READER COMMENTS ON
"National Security Lab Hacks Diebold Touch-Screen Voting Machine by Remote Control With $26 in Computer Parts: My New EXCLUSIVE at Salon"
(48 Responses so far...)
COMMENT #1 [Permalink]
...
Mark E. Smith
said on 9/27/2011 @ 10:50 am PT...
As long as people are willing to vote on insecure systems, they have no leverage to demand secure systems.
COMMENT #2 [Permalink]
...
leftisbest
said on 9/27/2011 @ 11:45 am PT...
Brad - CONGRATULATIONS - You have made the "man-in-the-middle" concept about as clear as it can be made.
Another place where this can take place is on "sleepovers" where the voting machines stay at someone's home or garage for up to 10 days prior to the election, with unlimited time for such "adjustments" to be made.
The ease with which this can be accomplished is quite frightening. And the cost is obviously a non-issue.
You have been fighting for 5 years now to get people to listen to the dangers of e-voting. Having a demonstration by the folks at The Vulnerability Assessment Team (VAT) at the U.S. Dept. of Energy's Argonne National Laboratory adds a degree of credibility that should make everyone stand up and take notice and demand the removal of these non-verifiable machines from the election system.
Thank you for ALWAYS staying on topic with Election Integrity issues, regardless of the political party or affiliation of those driving the train.
COMMENT #3 [Permalink]
...
Dredd
said on 9/27/2011 @ 12:18 pm PT...
"It should really be handled by the Department of Homeland Security"
There is where I would disagree, because they are an essential pillar in this problem, now building a headquarters larger than the Pentagon.
Has anyone stopped to consider that these machines could not have been developed and implemented as the were without "government" approval?
Thus, they server a "government" function.
I will leave it to you to determine what that is, knowing the crisp mental prowess of traditional Brad Blog readers.
COMMENT #4 [Permalink]
...
karenfromillinois
said on 9/27/2011 @ 12:37 pm PT...
handled by homeland security.....or handled by actual moms and dads,grandmas and grandpas in their own precincts with paper and pen and hand counted paper ballots,preferably counted while being live streamed on the net(so anyone with internet can count along with them)
COMMENT #5 [Permalink]
...
Ernest A. Canning
said on 9/27/2011 @ 1:34 pm PT...
Mark E. Smith @1 wrote:
As long as people are willing to vote on insecure systems, they have no leverage to demand secure systems.
"Willing?" You make it sound as if people had a choice as to what type of system they will vote on.
I know, Mark, that your usually stated position is to not vote at all. But I still have a problem ascertaining how that will produce a system where people can vote on hand-marked paper ballots that must be publicly hand-counted at the precinct level.
The way I see it is that the only way to acquire election integrity is demand that those who run for public office commit to it. EI must become a centerpiece issue in every campaign.
COMMENT #6 [Permalink]
...
Mazoola
said on 9/27/2011 @ 1:42 pm PT...
Obviously a threat that can only be addressed by stricter photo-ID requirements.
COMMENT #7 [Permalink]
...
Ernest A. Canning
said on 9/27/2011 @ 1:55 pm PT...
This article should be required reading for every member of the GA Supreme Court.
In rejecting a citizen challenge to the use of the very same 100% unverifiable Diebold DREs that were hacked by remote control by Argonne Labs, the GA Supreme Court in Favorito v. Handel (2009) wrote:
Appellants assert that current implementation of the DRE voting system fails to assure that each vote is accurately counted and, thus, fails to comply with the statutory requirement that "[i]t shall, when properly operated, record correctly and accurately every vote cast."…However, the undisputed evidence shows that the touch-screen machines accurately record each vote when they are "properly operated."
GA a citizens should mount a new legal challenge in which they utilize the services of computer experts from Argonne and Princeton to build a record that will demolish the Orwellian assumption the GA Supremes made in Favorito.
COMMENT #8 [Permalink]
...
Steve Heller
said on 9/27/2011 @ 4:37 pm PT...
Any comments about this latest hack from the corporations bunch of crooks that field these machines?
COMMENT #9 [Permalink]
...
DieboldinDuPage
said on 9/27/2011 @ 5:03 pm PT...
Brad,
How appropriate that this lab located here in DuPage County found flaws in Diebold machines. Our election board ignored the pleas from dozens of citizens urging them not to vote for the flawed Diebold TSx in 2005 because they were inaccurate, unaccountable, non-transparent and not secure. (Many more citizens would have showed up to make public statements but board meetings were always held weekdays when most of us were working.)
The vote for the TSx was 3-0. Citizens were ridiculed by the board in a statement to the press, saying that our concerns were based on rumor and innuendo.
That's before we learned that the election chairman had received thousands of dollars in contributions from the Diebold distributor, including $9,000 toward his lavish retirement party just one year before the vote. We also learned he was/is long personal friends with the distributor.
State's Attorney Joe "Corruption Buster" Birkett did nothing, of course.
Please emphasize that Argonne Lab is in DuPage County --- location of one of the worst places to vote in America. Our votes have been tabulated on Diebold machines for a decade.
And thank you (I guess...) for confirming our worst fears.
COMMENT #10 [Permalink]
...
hankydub
said on 9/27/2011 @ 5:26 pm PT...
There's NOTHING TO SEE HERE. MOVE ALONG NOW. These ARE NOT the droids you're looking for!
COMMENT #11 [Permalink]
...
karenfromillinois
said on 9/27/2011 @ 5:31 pm PT...
COMMENT #12 [Permalink]
...
Marge
said on 9/27/2011 @ 5:50 pm PT...
Now we see how the republicans took the 2010 elections after every one was saying they couldn't. And who knows maybe 2004 also. We can NOT,can NOT trust republicans. The will lie, cheat and steal any election they can, because they know that the majority of people will not vote for them.
COMMENT #13 [Permalink]
...
Botany
said on 9/27/2011 @ 5:53 pm PT...
Brad,
It looks to me that the hardware in the voting machine was designed and installed so as to allow manipulation of the vote
because it is doubtful that is "glitch" just happened to be
in the guts of the machine.
COMMENT #14 [Permalink]
...
Andreas
said on 9/27/2011 @ 8:12 pm PT...
Common knowledge the corporations will defraud
the American voters just to get their way.
About time their CEO's went the way of the
dinosaur.
COMMENT #15 [Permalink]
...
David Lasagna
said on 9/27/2011 @ 9:20 pm PT...
Rachel mentioned Brad and showed his article on the Kochs tonight as she was doing a piece on Christie. She also did a piece on the concerted efforts of Repubs to make it harder to vote. Wish she could take one more step, connect all the dots(like including the above piece),and start talking to Brad about it all. Gotta believe the country is now fed up enough to DO something about our electile dysfunction if knowledge of it can reach some critical mass of public consciousness.
COMMENT #16 [Permalink]
...
David Lasagna
said on 9/27/2011 @ 9:24 pm PT...
Brad's piece here is referenced in one of the rawstory headline stories right now.
COMMENT #17 [Permalink]
...
Brad Friedman
said on 9/27/2011 @ 9:56 pm PT...
David Lasagna, clearly stalking me, said...
Rachel mentioned Brad and showed his article on the Kochs tonight as she was doing a piece on Christie.
Caught after someone shouted out to me on the Twitters. Was a nice mention. I'll try to post it tomorrow if I remember.
She also did a piece on the concerted efforts of Repubs to make it harder to vote. Wish she could take one more step, connect all the dots(like including the above piece),and start talking to Brad about it all.
Funny you put those together. I did too, as I was watching. Thought she might even quote from the Salon story today, but figured that'd be too much "Brad Friedman" citing in a single night over there! 
Brad's piece here is referenced in one of the rawstory headline stories right now.
'Bout time they noticed! 
COMMENT #18 [Permalink]
...
David Lasagna
said on 9/27/2011 @ 10:07 pm PT...
Shit!!!I hadn't realized it until you just said it now. I AM STALKING YOU!!!!OH HOW OH HOW DID IT ALL COME TO THIS????!!!!!!!!!!!I used to be such a regular guy who enjoyed the company of real women in real time and now to be outted like this, stalking a man I've never even met through the ethers of cyberspace. Oh the shame. oh the shame. not to mention the confusion.
Oh well...there're worse things. And I feel better now that it's out in the open.
COMMENT #19 [Permalink]
...
hankydub
said on 9/27/2011 @ 11:16 pm PT...
You're right David Lasagna, there are worse things. You could be Tony Bologna, for instance.
COMMENT #20 [Permalink]
...
steve
said on 9/28/2011 @ 2:08 am PT...
Botany, you are totally onto something there ("machine was designed and installed so as to allow manipulation").
When I was a programmer of embedded systems (things that use a computer but only do one thing, such as a CD player or a voting machine), the Help America Vote Act was passed (as a result of the 2000 Florida chad fiasco), mandating a switch to electronic voting. I instantly saw a very simple design problem and was about to map out a great way to get rich, when I read that Diebold was going to do that, too. Diebold, the maker of 100% verifiable, accurate, and reliable ATMs would get to market a lot quicker than I would. The Princeton expose () showed a machine that I would call an excellent field-serviceable design; IOW, the exact opposite of secure, and quite intentionally done (ie, costs $ to design it like that), and SOME OTHER MANUFACTURERS' MACHINES ARE EVEN BETTER IN THAT RESPECT. And the team demonstrated your worst nightmare - a perfectly thrown election.
COMMENT #21 [Permalink]
...
An Infinitude of Tortoises
said on 9/28/2011 @ 2:26 am PT...
With mass-production, of course, we can expect the price to come down further....
COMMENT #22 [Permalink]
...
David Lasagna
said on 9/28/2011 @ 3:14 am PT...
Why, who's Tony Bologna stalking?
COMMENT #23 [Permalink]
...
CambridgeKnitter
said on 9/28/2011 @ 5:15 am PT...
It seems like a good idea to repeat a comment I made last Sunday in the Elizabeth Warren thread that scrolled past the front page without being seeing by too many people.
So, David Lasagna, KarenfromIllinois and others, I had the tremendous pleasure of meeting Elizabeth Warren today at a tea (not tea party) for her sponsored by the Cambridge Ward 6 Democratic Committee. Scott Brown should be worried. She's articulate and generally well-informed and has a good sense of humor.
On your behalf (and my own, of course), when I got the chance to speak with her, I said the words "election integrity" (after introducing myself as HLS Class of '83 and observing that it was the most woman-hating place I have ever been, including the job I usually describe as akin to working in a men's locker room, to which she nodded). Not only did she understand what I meant, but she told me the very interesting fact that one of her daughters works at Demos, which, among other, mostly economic issues, works on election integrity issues. It looks to me from their website (demos.org) that they get it.
As I said before, Scott Brown should be worried.
COMMENT #24 [Permalink]
...
caseyf5
said on 9/28/2011 @ 6:43 am PT...
Hello Hankydub,
About your comment # 19. How about a nickname for Tony Bologna (thanks Oscar Mayer for the spelling lesson from your commercials). My first choice "Tony Baloney".
COMMENT #25 [Permalink]
...
Randy D
said on 9/28/2011 @ 7:31 am PT...
OK, this experiment shows not only the problem but the only path to a solution. The ONLY way these problems will ever be fixed is to actually put these hacks into action. It would take a techno-civil-disobedience campaign, with principled hackers rigging the vote than confessing afterwards. Perhaps a "Vote Hack" party whose candidate's sole purpose on the ballot is to get votes through hacking. Even if "thwarted" the extra vigilance generated would accomplish the movement's ends...
COMMENT #26 [Permalink]
...
Mitch Trachtenberg
said on 9/28/2011 @ 7:55 am PT...
Brad,
You're doing us all an excellent service by pointing out Roger Johnston's work. Roger Johnston himself should be declared a national treasure.
Any form of voting that does not rely, at bottom, on people submitting sheets of paper that can be hand-counted if necessary is broken by design. The corporations (not to mention the gaggle of academics that condescendingly and disgustingly complain about you behind your back) don't want to admit this.
As Johnston points out, it's a national security issue. It's pointless to protect the nation's nukes if we're going to put in a commander in chief based on the word of Diebold and the status quo crowd.
COMMENT #27 [Permalink]
...
Bret191
said on 9/28/2011 @ 8:27 am PT...
Do you really think this group of individuals wouldn't build in redundancy all the way threw the voting process to make sure the man or woman they want gets elected? Wake up....
This group of thieves have all the money and power in the world to do what they want when they want.
What really astounds me is how easy it is for them to fool everyone!
COMMENT #28 [Permalink]
...
David Lasagna
said on 9/28/2011 @ 8:54 am PT...
Dear Cambridgeknitter @23,
Thank you, thank you for speaking to Elizabeth Warren about election integrity but at this point I don't think we can assume anything about what she knows/believes-doesn't know/doesn't believe about our ridiculously easy to hack voting systems.
I looked at the demos website and found nothing on electronic voting. Stuff on many of the other problems related to voting and the continuing assault by Repubs on our voting rights but nothing on the hackable/error-prone machines. Maybe I missed it but a cursory examination revealed nothing.
This subject and its ramifications, that many of us here feel is THE subject with THE ramifications, seems to be most elusive for people to grock.
Kerry supposedly knows he was robbed but apparently does not get it enough to DO anything about it. He raises no stink. None. Yet, he supposedly has awareness that his election was stolen? What's the thinking/rationale there behind his silence? What concerns might he have that would reasonably outweigh this overt threat to the integrity, the foundation of our democracy?
Kloppenburg seemed to get it but apparently not enough to make a big enough stink to get the vulnerability and unreliability of the machines and the vote counting process the attention required to increase public awareness enough so that we demand change.
These sorts of disconnects are astonishinig to me (for multiple reasons) but we see again and again that you can't make up shit crazier than what people will do or say or believe or ignore.
So we need to have more and deeper conversations with Warren. We have to follow through. We have to keep at it.
It now looks like I may be able to come back to New England soon(but no guarantess so don't count on me). I'll try to find Warren's schedule and if I am back here, see if I can go to one of her little get togethers. It'd be good if many, many of us spoke to her, I'm a thinkin'.
ps--it's probably not necessary but I'll try to contact Sally Castleman at the Election Defense Alliance(EDA) about this Warren opportunity.
COMMENT #29 [Permalink]
...
David Lasagna
said on 9/28/2011 @ 9:14 am PT...
Elizabet Warren has a facebook page and it appears that see actually goes there and writes to people. So I just wrote this to her--
David Lasagna
Dear Elizabeth,
I've been loving you and your efforts for some years now. Here's an article published yesterday at Salon and Bradblog about the severe vulnerabilities in our current voting systems. I hope you will consider making this an issue in your campaign. If we have no reasonable confidence in our election outcomes, what's the point? Best of luck.
https://bradblog.com/?p=8785
COMMENT #30 [Permalink]
...
Bob Kennedy
said on 9/28/2011 @ 10:06 am PT...
There are quite a few holes in this demonstration of hi-jacking an election. Here are a few of them.
1. In GA, the DREs are never left in polling places for days or weeks. They are delivered on Sunday for a Tuesday election. The DREs themselves are enclosed in cases which are sealed and documented. Any broken seals would be seen by the poll workers and that DRE would not be used.
2. Each DRE contains a ballot for the precinct it is being used in. Various precincts have different ballots because of different people running for different offices. The "simple, cheap, man-in-the middle electronics" would have to know which precinct it was being sent to. Difficult if not impossible to do without the help of several election officials in every county.
3. It is impossible for anyone to tamper with the DRE once it is delivered to a precinct, especially on election day.
4. The cost of the electronics may be $26, but the cost for the person is several years in prison when he/she is caught. That is a high price to pay for hi-jacking a county commissioner election.
5. To actually pull this off would require a large conspiracy of election officials either at the county or state or both levels. Large conspiracies are very difficult to pull off successfully.
6. The comment that no one looks inside the units is suspect. In the event a unit malfunctions, a technician would open it up to fix it and would immediately notice the foreign PC board inside. All other units would immediately be checked and verified.
The gentlemen at the VAT managed to hi-jack a DRE when they had plenty of time in the lab. But to achieve the same result in the real world would be nearly impossible. I would challenge them to try to do it in Georgia. I am, confident that the realities of the election process and the security measures would stop them at several points.
Robert Kennedy
Precinct Manager
Fulton County, GA
COMMENT #31 [Permalink]
...
Ernest A. Canning
said on 9/28/2011 @ 10:42 am PT...
Robert Kennedy, Princinct Manager, Fulton County, GA (not to be confused with RFK, Jr.) claims:
It is impossible for anyone to tamper with the DRE once it is delivered to a precinct, especially on election day.
Does "anyone" include "you" or other Election Officials, Robert? Does it include those who service the machine? You know, people with keys, and access.
I do appreciate your willingness to boldly make these claims about the 100% unverifiable Diebold AccuVote TS.
Here's an earlier article that you might wish to peruse.
HACKED: VIRUS IMPLANTED, SPREAD ON DIEBOLD TOUCH-SCREEN VOTING MACHINE!
Felton went on to report that "malicious code could also modify its own tracks [afterwards] and remain virtually undetectable by elections officials."
But then, I'm sure voters can be comforted by the security of a system whose memory card slot can be accessed by "the same key that you may have to open your desk drawer, filing cabinet or even a hotel mini-bar."
COMMENT #32 [Permalink]
...
Mitch Trachtenberg
said on 9/28/2011 @ 10:48 am PT...
Mr. Kennedy,
You suggest an extremely useful challenge. I'd like to think that if you were to provide the folks at the VAT with legal permission to "hack" a real election, they could pull it off without much difficulty.
You might consider directly inviting Dr. Johnston to engage in such an effort, so that you could confirm or reassess your confidence in your procedures.
You could require an invited attack team to file an affidavit prior to the election describing exactly what changes they would attempt to make to the results, perhaps replacing a candidate name with Mickey Mouse, or adding an unreasonably large number to the write-in total (100,000).
If they were unable to accomplish the task, that would be better grounds for confidence in your machines than you have now.
You are probably aware of the embarrassment that the District of Columbia was faced with when they engaged in a test of internet voting, feeling that their system was secure. If not, the results are easily found.
Of course, it's an imposition to keep asking engineers and scientists to form ad hoc teams to demonstrate vulnerabilities. I'd like to think, though, that it would be a useful test to invite someone to attack a system under real world conditions, instead of under test conditions.
COMMENT #33 [Permalink]
...
Ernest A. Canning
said on 9/28/2011 @ 11:02 am PT...
If I dare to modify what I believe was an excellent suggestion by Mitch Trachtenberg @32, Mr. Kennedy, I would propose that, like DC, you stage a mock election and invite both Argonne Labs Roger Johnson, Ph.D. and Princeton's Ed Felton, Ph.D. to attempt a hack.
If you are serious about your challenge, Mr. Kennedy, then give them the same access that election officials have. For election integrity experts and even the CA SoS recognize that the principle security threat comes not from voters but from insiders.
Film it, and we'll publish the results here at The BRAD BLOG.
COMMENT #34 [Permalink]
...
Ernest A. Canning
said on 9/28/2011 @ 11:13 am PT...
COMMENT #35 [Permalink]
...
karenfromillinois
said on 9/28/2011 @ 11:54 am PT...
cambridgeknitter,
ty so much for the report on your meeting ms warren...because candidates have "standing" we really need to educate them early in the process and try and help them be ready for "the long haul"(remember it took franken 8 monthes to gain his senate seat with a hand count after the machines had given it to his opponent)
david,
you had posted a great link to a report on browns "win",could you hard copy that and send it registered mail to ms warren?
COMMENT #36 [Permalink]
...
Brad Friedman
said on 9/28/2011 @ 12:23 pm PT...
Bob Kennedy (Fulton County, GA Precinct Manager) @ 30:
Thanks for your thoughts and critiques below. Though both Ernie Canning and Mitch Trachtenberg (who, by the way, knows a thing or two about vulnerabilities and failures in Diebold technology --- look him up) spoke to some of your points, I'd like to offer a few additional thoughts of mine. I hope you will speak to the responses they took the time to offer you as well, however. Where my points overlap with points that Ernie and/or Mitch made, please forgive. I'll do my best to limit that.
I appreciate that, as you say, you are merely a "Precinct Manager" in Fulton County, GA. And, as such, do not likely have either the insight or technical knowledge as to how these systems actually work (or don't.) Also, that while you have some special access to the systems, you don't have the same kind of access that higher ranking officials and/or voting machine company employees would have. So my responses are offered with that in mind...
There are quite a few holes in this demonstration of hi-jacking an election. Here are a few of them.
1. In GA, the DREs are never left in polling places for days or weeks. They are delivered on Sunday for a Tuesday election. The DREs themselves are enclosed in cases which are sealed and documented. Any broken seals would be seen by the poll workers and that DRE would not be used.
So there are some 48 hours in GA to make the modifications required by the Argonne attack at the precincts in GA...the modifications that are shown as taking about 2 minutes or so in their video demonstration. Got it. That, of course, does not count the time that the machines are in transport to the precinct, when nobody at all is watching, or the time spent during programming prior to the election, or the weeks, months, and years the machines spend sitting in a warehouse between each election.
I'll not get into specifics here, but as to your seals comment, most "seals" used on Diebold DREs have been shown to be easily defeated without probability of detection. But for brute force defeat of those seals --- and of the election held at your precinct --- you suggest all that needs to be done is for someone to violate the seals and/or the cases of every machine at your precinct in the 48 hours they're sitting unguarded at the precinct. How long will it take to replace all of those machines on Election Day when the violations are discovered? And how many extra machines does your county have in the event that, say, the same thing happens at about 10 or 20 different precincts out there?
Has any of this become a problem yet, as I describe it, for an election in your county?
2. Each DRE contains a ballot for the precinct it is being used in. Various precincts have different ballots because of different people running for different offices. The "simple, cheap, man-in-the middle electronics" would have to know which precinct it was being sent to. Difficult if not impossible to do without the help of several election officials in every county.
Does anything stop someone like, say, you from carrying out that attack? If you're in the precinct all day, you could certainly man that remote control, I suspect, without much possibility of detection.
Furthermore, as noted in the video, not all races need be affected. Perhaps just the ones that are in the same ballot position across the entire county.
And finally, presuming your assertion is accurate that none of this could be done "without the help of several election officials in every county," how are we to know that wasn't the case? As in what happened in Clay County, KY for years on end, election after election, with the County Clerk, the circuit court judge, the county school superintendent, virtually every member of the election board and many of the Precinct Judges in on the conspiracy, which was carried out on very similar DRE systems?
3. It is impossible for anyone to tamper with the DRE once it is delivered to a precinct, especially on election day.
"Impossible" is a word I'd not recommend using here. Other officials have done so, and come to regret that. I'll not bother you with the links here. But, suffice to say, you are a) wrong. And b) able to tamper with the machines yourself if you like, as you probably know.
4. The cost of the electronics may be $26, but the cost for the person is several years in prison when he/she is caught. That is a high price to pay for hi-jacking a county commissioner election.
Of course, it happens all the time. And the hi-jacking neednt' be simply for a county commissioner election, either. Nonetheless, given the amount of money that stands to be made --- often millions, sometimes, billions --- from such an election, and given the extremely low probability of detection in hacks like the one detailed by Argonne, your optimism there is...um...charming. 
5. To actually pull this off would require a large conspiracy of election officials either at the county or state or both levels. Large conspiracies are very difficult to pull off successfully.
They are. Thought they are frequently carried out. In this case, however, a large conspiracy is not actually required at all.
6. The comment that no one looks inside the units is suspect. In the event a unit malfunctions, a technician would open it up to fix it and would immediately notice the foreign PC board inside. All other units would immediately be checked and verified.
It's "suspect"??? Actually, it's accurate. As this hack does not need to offer any clues to any voter or poll worker that the machine has malfunctioned, why would a tech bother to open it up?
Furthermore, in the event that they did --- and that is exceedingly rare --- a) if you note in the video, the chip can be miniaturized so it's extremely unlikely to be noticed at all, b) Even not miniaturized, there's a good chance technicians would not notice anything unusual on the hardware and c) Even if they did, it would be very very difficult, if not impossible, to determine who did the attack, and how many other machines were also affected, without stopping the election cold in its tracks across the entire county/state.
The gentlemen at the VAT managed to hi-jack a DRE when they had plenty of time in the lab. But to achieve the same result in the real world would be nearly impossible.
Again, I'd be careful with that word "impossible."
I would challenge them to try to do it in Georgia. I am, confident that the realities of the election process and the security measures would stop them at several points.
Others spoke to that, so I'll leave it alone. Suffice to say, you don't really mean to issue that "challenge".
Finally, as I'll be having Dr. Johnston on the radio with me both today (on KPFK/Pacifica) and likely next week on the nationally syndicated Mike Malloy Show, I'd welcome you, if interested, to come on the air as well to discuss the "holes" you see in either my reporting, or in the Argonne attack, if you'd like. If so, I can be reached via email here, if you're interested.
COMMENT #37 [Permalink]
...
David Lasagna
said on 9/28/2011 @ 12:30 pm PT...
Karen,
Just got an address from her website that I could send it to. Thanks. But I'm a little wary of trusting something sent in the mail to get the information through. I once handed Phil Donahue a copy of UnCounted. When Howard Dean was running for president I handed him a copy of the Eqbal Ahmad tape on terrorism after I performed at a benefit for him. In neither case did I ever see any evidence later that anything had been checked out. That's why, though I guess it couldn't hurt to send her a copy through her campaign, I'll also try to see here and talk to her and have a copy to hand to her in person, if possible.
COMMENT #38 [Permalink]
...
Grizzly Bear Dancer
said on 9/28/2011 @ 7:56 pm PT...
Thanks Brad for doing an outstanding job on putting this information out and your other valuable work. My band just released a record called Captured American Flag Displayed Upside Down and in the liner notes, this is 1 of the issues American people need to get shored up to have transparency of their election system.
Electronic computer voting machines CANNOT produce a paper ballot trail so there is nothing to count, and voters have to trust an election official to tell them their results.
Of course there has been no outrage by the leadership of the 2 party dictatorship in this country who serve the corporate elite let alone the corporate mass media because as long as they can get away with it, it's too easy to rig an election and put their robots into office.
Arrrgh website is www.kabong.co if you want to check it out.
COMMENT #39 [Permalink]
...
Bob Kennedy
said on 9/28/2011 @ 9:34 pm PT...
To Brad and the other responders to my comments:
I created a response to Mr. Canning's comments, but lost it when I did not include my name and email at the beginning. Won't do that again. So I will respond to Brad's comments and hopefully cover the questions from the others as well.
So there are some 48 hours in GA to make the modifications required by the Argonne attack at the precincts in GA...the modifications that are shown as taking about 2 minutes or so in their video demonstration. Got it.
In my precinct and I suspect in most others, the units are inside a facility with alarm systems. So to access the units you would also need to defeat the alarms. We have 10 units in our place, other larger precincts may have 15-20 or more. So your two minutes becomes 20 minutes in my precinct. Then add additional time to circumvent the seals on the cases.
Concerning the seals, if the seals we use can be defeated then the elections official need to replace them with more secure types.
If one or two of our units were tampered with, they would be set aside and not used. It would take some amount of time to replace all of our units if all of the seals were broken. But we have a paper ballot backup procedure which covers the situation where all the units are not useable. Obviously the voting would slow down dramatically, but the integrity of the voting is paramount.
Does anything stop someone like, say, you from carrying out that attack? If you're in the precinct all day, you could certainly man that remote control, I suspect, without much possibility of detection.
Yes, I could operate the remote during the voting, but that assumes that I am part of a team one of which has installed the electronics inside the units. And yes, I could have access to the units during the hours before the election, but that assumes that the seals can be tampered with.
I agree "impossible" should be replaced with Highly improbable or Extremely difficult.
Furthermore, as noted in the video, not all races need be affected. Perhaps just the ones that are in the same ballot position across the entire county.
From my experience there can be a very large number of differences between precincts within a county. Only the presidential and senatorial choices would probably be in the same position on all ballots. Even the congressional races could be different in different parts of a county, since districts cross county lines.
As in what happened in Clay County, KY for years on end, election after election, with the County Clerk, the circuit court judge, the county school superintendent, virtually every member of the election board and many of the Precinct Judges in on the conspiracy, which was carried out on very similar DRE systems?
Election officials at this high level could tamper with election results regardless of the system used. It happened for decades when paper ballots were used. It does not require a DRE to be a corrupt official.
It's "suspect"??? Actually, it's accurate. As this hack does not need to offer any clues to any voter or poll worker that the machine has malfunctioned, why would a tech bother to open it up?
My point here was that prior to the election, any unit could fail for any reason causing a technician to open up the unit. The Argonne hack is very obvious to any knowledgeable tech. If the hack was found in one unit all other unit would be inspected. Yes it would be a big job, but it would be done.
It also may be standard pre-election procedure to open all units to test and verify them.
Even if they did, it would be very very difficult, if not impossible, to determine who did the attack,
There is that word "impossible"... from your side. lol
I sent this response late this afternoon, but it apparently got lost somewhere. So here it is again. Will continue tomorrow if there is interest.
Bob Kennedy
COMMENT #40 [Permalink]
...
David Lasagna
said on 9/28/2011 @ 10:12 pm PT...
Well maybe it's just me being bad at computers and not understanding facebook but I just went back to Elizabeth Warren's facebook page to see if she'd responded to my comment that included a link to this article and couldn't find my comment.
Sigh.......
Sometimes(like this second)I wonder in pain and frustration how the fuck one would ever want to help ANY politician when none of them seem capable of even acknowledging that these fundamental election integrity issues exist.
Feels sorta like I'd immediately be being required to not know or care about what for me is the primary number one gotta start there issue.
That don't feel right.
COMMENT #41 [Permalink]
...
freedomlover
said on 9/28/2011 @ 10:50 pm PT...
If someone with an 8th grade science education can making a $26 device than can manipulate a voting machine that I'm sure costs A LOT MORE than $26, you have to wonder about the mentality of the people that run Diebold (and other "businesses" like them).
In Corporate America we trust... NOT!
COMMENT #42 [Permalink]
...
Brad Friedman
said on 9/28/2011 @ 11:01 pm PT...
Bob Kennedy @ 39:
Much appreciate your responses here, and I'm sorry about whatever happened to your initial attempts at responding!
My responses to yours...
In my precinct and I suspect in most others, the units are inside a facility with alarm systems. So to access the units you would also need to defeat the alarms. We have 10 units in our place, other larger precincts may have 15-20 or more. So your two minutes becomes 20 minutes in my precinct. Then add additional time to circumvent the seals on the cases.
Of course, as discussed there are 48 hours where the machines are left alone in your precinct, as you conceded. So that's plenty of time. As well, I also mentioned the time in transit, the time during programming before the election, and the months and years in between in the storage warehouse which you didn't speak to.
What facility is that you use which has an alarm as in inaccessible by any humans for two full days before the election?
Concerning the seals, if the seals we use can be defeated then the elections official need to replace them with more secure types.
As Roger Johnston of Argonne Labs explained to me, the boxes are not designed for security seals at all. At best, they're using after market seals, all of which have been defeated in some fashion in the past. "More secure types"? What are they?
While I'm happy to hear there is some interest in security there, if there was really such interest, you wouldn't be using these machines at all, given all that we've learned about them over the years. The Argonne hack is just the latest (and a different type of) attack. You may wish to go back to the Diebold Princeton Virus Hack to get an idea of a more direct way to flip an entire election, over an entire county, with little possibility of detection.
Or, you could just speak to some of the Diebold folks who originally installed those systems in Georgia and hear what they have to say about them, and about Diebold's "security". Do a search for "Dieb-throat" and you'll find plenty, going all the way back to 2005.
And, of course, there is the little problem that it's strictly impossible for you --- or anybody else - to prove that any vote ever cast on one of your Diebold systems during any election for any candidate or initiative on the ballot has ever been recorded accurately as per any voter's intent.
I'm sure one must have been, but there is no evidence of such. That, in and of itself, is a grave threat to democracy, as I'd think many of Georgia's voters would tell you.
If one or two of our units were tampered with, they would be set aside and not used. It would take some amount of time to replace all of our units if all of the seals were broken.
Right. You all would be in big trouble.
But we have a paper ballot backup procedure which covers the situation where all the units are not useable. Obviously the voting would slow down dramatically, but the integrity of the voting is paramount.
1) The voting would speed up dramatically. If you think touch-screen voting is faster, I'd love to read where you are getting that statistic from. More voters could vote much quicker, reducing lines for all. 2) I assume that means you have enough paper ballots in your precinct to let every voter vote on one, right? 3) Begging the question as to why you'd spend the extra money/expense on DREs and not just let voters vote verifiably in the first place.
I could operate the remote during the voting, but that assumes that I am part of a team one of which has installed the electronics inside the units.
You could be both the person who installed the chip and who operates the remote. But if you read the article and/or watch the video, you know that the remote is not necessary. It just makes the attack more fun. Can be turned on and off by timer, or any other number of triggers.
And yes, I could have access to the units during the hours before the election, but that assumes that the seals can be tampered with.
They can. It also assumes that the insertion of the chip is done after the seals are applied. Not a very safe assumption.
Election officials at this high level [Clay County, KY] could tamper with election results regardless of the system used. It happened for decades when paper ballots were used. It does not require a DRE to be a corrupt official.
Actually, it was in the precincts themselves that those officials flipped the votes of voters after they'd left the DRE. Of course, that's cause those officials weren't particularly bright. They coulda had one guy just change the results at the central tabulator.
In any case, if paper ballots are counted publicly, at the precinct level, in front of all parties and video cameras, on Election Night, with results posted before ballots are moved anywhere, it's exceedingly difficult to tamper with a paper ballot election. At least not without getting caught. You may wish to watch my "Democracy's Gold Standard" video here. May be informative.
My point here was that prior to the election, any unit could fail for any reason causing a technician to open up the unit. The Argonne hack is very obvious to any knowledgeable tech.
No. It isn't. As noted in their demo video, the chip can be miniaturized making it next to impossible to notice on the very off chance that anybody ever looked inside. If you look at their Sequoia DRE hack, they explain how the chip would be virtually invisible if they wanted it to be.
It also may be standard pre-election procedure to open all units to test and verify them.
It isn't.
Again, I thank you much for your willingness to discuss this issue here. Too many election officials simply won't. That said, you may wish to do some reading up on the machines you're using out there, and the very well known concerns about them from world-class computer scientists and security experts across the globe, for years now on end. That you folks have been so bamboozled out there by disinformation from the vendors is, to say the least, troubling. But, unfortunately, it's not much of a surprise here anymore.
Please let me know if you have any questions as you research the facts behind the 100% unverifiable voting systems that GA forces folks to vote on. You've got my email address, so I'm happy to chat via email, off-record, if you find that may be helpful.
COMMENT #43 [Permalink]
...
Gordon Peterson
said on 9/29/2011 @ 12:43 pm PT...
We could waste a lot of time arguing about whether it is conceivably possible to hack computer-based voting machines, but the fact remains that it's far (far!) easier to simply change the totals on the (one!) computer at the county or state level where the totals are tallied. This is immaterial to whether paper ballots are used, or whether Diebold or ESS or other equipment was used in the polling places.
So if you really want to have secure, robust, trustworthy elections, it's not helpful to worry so much about where the problems probably aren't, while ignoring where the problems are far more likely to happen (as we saw in Ohio in 2004, when Ohio suddenly and inexplicably saw Kerry's vote total GO DOWN, throwing the election to Shrub.
In a county where we have on the order of 500 polling places, it's ridiculous to hypothecate on having television news crews at each polling place filming as the votes (on hand-marked, hand-counted paper ballots) are being tallied by hand.
There ARE ways to make reliable, robust, trustworthy elections... but key to that involves having the precinct polling location judges handing duplicate signed/certified results tapes to representatives of at least both major parties at the same time they deliver results to the county or other election authority. This allows the parties to INDEPENDENTLY tally the totals (county wide, and eventually state-wide) and obviously the totals THEY get ought to match the totals the county and state report... and if not, the reason for the discrepancy needs to be studied.
Another key issue is that if ballots are hand-marked, it's easy at any later stage for additional stray marks or votes to be added by anyone having access to those ballots. (A typical example might be adding a crossover vote where the original voter had made a single "X" indicating a straight party vote). Clearly a public hand-count before the ballots leave the polling place would make such tampering difficult, but it still makes the enduring value of those ballots questionable in the event of a further recount some days or weeks later. And in the event of tampering, it could never be determined who tampered with them, or what the correct totals should be.
A better solution is a first-level system (perhaps a touchscreen system) which prints a (perhaps scannable) TAMPER-PROOF paper ballot, using micro-printing and other security techniques which would make it essentially impossible to change the marks or add additional marks afterwards. The voter would then confirm that the printed, tamper-proof, machine-marked paper ballot matched their selections before depositing it. This way, there would be no less than THREE separate sets of totals... the totals from the first-stage system (the one that printed the tamper-proof ballots), and the tamper-proof paper ballots, and the total from whatever system(s) counted those paper ballots. Again, all three independent counts would need to agree, or an investigation opened into what caused the discrepancy.
Using a good touchscreen system to print tamper-proof marked paper hardcopy ballots has the additional great advantage that it can prevent overvotes, and warn the voter about inadvertent undervotes (e.g. when a voter votes a straight party ticket without noticing that they didn't express a preference for a downticket race, where their chosen party might not have a candidate running, but where the voter might have wished to express a preference from among the candidates of the other parties).
This approach also prevents the production of ambiguously marked ballots, as we saw in the Minnesota senate race.
COMMENT #44 [Permalink]
...
Brad Friedman
said on 9/29/2011 @ 7:16 pm PT...
Gordon Peterson @ 43:
Your comments are, um, unfortunate and display an extraordinary level of misunderstanding of all manner of things. Or worse.
I'll do my best to reply soon. Sorry I don't have the time to do so at the moment. Hope too soon.
COMMENT #45 [Permalink]
...
Chris Hooten
said on 9/30/2011 @ 2:32 pm PT...
Tony Baloney
Has a chile demeanor
towards some women
COMMENT #46 [Permalink]
...
Larry Bergan
said on 9/30/2011 @ 9:33 pm PT...
The machines are working as designed. 
COMMENT #47 [Permalink]
...
Brad Friedman
said on 10/1/2011 @ 10:25 pm PT...
Gordon Peterson @ 43 said:
In a county where we have on the order of 500 polling places, it's ridiculous to hypothecate on having television news crews at each polling place filming as the votes (on hand-marked, hand-counted paper ballots) are being tallied by hand.
"Hypothecate"? I don't think that means what you think it means.
In any event, I'm told that it's not only "television news crews" who have access to those video cameras these days. Some of the kids even have them right on their telephones, if you can believe it!
Of course, while video cameras are most welcome (and ubiquitous), they are not necessary to ensure a properly overseen, public, precinct-based hand-count.
There ARE ways to make reliable, robust, trustworthy elections... but key to that involves having the precinct polling location judges handing duplicate signed/certified results tapes to representatives of at least both major parties at the same time they deliver results to the county or other election authority. This allows the parties to INDEPENDENTLY tally the totals (county wide, and eventually state-wide) and obviously the totals THEY get ought to match the totals the county and state report... and if not, the reason for the discrepancy needs to be studied.
Wow. Sounds like a really swell way to bring chaos to an election, and plunge its results into question!
So if the tallies don't match, who has it right? And whose to say they haven't gamed the ballots in the meantime! That's one of the worst ideas for tallying elections I've heard to date, Gordon...with all due respect, of course.
Another key issue is that if ballots are hand-marked, it's easy at any later stage for additional stray marks or votes to be added by anyone having access to those ballots.
Right. Which is why they need to be hand-counted immediately, in front of the public, all parties and even some of the high-falootin' "video cameras" if we can trick a television station to bring one over. With results agreed upon and posted publicly at the precinct, decentralized, it doesnt matter what someone might try to get away with later. It'd be too late!
Clearly a public hand-count before the ballots leave the polling place would make such tampering difficult, but it still makes the enduring value of those ballots questionable in the event of a further recount some days or weeks later.
That problem exists with any system, which is why a secure chain of custody remains important. But your method doesn't solve that concern either.
A better solution is a first-level system (perhaps a touchscreen system) which prints a (perhaps scannable) TAMPER-PROOF paper ballot, using micro-printing and other security techniques which would make it essentially impossible to change the marks or add additional marks afterwards.
Oy. More Mack trucks for delivering pizzas?
And how can anybody know after the election if what was printed was what the voter intended? You are familiar, for example, with the Rice University study showing that of those who did check their summaries at the end of electronic voting (most don't), some two-thirds of them didn't notice when the computer had flipped their vote?
Your system doesn't seem to take that in mind. And, of course, even if they did notice vote flips, how does the public know that anybody did?
Sigh...
The voter would then confirm that the printed, tamper-proof, machine-marked paper ballot matched their selections before depositing it.
And if they don't? Or can't? Or if they do, how do we know?
This way, there would be no less than THREE separate sets of totals... the totals from the first-stage system (the one that printed the tamper-proof ballots), and the tamper-proof paper ballots, and the total from whatever system(s) counted those paper ballots. Again, all three independent counts would need to agree, or an investigation opened into what caused the discrepancy.
Oy. I'll not bother with responding to the rest. The answers are the same. Bad ideas, Gordon. For reasons we've known for years. Sorry. Your pizza is on its way. The huge 18-wheeler will be in your driveway at any minute with it.
But I can't help but respond to this one last...
This approach also prevents the production of ambiguously marked ballots, as we saw in the Minnesota senate race.
Right. It makes every ballot ambiguous. With no way to know if any of them actually reflect the intent of any voter.
Thanks, though, for trying.
COMMENT #48 [Permalink]
...
Eric
said on 10/13/2011 @ 8:15 pm PT...
Hello,
I found the machine tampering videos interesting (though the silly music and graphics make them seem somewhat less serious). A few quick comments:
On the Diebold hack, the parts may be cheap but the skill required to program a microprocessor-driven circuit is beyond simple hobbyists. It also requires some knowledge of what is happening on the data lines that are being interrupted. Obviously doable by a skilled hacker with bad intent, but it's harder than the mods on the earlier machine--which were essentially crossing switch and lamp wires via relays.
I have been a poll judge for a few years in Maryland and I concur with Mr. Kennedy that actually making these mods to a significant number of machines across a large range of jurisdictions would be quite difficult. There are a variety of arcane security measures that we must follow in handling the machines (and now I understand why).
It would require a substantial conspiracy involving large numbers of dishonest people to circumvent enough security to do any real damage. Of course this is *possible*, but not very likely. Going inside thousands of voting machines just seems too difficult and risky. I tend to think that more effective fraud could be perpetrated using manipulation where data is centrally collected.
That being said, I don't doubt there are security problems with the whole damn system and money is a very powerful agent of change.
 The Vulnerability Assessment Team (VAT) at the U.S. Dept. of Energy's Argonne National Laboratory in Illinois has managed to hack a Diebold Accuvote touch-screen voting machine in what I describe at my exclusive today at Salon as perhaps "one of the most disturbing e-voting machine hacks to date."
The Vulnerability Assessment Team (VAT) at the U.S. Dept. of Energy's Argonne National Laboratory in Illinois has managed to hack a Diebold Accuvote touch-screen voting machine in what I describe at my exclusive today at Salon as perhaps "one of the most disturbing e-voting machine hacks to date." Add an optional $15 radio frequency remote control device, and votes can be changed, without the knowledge of the voter, from up to half a mile away. Without the remote, the attack can be turned on and off at certain times, or by other triggers. The voter would have no idea that their votes have been changed after they've already approved them as "correct" on the various confirmation screens, and even on the so-called "paper-trail" (on e-voting machines which offer them --- though VAT has learned how to manipulate those as well, see photo at right.)
Add an optional $15 radio frequency remote control device, and votes can be changed, without the knowledge of the voter, from up to half a mile away. Without the remote, the attack can be turned on and off at certain times, or by other triggers. The voter would have no idea that their votes have been changed after they've already approved them as "correct" on the various confirmation screens, and even on the so-called "paper-trail" (on e-voting machines which offer them --- though VAT has learned how to manipulate those as well, see photo at right.)

 Vets Push Back at Trump, Musk Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25
Vets Push Back at Trump, Musk Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25 'Green News Report' 3/27/25
'Green News Report' 3/27/25
 Signal Scandal Worsens for Trump, GOP; Big Election Victories for Dems in PA: 'BradCast' 3/26/25
Signal Scandal Worsens for Trump, GOP; Big Election Victories for Dems in PA: 'BradCast' 3/26/25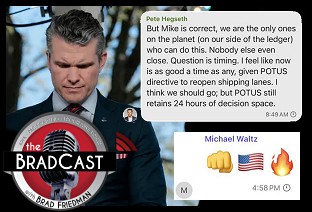 'Emptywheel' on Why Trump NatSec Team Should 'Resign in Disgrace' After Signal Chat Debacle: 'BradCast' 3/25/25
'Emptywheel' on Why Trump NatSec Team Should 'Resign in Disgrace' After Signal Chat Debacle: 'BradCast' 3/25/25 'Green News Report' 3/25/25
'Green News Report' 3/25/25 Postal Workers Union Prez: USPS 'Belongs to the People, Not the Billionaires':
Postal Workers Union Prez: USPS 'Belongs to the People, Not the Billionaires': Sunday 'Suddenly Conceivable' Toons
Sunday 'Suddenly Conceivable' Toons We're ALL Voice of America Now: 'BradCast' 3/20/25
We're ALL Voice of America Now: 'BradCast' 3/20/25 'Green News Report' 3/20/25
'Green News Report' 3/20/25 What Trump's 'Timber Production Expansion' Means (and Costs): 'BradCast' 3/19/25
What Trump's 'Timber Production Expansion' Means (and Costs): 'BradCast' 3/19/25 Courts Largely Holding Against Trump, Musk Lawlessness: 'BradCast' 3/18/25
Courts Largely Holding Against Trump, Musk Lawlessness: 'BradCast' 3/18/25 'Green News Report' 3/18/25
'Green News Report' 3/18/25 Chief VOA Reporter on Outlet Falling Silent First Time Since 1942: 'BradCast' 3/17/25
Chief VOA Reporter on Outlet Falling Silent First Time Since 1942: 'BradCast' 3/17/25 Sunday 'The Usual' Toons
Sunday 'The Usual' Toons 'Green News Report' 3/13/25
'Green News Report' 3/13/25 Trump EPA Unveils Plans to Endanger, Sicken Americans: 'BradCast' 3/13/25
Trump EPA Unveils Plans to Endanger, Sicken Americans: 'BradCast' 3/13/25 Trump Nixed Enforce-ment Against 100 Corp. Lawbreakers: 'BradCast' 3/12/25
Trump Nixed Enforce-ment Against 100 Corp. Lawbreakers: 'BradCast' 3/12/25 Bad Day for 'Strongmen': 'BradCast' 3/11
Bad Day for 'Strongmen': 'BradCast' 3/11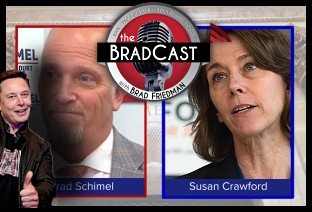 WI Election Could Flip Supreme Court Control, Musk Jumps In: 'BradCast' 3/10
WI Election Could Flip Supreme Court Control, Musk Jumps In: 'BradCast' 3/10 'What Else Could a Russian Asset Do That Trump Hasn't?': 'BradCast' 3/6/25
'What Else Could a Russian Asset Do That Trump Hasn't?': 'BradCast' 3/6/25 The Longest, Dullest, Most Lie-Filled 'SOTU' Ever: 'BradCast' 3/5/25
The Longest, Dullest, Most Lie-Filled 'SOTU' Ever: 'BradCast' 3/5/25 Trump Bad for Biz... and Farmers... and Nat'l Parks... and...: 'BradCast' 3/4/25
Trump Bad for Biz... and Farmers... and Nat'l Parks... and...: 'BradCast' 3/4/25 Trump Targeting 50% Cuts, Office Closures at Social Security: 'BradCast' 3/3/25
Trump Targeting 50% Cuts, Office Closures at Social Security: 'BradCast' 3/3/25
 VA GOP VOTER REG FRAUDSTER OFF HOOK
VA GOP VOTER REG FRAUDSTER OFF HOOK Criminal GOP Voter Registration Fraud Probe Expanding in VA
Criminal GOP Voter Registration Fraud Probe Expanding in VA DOJ PROBE SOUGHT AFTER VA ARREST
DOJ PROBE SOUGHT AFTER VA ARREST Arrest in VA: GOP Voter Reg Scandal Widens
Arrest in VA: GOP Voter Reg Scandal Widens ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC
ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States'
LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States' 'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States
'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States FINALLY: FOX ON GOP REG FRAUD SCANDAL
FINALLY: FOX ON GOP REG FRAUD SCANDAL COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION
COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL
CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV
Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV  CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM
CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM
CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL
RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV
VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD
RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud
EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud GOP REGISTRATION FRAUD FOUND IN FL
GOP REGISTRATION FRAUD FOUND IN FL


































