Regarding voting, this may be the biggest outrage you have ever read:
"13. ABasic Files. AccuBasic report files are used to configure AccuVote-OS and AccuVote-TS report contents and printing in precinct count mode. They are actually loaded into the memory cards for the AV-OS and AV-TS where their logic is executed. There are 24 report files supporting modifications to the reports for different states and jurisdictions. A few of these may provide options that are attractive to local jurisdictions as they provide variations on what summary reports are printed optionally or automatically and the order they are prepared. At the current time, the Federal testing only uses one of these files and does no source code review, leaving this to the states to verify. Within our state testing, we only verified the reports for the same file, 194US.abo, revision 1.15, and have checked the source files. Since the source file is not reviewed in the Federal testing, we have no absolute verification that the installed file found in the witnessed build (forwarded by Ciber) was created from these source files but signature information in the .abo file matches what would be expected from the source file.
The source code I was given clearly does not directly affect stored votes or even the voting result content of the reports. It just sets up the report options that will be available to the operator and some operator display information that sets up the options. The .abo file given is without risk to the election results.
The actual file used is selected in the AV-OS Options window of GEMS from the pulldown list in the Report field so the local user could potentially select any of these files or a modification of that file. The risk occurs in the opportunity to replace the verified file with some other .abo file (prior version, one the other existing versions installed in the GEMS/ABASIC directory, or by replacing the current code with rewritten code performing other operations.) In a certification report last year, we recommended that the unverified report files be deleted from the GEMS directory leaving only the verified files. The California Use Procedures should specify which files are approved for use and provide information so that the approved files may be verified.
This comes directly from Josh Washburn, Jim March of Black Box Voting.
It shows that any file in these Diebold machines whether they be touch-screen or optical scan, can be replaced with another file of executable code. And it is hidden straight in the .abo file, no actual encryption needed!!!
You heard me right....this file could be replaced with Clint Curtis source code obviously, or any known exploit already being used in the voting. And NOBODY would know about it because nobody would check the file extensions of the *.abo code whatsoever and wouldn't be able to match any of the results...
Dr. Washburn, with the help of Dr. Thompson proved this to the point it can stand up in court.
ES&S and probably Sequoia have similar architecture. Diebold is who invented this architecture.
It is NOT sloppy, it is deliberately put there so executable code such as "vote switch" or "VB script" can be written in.
This was no mistake, these programmers are nothing but crooks who had malicious intentions to begin with. DIEBOLD the entire company should be prosecuted for this, and as for the Sequoia company, if its proven they have the same code we need to take this into the COURTS!!!!!!!!!!
Doug E.
 North Carolina counties continue to meet and make their selections of voting machines for the future. Unfortunately they cannot wait until a decision from the court on whether any voting system presently certified by the state board of elections can, by law, be considered to be certified. The state is certainly doing nothing to stop the counties from making their decisions....
North Carolina counties continue to meet and make their selections of voting machines for the future. Unfortunately they cannot wait until a decision from the court on whether any voting system presently certified by the state board of elections can, by law, be considered to be certified. The state is certainly doing nothing to stop the counties from making their decisions....

 Sunday 'Zero Day' Toons
Sunday 'Zero Day' Toons Soc. Sec. Expert Warns DOGE Hastening Collapse, Privati-zation: 'BradCast' 4/10/2025
Soc. Sec. Expert Warns DOGE Hastening Collapse, Privati-zation: 'BradCast' 4/10/2025 'Green News Report' 4/10/25
'Green News Report' 4/10/25
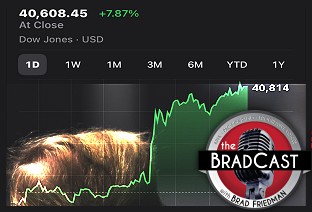 Trump Blinks, Chaos Reigns, Markets Spike as Many Tariffs Remain Despite 90-Day 'Pause': 'BradCast' 4/9/25
Trump Blinks, Chaos Reigns, Markets Spike as Many Tariffs Remain Despite 90-Day 'Pause': 'BradCast' 4/9/25 SCOTUS Deportation Ruling Grimmer Than First Appears: 'BradCast' 4/8/25
SCOTUS Deportation Ruling Grimmer Than First Appears: 'BradCast' 4/8/25 'Green News Report' 4/8/25
'Green News Report' 4/8/25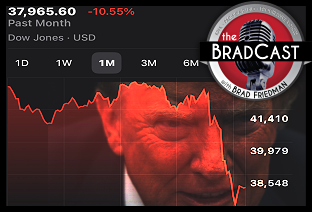 Cliff Diving with Donald: 'BradCast' 4/7/25
Cliff Diving with Donald: 'BradCast' 4/7/25 Sunday 'Don't Look Down' Toons
Sunday 'Don't Look Down' Toons 'Green News Report' 4/3/25
'Green News Report' 4/3/25 'Mob Boss' Trump's Trade Sanctions Tank U.S., World Markets: 'BradCast' 4/3/25
'Mob Boss' Trump's Trade Sanctions Tank U.S., World Markets: 'BradCast' 4/3/25 Crawford Landslide in WI; Booker Makes History in U.S. Senate: 'BradCast' 4/2/25
Crawford Landslide in WI; Booker Makes History in U.S. Senate: 'BradCast' 4/2/25 Judge Ends Challenge to GA's Unverifiable, Insecure Vote System: 'BradCast' 4/1/25
Judge Ends Challenge to GA's Unverifiable, Insecure Vote System: 'BradCast' 4/1/25 Bad Court, Election News for Trump is Good News for U.S.: 'BradCast' 3/31
Bad Court, Election News for Trump is Good News for U.S.: 'BradCast' 3/31 Vets Push Back at Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25
Vets Push Back at Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25 Signal Scandal Worsens for Trump, GOP; Big Dem Election Wins in PA: 'BradCast' 3/26
Signal Scandal Worsens for Trump, GOP; Big Dem Election Wins in PA: 'BradCast' 3/26 'Emptywheel': Trump NatSec Team Should 'Resign in Disgrace': 'BradCast' 3/25/25
'Emptywheel': Trump NatSec Team Should 'Resign in Disgrace': 'BradCast' 3/25/25 USPS 'Belongs to the People, Not the Billionaires': 'BradCast' 3/24/25
USPS 'Belongs to the People, Not the Billionaires': 'BradCast' 3/24/25
 VA GOP VOTER REG FRAUDSTER OFF HOOK
VA GOP VOTER REG FRAUDSTER OFF HOOK Criminal GOP Voter Registration Fraud Probe Expanding in VA
Criminal GOP Voter Registration Fraud Probe Expanding in VA DOJ PROBE SOUGHT AFTER VA ARREST
DOJ PROBE SOUGHT AFTER VA ARREST Arrest in VA: GOP Voter Reg Scandal Widens
Arrest in VA: GOP Voter Reg Scandal Widens ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC
ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States'
LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States' 'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States
'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States FINALLY: FOX ON GOP REG FRAUD SCANDAL
FINALLY: FOX ON GOP REG FRAUD SCANDAL COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION
COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL
CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV
Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV  CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM
CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM
CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL
RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV
VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD
RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud
EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud GOP REGISTRATION FRAUD FOUND IN FL
GOP REGISTRATION FRAUD FOUND IN FL


































