 A number of mainstream news outlets (for a pleasant change) followed up on our report yesterday (full version here, quick summary here) on the SQL Slammer Worm virus which hit Sarasota County's database network on the first day of Early Voting last year, wreaking havoc which disallowed voting for two hours in the now-contest FL-13 U.S. House election between Christine Jennings (D) and Vern Buchanan (R). No telling what got into the MSM'ers, but perhaps it's because we ran the story at Computerworld first instead of here at the "dreaded" and "unreliable" blog.
A number of mainstream news outlets (for a pleasant change) followed up on our report yesterday (full version here, quick summary here) on the SQL Slammer Worm virus which hit Sarasota County's database network on the first day of Early Voting last year, wreaking havoc which disallowed voting for two hours in the now-contest FL-13 U.S. House election between Christine Jennings (D) and Vern Buchanan (R). No telling what got into the MSM'ers, but perhaps it's because we ran the story at Computerworld first instead of here at the "dreaded" and "unreliable" blog.
Either way, of the several outlets we found who picked up the story (with more on the way, we're told, and local TV news coverage which we haven't been able to find online), the Brandenton Herald's coverage led the pack in advancing the story which they said "caused a stir Wednesday".
Their report includes a quote from Jennings --- who was named the loser in the race by just 369 votes, despite 18,000 reported undervotes on the county's ES&S iVotronic touch-screen voting machines --- saying "I read the story on the Internet and I was surprised...I need to know more about it. It does bring up some security issues that I think need to be looked at."
Her campaign spokesperson, David Kochman adds, "It makes you wonder what else is there that they haven't done to take care of the machines and protect them."
But Kochman does help answer one very important question we asked in our piece yesterday, about whether or not the county had notified the plaintiff's attorneys about this incident via the discovery process...
"We got tens of thousands of pages of documents and one of those things that we received literally had 32,000 e-mails on it. It was in one of those e-mails," Kochman told the paper.
Before we ran our original story, Kochman told us he was trying to comb through documents to determine whether the incident report describing the successful viral attack had been included in what had been turned over to Jennings. Apparently it was.
We're still trying to determine if the voter plaintiffs, who filed a separate suit in the case, were informed as well.
Either way, details of the incident were specifically not mentioned in the county's state-mandated "Conduct of Elections Report", signed by Election Supervisor Kathy Dent on November 18th. As we reported yesterday, an email to Dent reveals that she was notified about the October 23rd incident on November 9th. As well, she refused to return requests for comment on the matter placed by the Brandenton Herald --- just as she did when we twice tried to contact her for same --- so there is still no explanation for why the incident was more fully disclosed.
The Register in the UK also covered our report, adding that the incident highlights the dangers of secret e-voting systems.
"The lack of transparency is breathtaking," they said, before concluding with: "Free and open elections, without which democracy isn't possible, demand a fearless pursuit of the truth, something that appears to be in short supply in Sarasota."
And finally, for now, Allan Holmes' "Tech Insider" coverage for Government Executive, a print and online 'zine which bills itself as "the authoritative voice on the business of government" and "the premier vehicle to connect businesses and federal decision-makers," reports that the incident demonstrates fears by e-voting critics of viruses striking election machinery is no longer just a theory. "Now it seems theory has become reality," Holmes writes.
"The delay could have played a big part in the outcome of the election," he adds, noting that Buchanan's 369 vote "win" might have been affected by the confirmed two hour system outage in all Early Voting locations in the the Democratic-leaning Sarasota County --- Jennings strongest county.
"Did the wait dissuade some from voting?," Holmes wonders, before summing up with a particular cogent point:
Indeed, while the folks who oversaw the system which was attacked, including one of the county's security experts, Hal Logan, who we quoted in the article, seem to take their job quite seriously, even the best of IT system experts are frequently bested by hackers trying to defeat the system. And what higher target could their be, then our electoral system on which trillions of dollars hang in the balance.
And yet, we've allowed small, underfunded governmental entities --- such as the thousands of county election offices around the country --- to build the precious and precarious machinery of democracy on top of extremely sensitive, virus prone, high-tech, mission-critical IT hardware and software which even well-funded, highly-trained experts in the private sector have enough trouble keeping secure and online.
What must America be thinking to believe that these types of incredibly complicated systems can be properly maintained and secured by small time, local governmental officials who have absolutely no idea how these systems even work --- or don't --- in the first place?
What in God's name must we be thinking?...


 Judge Dismisses Long-Running Challenge to GA's Unverifiable, Insecure E-Vote System: 'BradCast' 4/1/25
Judge Dismisses Long-Running Challenge to GA's Unverifiable, Insecure E-Vote System: 'BradCast' 4/1/25 'Green News Report' 4/1/25
'Green News Report' 4/1/25
 Bad Court and Election News for Trump is Good News for America: 'BradCast' 3/31/25
Bad Court and Election News for Trump is Good News for America: 'BradCast' 3/31/25 Sunday 'Great Start!' Toons
Sunday 'Great Start!' Toons Vets Push Back at Trump, Musk Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25
Vets Push Back at Trump, Musk Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25 'Green News Report' 3/27/25
'Green News Report' 3/27/25 Signal Scandal Worsens for Trump, GOP; Big Dem Election Wins in PA: 'BradCast' 3/26
Signal Scandal Worsens for Trump, GOP; Big Dem Election Wins in PA: 'BradCast' 3/26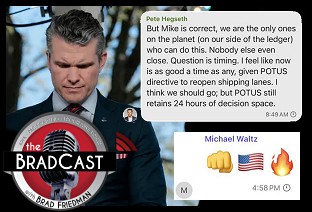 'Emptywheel' on Why Trump NatSec Team Should 'Resign in Disgrace' After Signal Chat Debacle: 'BradCast' 3/25/25
'Emptywheel' on Why Trump NatSec Team Should 'Resign in Disgrace' After Signal Chat Debacle: 'BradCast' 3/25/25 'Green News Report' 3/25/25
'Green News Report' 3/25/25 USPS 'Belongs to the People, Not the Billionaires': 'BradCast' 3/24/25
USPS 'Belongs to the People, Not the Billionaires': 'BradCast' 3/24/25 Sunday 'Suddenly Conceivable' Toons
Sunday 'Suddenly Conceivable' Toons 'Green News Report' 3/20/25
'Green News Report' 3/20/25 We're ALL Voice of America Now: 'BradCast' 3/20/25
We're ALL Voice of America Now: 'BradCast' 3/20/25 What Trump's 'Timber Production Expansion' Means (and Costs): 'BradCast' 3/19/25
What Trump's 'Timber Production Expansion' Means (and Costs): 'BradCast' 3/19/25 Courts Largely Holding Against Trump, Musk Lawlessness: 'BradCast' 3/18/25
Courts Largely Holding Against Trump, Musk Lawlessness: 'BradCast' 3/18/25 Chief VOA Reporter on Outlet Falling Silent First Time Since 1942: 'BradCast' 3/17/25
Chief VOA Reporter on Outlet Falling Silent First Time Since 1942: 'BradCast' 3/17/25 Trump EPA Unveils Plans to Endanger, Sicken Americans: 'BradCast' 3/13/25
Trump EPA Unveils Plans to Endanger, Sicken Americans: 'BradCast' 3/13/25 Trump Nixed Enforce-ment Against 100 Corp. Lawbreakers: 'BradCast' 3/12/25
Trump Nixed Enforce-ment Against 100 Corp. Lawbreakers: 'BradCast' 3/12/25 Bad Day for 'Strongmen': 'BradCast' 3/11
Bad Day for 'Strongmen': 'BradCast' 3/11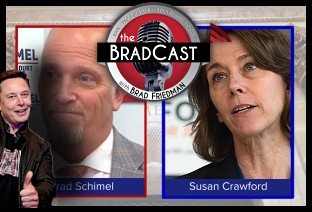 WI Election Could Flip Supreme Court Control, Musk Jumps In: 'BradCast' 3/10
WI Election Could Flip Supreme Court Control, Musk Jumps In: 'BradCast' 3/10
 VA GOP VOTER REG FRAUDSTER OFF HOOK
VA GOP VOTER REG FRAUDSTER OFF HOOK Criminal GOP Voter Registration Fraud Probe Expanding in VA
Criminal GOP Voter Registration Fraud Probe Expanding in VA DOJ PROBE SOUGHT AFTER VA ARREST
DOJ PROBE SOUGHT AFTER VA ARREST Arrest in VA: GOP Voter Reg Scandal Widens
Arrest in VA: GOP Voter Reg Scandal Widens ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC
ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States'
LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States' 'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States
'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States FINALLY: FOX ON GOP REG FRAUD SCANDAL
FINALLY: FOX ON GOP REG FRAUD SCANDAL COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION
COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL
CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV
Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV  CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM
CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM
CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL
RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV
VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD
RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud
EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud GOP REGISTRATION FRAUD FOUND IN FL
GOP REGISTRATION FRAUD FOUND IN FL


































