Transcript of sworn testimony by computer programmer Clint Curtis, before the U.S. HOUSE OF REPRESENTATIVES Democrats of the Judiciary Committee, December 13, 2004, as seen on video above follows below.
For the full compendium of our Clint Curtis/Tom Feeney vote-rigging scandal, which we originally broke on December 6, 2004, please see: https://BradBlog.com/ClintCurtis.
Attorney Cliff Arnebeck called Clint Curtis before the Committee, for the purpose of determining if the vote-counting process of the 2004 U.S. General Election in Ohio could have been manipulated by computer.
[Mr. Curtis is sworn in by the court reporter, on-camera, but without sound. Then sound commences.]
CLIFF ARNEBECK: Mr. Curtis, would you please state your full name for the record.
CLINT CURTIS: My name is Clinton Eugene Curtis.
ARNEBECK: And where do you reside?
CURTIS: Tallahassee, Florida.
ARNEBECK: And what is your profession?
CURTIS: I'm a computer programmer.
ARNEBECK: Would you please speak into the microphone so that the audience can hear your testimony.
CURTIS: I'm a computer programmer.
ARNEBECK: Mr Curtis, are there programs that can be used to secretly fix elections?
CURTIS: Yes.
ARNEBECK: How do you know that to be the case?
CURTIS: Because in October of 2000 I wrote a prototype for present Congressman Tom Feeney, at the company I work for in Oviedo, Florida, that did just that.
ARNEBECK: And when you say, "Did just that," it would rig an election?
CURTIS: It would flip the vote fifty-one forty-nine to whoever you wanted it to go to, and whichever race you wanted it to win.
ARNEBECK: And would that program that you designed be something that elections officials, that might be on county boards of elections, could detect?
CURTIS: They'd never see it.
[Audience: "Hmmm!"]
ARNEBECK: Mr....[Audience speaks "... question again"] Would you answer that question once again?
CURTIS: They would never see it.
ARNEBECK: So how would such a program, a secret program that fixes the election, how could it be detected?
CURTIS: You would have to view it either in the source code, or you'd have to have a receipt, and then count the hard paper against the actual vote total. Other than that, you won't see it.
ARNEBECK: Alright, Mr. Curtis, if you had been asked, you or others with your professional expertise, had been asked to design a protective program, a program that would protect the Ohio elections from against such software to fix the election, could you have done so?
CURTIS: If we'd been asked to make a program that could fix the election? Sure, anybody can do it.
ARNEBECK: No, could you have designed a program, a procedure, a protocol, that would have protected Ohio against this kind of rigging?
CURTIS: No, you have to look at the source code. You have to get, probably, programmers from both, or all, parties to look at the source code, and determine if there's anything in there that shouldn't be there. I mean, it's a simple program, you're adding one, two persons total. It's a hundreds lines of code, tops. There's.. [unintelligible]
ARNEBECK: Are you aware of whether there was any protective action in Ohio against this kind of vote rigging through software?
CURTIS: I don't know.
ARNEBECK: You don't know?
CURTIS: I don't know.
ARNEBECK: You were not asked to assist in the development of any protective system, is that correct?
CURTIS: No I was not.
ARNEBECK: In your op.. uh..have you reviewed at all the elections results in Ohio?
CURTIS: No I haven't.
ARNEBECK: OK. Given the availability of such vote-rigging software, and the testimony that has been given under oath of substantial statistical anomalies, and gross differences between exit polling data and the actual tabulated results, do you have an opinion whether or not the Ohio election, the Presidential election, was hacked?
CURTIS: Yes I would say it was. I mean, if you ... have exit polling data that is significantly off from the vote, then it's probably hacked.
ARNEBECK: And your testimony is under oath?
CURTIS: Yes, sir.
ARNEBECK: And the testimony you've given is true?
CURTIS: Yes, sir.
ARNEBECK: Thank you.
[Applause, considerable.]
REP. STEPHANIE TUBBS JONES Congresswoman Waters and I have the same question:
[Curtis is directed: "Back to the podium." Curtis returns to podium.]
REP. STEPHANIE TUBBS JONESWhat did you say you were asked to prepare?
CURTIS: I was asked by Tom Feeney, he's now Congressman, at that time he was Speaker of the House of Florida; Yang Enterprises' --- which is the company I worked for --- lobbyist; and their corporate attorney. He wore a lotta hats.
REP. STEPHANIE TUBBS JONESAnd at that time, he was the Speaker of the House of Florida, is that what you said?
CURTIS: Yes.
REP. STEPHANIE TUBBS JONESOk, thank you.
CONGRESSMAN JERROLD NADLER: You say he was the lobbyist for the voting machine company at the same time he was Speaker of the House?
CURTIS: I don't know what the voting machine company, but he was a lobbyist for Yang Enterprises. We had NASA contracts...
CONGRESSMAN JERROLD NADLER: Yang Enterprises did what, computers?
CURTIS: Computers.
REP. JERROLD NADLER: OK. And he was your lobbyist, your company's lobbyist?
CURTIS:
He was the lobbyist for Yang Enterprises.REP. JERROLD NADLER: And he asked you to design a code to rig an election?
CURTIS: Yes.
REP. JERROLD NADLER: While he was Speaker of the Florida House?
CURTIS: Yes.
REP. JERROLD NADLER: Was that during, or previous to, the 2000 election?
CURTIS: Yes, October, end of September.
REP. JERROLD NADLER: Did he ever express why he wanted the code to rig an election?
CURTIS: No. I immediately assumed that they were trying to keep you guys from cheating on them. [Audience laughs.] So I wrote up the documentation of what you would look for in the source code, how you would make sure that you didn't get, you know, taken advantage of, make sure that all voting machines had receipts, because that way you could back count the ones that looked funny.
REP. JERROLD NADLER: By "receipts," you mean a paper trail?
CURTIS: Yes, paper trail. And I handed that in to Mrs. Yang and said, "Here's your report, here's your program." And she said, "You don't understand. We need to hide the fraud in the source, in the source code."
REP. JERROLD NADLER: Hide the fraud, not reveal it?
CURTIS: Not reveal the fraud, "Because we need it to control the vote in South Florida." That's what she it said.
[Audience: "Woh!!"]
REP. JERROLD NADLER: To your knowledge, was this used?
CURTIS: I have no idea, I, I was ready to leave. [Audience/Curtis laugh.] I retired and left the company.
REP. JERROLD NADLER: Your testimony just a moment ago I think you said just before you left in answer to Congresswoman ... Jones' question, would you just repeat what you said in reference to the exit polls?
CURTIS: The exit polls should not be significantly different from the vote.
REP. JERROLD NADLER: And if they were, you would conclude what?
CURTIS: I would conclude someone's playing with the vote.
REP. JERROLD NADLER: Not with the exit polls?
CURTIS: That's possible too.
REP. JERROLD NADLER: OK.
CURTIS: Something is definitely skewed.
REP. JERROLD NADLER: Something is skewed in one or the other?
CURTIS: Right. To select which one, you'd have to see where the problem is.
REP. JERROLD NADLER: Let me ask you one further question. Assuming for the moment that such software, that's what you call it? such software to rig a vote, was used, in one or more machines in Ohio or in Florida, could you today detect that, if you looked at the source code?
CURTIS: If you could get the machines, and they had not been patched yet, I mean once they get in and touch 'em, anything could happen. You could also set timers to do that, but then you'd see the timers. Then you'd have to take those machines, decompile 'em, which I couldn't do, but possibly a Microsoft or MIT something, could do, you might, you might, be able to do.
REP. JERROLD NADLER: You might.
CURTIS: Depends on how good they are at destroying what they had.
REP. JERROLD NADLER: Destroying what they had by tampering with the machine afterwards, or by programming it with destroying instruction in the first place?
CURTIS:
Right.REP. JERROLD NADLER: Either or both?
CURTIS: Either or both. Because since you didn't actually see what's in there. So you don't actually know if the code is running in single executable, or running in various modules. If it's running in modules, you can make the code actually eat itself.
[Audience murmurs, then "Wow!"]
REP. JERROLD NADLER: Let me ask you just one further question. We've been told, I've been told, that people who assume that lots of the election results, a large fraction of the election results in this state may have been affected by computerware fraud in the computer are paranoid, because in order to do that you would have to have access to thousands of machines, and that would be readily detectable. Is that true?
CURTIS: It depends on the technology used. If you did a central tabulation machine that fed in, all you would have to do is set a flag. If you set a flag, the central tabulation machine would then flip your vote.
REP. JERROLD NADLER: So if you, so one person putting in bad code in a central tabulation machine could affect thousands and thousands, or tens of thousands, of votes?
CURTIS: Right. And you could activate it ...
[Congressman Nadler starts to speak, but stops]
CURTIS: ...you could activate it either automatically, or you could make it so that there's code existing on like an automic [?] machine that feeds it, where you would punch it in, it would set the flag, server would receive the flag, and then...
REP. JERROLD NADLER: And if you had a recount ... [unclear] ... no paper trail --- assuming that would happen --- would that be revealable by seeing a discrepancy between what the tabulator, the central tabulator trail [unclear] the individual machines which had not been tampered with, have?
CURTIS: Not if I wrote it.
REP. JERROLD NADLER: Why not?
CURTIS: I would make it match.
REP. JERROLD NADLER: You could work back from the tabulator to the individual machines? So the tabulator would tell the machines to switch their results?
CURTIS: Yes. It talks both ways. You can flip it to do whatever you need.
REP. JERROLD NADLER: And they actually do talk to each other, the machines...?
CURTIS: Yes, once it's hooked up, if it's networked together, they can talk to each other.
REP. JERROLD NADLER: So there's absolutely no assurance whatsoever that anything could be [right?] with these machines?
CURTIS: Absolutely none, unless you look at the source code, and make sure it's safe before it goes out.
REP. JERROLD NADLER: Thank you very much.
[Madam Chair:] Thank you, Congressman Nadler. I know that Congresswoman Waters has questions, and then Senator Miller, and then Congresswoman Stephanie Tubbs-Jones.
REP. MAXINE WATERS: This will only a moment, if you will come back to the uh, microphone.
[Audience laughs]
CURTIS: I'm new at this.
REP. MAXINE WATERS: As you know, there has been a lot of discussion about, I think it was Diebold Company, their relationship to the President, and the administration, and supposedly comments about helping to insure that the President was re-elected. In your world, in your environment, have you heard any of this kind of discussion? Do you know people at Diebold? Do you have any sense of any actions that may have been taken?
CURTIS: Uh, I don't know anything about that at all.
REP. MAXINE WATERS: Thank you.
[Madam Chair calls Dr. Miller]
DR. MILLER: I suspect that people will attack you in terms of your credibility. Could you restate once again your, your credentials.
CURTIS: Uh, I'm a programmer, I worked for NASA, I worked for Exxon Mobil, I worked for um, Florida Department of Transportation, and other elements of my story, because this company, well, let's get into it. Why not? This company also had a NASA contract, and they were basically downloading tons of information, I mean, gigabytes' worth, and handing them off to this little Chinese guy named Henry Nee (?) And, it didn't seem right, and, he was hacking things
I wrote a program for DOT that allowed contractors to send information into DOT, and he was kind of the quality assurance guy for software. He put a wiretapping module into the program that went out to the contractors so that it actually sent everything they sent, back to Yang. So I reported all this, and just last March I think, he was arrested for attempting to send anti-tank missile chips to the capital of Communist China.
If that's correct, this is like a small thing...
Of course I think he only got a hundred dollar fine.
[Audience: Hmmmm! Hmmm!]
And no time.
[Audience: Oh God!]
[Madam Chair:] Thank you. Congresswoman Stephanie Tubbs-Jones....
[Audience: long, hearty applause]
We are now going to um go back to the public testimony and...
[End]


 Dems Step Up: Crawford Landslide in WI; Booker Makes History in U.S. Senate: 'BradCast' 4/2/25
Dems Step Up: Crawford Landslide in WI; Booker Makes History in U.S. Senate: 'BradCast' 4/2/25 Judge Dismisses Long-Running Challenge to GA's Unverifiable, Insecure E-Vote System: 'BradCast' 4/1/25
Judge Dismisses Long-Running Challenge to GA's Unverifiable, Insecure E-Vote System: 'BradCast' 4/1/25 'Green News Report' 4/1/25
'Green News Report' 4/1/25
 Bad Court and Election News for Trump is Good News for America: 'BradCast' 3/31/25
Bad Court and Election News for Trump is Good News for America: 'BradCast' 3/31/25 Sunday 'Great Start!' Toons
Sunday 'Great Start!' Toons Vets Push Back at Trump, Musk Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25
Vets Push Back at Trump, Musk Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25 'Green News Report' 3/27/25
'Green News Report' 3/27/25 Signal Scandal Worsens for Trump, GOP; Big Dem Election Wins in PA: 'BradCast' 3/26
Signal Scandal Worsens for Trump, GOP; Big Dem Election Wins in PA: 'BradCast' 3/26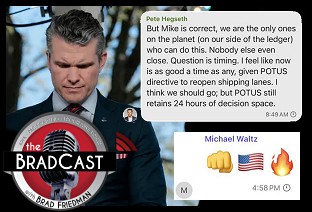 'Emptywheel' on Why Trump NatSec Team Should 'Resign in Disgrace' After Signal Chat Debacle: 'BradCast' 3/25/25
'Emptywheel' on Why Trump NatSec Team Should 'Resign in Disgrace' After Signal Chat Debacle: 'BradCast' 3/25/25 'Green News Report' 3/25/25
'Green News Report' 3/25/25 USPS 'Belongs to the People, Not the Billionaires': 'BradCast' 3/24/25
USPS 'Belongs to the People, Not the Billionaires': 'BradCast' 3/24/25 Sunday 'Suddenly Conceivable' Toons
Sunday 'Suddenly Conceivable' Toons 'Green News Report' 3/20/25
'Green News Report' 3/20/25 We're ALL Voice of America Now: 'BradCast' 3/20/25
We're ALL Voice of America Now: 'BradCast' 3/20/25 What Trump's 'Timber Production Expansion' Means (and Costs): 'BradCast' 3/19/25
What Trump's 'Timber Production Expansion' Means (and Costs): 'BradCast' 3/19/25 Courts Largely Holding Against Trump, Musk Lawlessness: 'BradCast' 3/18/25
Courts Largely Holding Against Trump, Musk Lawlessness: 'BradCast' 3/18/25 Chief VOA Reporter on Outlet Falling Silent First Time Since 1942: 'BradCast' 3/17/25
Chief VOA Reporter on Outlet Falling Silent First Time Since 1942: 'BradCast' 3/17/25 Trump EPA Unveils Plans to Endanger, Sicken Americans: 'BradCast' 3/13/25
Trump EPA Unveils Plans to Endanger, Sicken Americans: 'BradCast' 3/13/25 Trump Nixed Enforce-ment Against 100 Corp. Lawbreakers: 'BradCast' 3/12/25
Trump Nixed Enforce-ment Against 100 Corp. Lawbreakers: 'BradCast' 3/12/25 Bad Day for 'Strongmen': 'BradCast' 3/11
Bad Day for 'Strongmen': 'BradCast' 3/11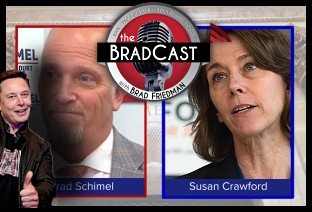 WI Election Could Flip Supreme Court Control, Musk Jumps In: 'BradCast' 3/10
WI Election Could Flip Supreme Court Control, Musk Jumps In: 'BradCast' 3/10
![Click to show/hide [+]](https://bradblog.com/images/toggle_plus.gif)
 VA GOP VOTER REG FRAUDSTER OFF HOOK
VA GOP VOTER REG FRAUDSTER OFF HOOK Criminal GOP Voter Registration Fraud Probe Expanding in VA
Criminal GOP Voter Registration Fraud Probe Expanding in VA DOJ PROBE SOUGHT AFTER VA ARREST
DOJ PROBE SOUGHT AFTER VA ARREST Arrest in VA: GOP Voter Reg Scandal Widens
Arrest in VA: GOP Voter Reg Scandal Widens ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC
ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States'
LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States' 'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States
'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States FINALLY: FOX ON GOP REG FRAUD SCANDAL
FINALLY: FOX ON GOP REG FRAUD SCANDAL COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION
COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL
CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV
Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV  CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM
CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM
CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL
RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV
VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD
RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud
EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud GOP REGISTRATION FRAUD FOUND IN FL
GOP REGISTRATION FRAUD FOUND IN FL


































