community and the Mueller Report claim Russia expended in hopes of interfering in the 2016 Presidential election. "When you have computers, and software, and firmware updating passwords and modems all mixed in together, you have the capability to do a lot of crazy stuff," he says, in response to my question about whether these passwords could have been used to alter or upload false results. "It's not out of the realm of possibility, but I have no specific reason to believe that happened. But that is kind of a frightening concept to realize that all of the ingredients are there."
Disturbingly, Vickery's report is startlingly similar to one revealed last year by Kim Zetter at Politico in the state of Georgia, regarding a security researcher who found millions of voter registrations along with voting system administrative passwords online and vulnerable to download without a password, prior to the Peach State's 2016 elections.
Also today: The last many weeks of climate changed-fueled weather disasters move from the Central U.S. to the SouthEast, with a month's worth of rain falling in one day over this past weekend (yet the DNC still won't allow a 2020 Presidential candidate debate focused solely on climate change!); Donald Trump pretends that his backing off of a threat to tax Americans who purchase imported goods from Mexico is a great negotiation victory; And we take a few calls on our disturbing interview with Vickery, including from one listener who quips that NC "left the combination of the safe written on top of the door"...
(Snail mail support to "Brad Friedman, 7095 Hollywood Blvd., #594 Los Angeles, CA 90028" always welcome too!)
|


 Trump EPA Guts Enviro Justice Office: 'BradCast' 4/24/25
Trump EPA Guts Enviro Justice Office: 'BradCast' 4/24/25 'Green News Report' 4/24/25
'Green News Report' 4/24/25
 Nation's Largest Broadcaster Mandates News Outlets Hoax Viewers to Help Gut FCC Rules: 'BradCast' 4/23/25
Nation's Largest Broadcaster Mandates News Outlets Hoax Viewers to Help Gut FCC Rules: 'BradCast' 4/23/25 Trump's FCC on Precipice of Ending All Limits on Corporate Control of Local TV Stations
Trump's FCC on Precipice of Ending All Limits on Corporate Control of Local TV Stations GOP Earth Day 2025 Hypocrisies and Dilemmas: 'BradCast' 4/22/25
GOP Earth Day 2025 Hypocrisies and Dilemmas: 'BradCast' 4/22/25 'Green News Report' 4/22/25
'Green News Report' 4/22/25 Pope Francis Dies,
Pope Francis Dies, Sunday
Sunday  Sunday 'Zero Day' Toons
Sunday 'Zero Day' Toons Soc. Sec. Expert Warns DOGE Hastening Collapse, Privati-zation: 'BradCast' 4/10/2025
Soc. Sec. Expert Warns DOGE Hastening Collapse, Privati-zation: 'BradCast' 4/10/2025 'Green News Report' 4/10/25
'Green News Report' 4/10/25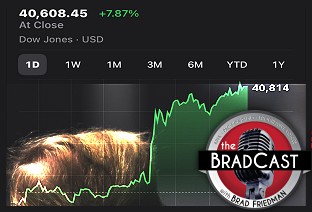 Trump Blinks, Chaos Reigns, Markets Spike as Many Tariffs Remain Despite 90-Day 'Pause': 'BradCast' 4/9/25
Trump Blinks, Chaos Reigns, Markets Spike as Many Tariffs Remain Despite 90-Day 'Pause': 'BradCast' 4/9/25 SCOTUS Deportation Ruling Grimmer Than First Appears: 'BradCast' 4/8/25
SCOTUS Deportation Ruling Grimmer Than First Appears: 'BradCast' 4/8/25 'Green News Report' 4/8/25
'Green News Report' 4/8/25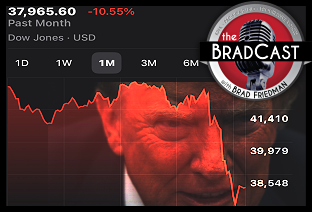 Cliff Diving with Donald: 'BradCast' 4/7/25
Cliff Diving with Donald: 'BradCast' 4/7/25 Sunday 'Don't Look Down' Toons
Sunday 'Don't Look Down' Toons 'Green News Report' 4/3/25
'Green News Report' 4/3/25 'Mob Boss' Trump's Trade Sanctions Tank U.S., World Markets: 'BradCast' 4/3/25
'Mob Boss' Trump's Trade Sanctions Tank U.S., World Markets: 'BradCast' 4/3/25 Crawford Landslide in WI; Booker Makes History in U.S. Senate: 'BradCast' 4/2/25
Crawford Landslide in WI; Booker Makes History in U.S. Senate: 'BradCast' 4/2/25 Judge Ends Challenge to GA's Unverifiable, Insecure Vote System: 'BradCast' 4/1/25
Judge Ends Challenge to GA's Unverifiable, Insecure Vote System: 'BradCast' 4/1/25 Bad Court, Election News for Trump is Good News for U.S.: 'BradCast' 3/31
Bad Court, Election News for Trump is Good News for U.S.: 'BradCast' 3/31 Vets Push Back at Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25
Vets Push Back at Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25 Signal Scandal Worsens for Trump, GOP; Big Dem Election Wins in PA: 'BradCast' 3/26
Signal Scandal Worsens for Trump, GOP; Big Dem Election Wins in PA: 'BradCast' 3/26 'Emptywheel': Trump NatSec Team Should 'Resign in Disgrace': 'BradCast' 3/25/25
'Emptywheel': Trump NatSec Team Should 'Resign in Disgrace': 'BradCast' 3/25/25 USPS 'Belongs to the People, Not the Billionaires': 'BradCast' 3/24/25
USPS 'Belongs to the People, Not the Billionaires': 'BradCast' 3/24/25
 VA GOP VOTER REG FRAUDSTER OFF HOOK
VA GOP VOTER REG FRAUDSTER OFF HOOK Criminal GOP Voter Registration Fraud Probe Expanding in VA
Criminal GOP Voter Registration Fraud Probe Expanding in VA DOJ PROBE SOUGHT AFTER VA ARREST
DOJ PROBE SOUGHT AFTER VA ARREST Arrest in VA: GOP Voter Reg Scandal Widens
Arrest in VA: GOP Voter Reg Scandal Widens ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC
ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States'
LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States' 'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States
'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States FINALLY: FOX ON GOP REG FRAUD SCANDAL
FINALLY: FOX ON GOP REG FRAUD SCANDAL COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION
COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL
CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV
Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV  CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM
CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM
CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL
RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV
VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD
RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud
EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud GOP REGISTRATION FRAUD FOUND IN FL
GOP REGISTRATION FRAUD FOUND IN FL



















 On today's
On today's  Today's
Today's  On today's
On today's  Every great Reality TV show needs a dramatic and gripping season finale. So too, apparently, does does every horrible Reality TV Presidency! [Audio link is posted below]
Every great Reality TV show needs a dramatic and gripping season finale. So too, apparently, does does every horrible Reality TV Presidency! [Audio link is posted below] Lots of news (for a change?) on today's
Lots of news (for a change?) on today's  Of all of the reactions to the July 16 joint press conference in Helsinki, Finland in which Russian President Vladimir Putin and U.S. President Donald Trump responded to reporters' questions, perhaps the harshest assessment came in a
Of all of the reactions to the July 16 joint press conference in Helsinki, Finland in which Russian President Vladimir Putin and U.S. President Donald Trump responded to reporters' questions, perhaps the harshest assessment came in a  On today's
On today's 







 On today's
On today's  On today's
On today's  For a few blessed moments on Monday, the peoples of the United States set politics aside, for the most part, to look skyward, toward the first
For a few blessed moments on Monday, the peoples of the United States set politics aside, for the most part, to look skyward, toward the first  On today's
On today's  On today's
On today's  On today's
On today's 













