 Virginia has decided to learn what much of the country already knows. The 100% unverifiable touch-screen voting systems they have long been using in their public elections are also 100% hackable.
Virginia has decided to learn what much of the country already knows. The 100% unverifiable touch-screen voting systems they have long been using in their public elections are also 100% hackable.
After ignoring the warnings and using them anyway for more than a decade --- and three Presidential elections --- a recent incident on Election Day in 2014 led the Commonwealth to finally do what they should have and could have done long ago: test the machines to find out how vulnerable they actually are.
Well, they finally did so and --- boy howdy! --- did they discover what the rest of us have been warning about for years.
There is a reason, after all, that Virginia was the last state in the union to continue using the WINVote system made by the ironically named Advanced Voting Solutions (AVS). And there is a reason why, after finally bothering to test them, Virginia has now immediately decertified one-fifth of the voting systems used across the state, even though it will leave some jurisdictions scrambling for new ways to hold their primary elections scheduled for early June.
We've been noting problems with the WINVote system almost as long as The BRAD BLOG has been in existence. One example is our short report from 2007, when we discussed problems with the AVS systems before the company eventually went out of business entirely and after the WINVote system had been decertified by Pennsylvania when the company refused to pay the federal testing lab examining a newer version of the system for federal certification. Before those tests were discontinued at the time, we reported, the lab had "found 1,946 source code anomalies, 25 serious documentation problems, and an unauthorized change of motherboards."
As we wrote in 2007, "Elections officials want to ignore those problems." The elections officials in Virginia were precisely among those we were talking about.
But, no more. Once VA officials finally decided to do their own long-overdue security analysis of the systems, "Security deficiencies were identified in multiple areas, including physical controls, network access, operating system controls, data protection, and the voting tally process," according to the 6-page report [PDF] released by the Virginia Information Technologies Agency (VITA) this week.
"The combination of critical vulnerabilities in these areas, along with the ability to remotely modify votes discretely, is considered to present a significant risk. This heightened level of risk has led VITA security staff to conclude that [a] malicious third party could be able to alter votes on these devices," they wrote, adding tersely: "These machines should not remain in service."
The details of the Commonwealth's findings (now that they've looked for them) are so mind-blowingly startling that some Virginia localities who are losing their voting systems are now perfectly happy with the idea that they may have to --- gasp! --- hand count paper ballots in their upcoming elections...
Spotsylvania, We've Got a Problem
NPR's Pam Fessler nicely explains what led the state to finally examine their long-used WINVote systems...
"One machine would go and crash. They'd bring it back up. Another one would crash," said Edgardo Cortes, the state's elections commissioner. "Starting in the early afternoon, they brought in a piece of replacement equipment that experienced the same issues when they set it up in the precinct."
Cortes added that elections workers had a theory about what had caused the problem.
"There was some interference," he said, "potentially from a wireless signal from an election officer [who] was streaming music on their phone."
When state auditors investigated, though, they didn't find that particular problem. Instead, they found something more disturbing. While using their smartphones, they were able to connect to the voting machines' wireless network, which is used to tally votes.
VITA, which, according to their report "was not provided with any information concerning the existing security controls enabled on these devices, therefore making the review a 'black-box' test," reviewed the systems from five aspects: "physical, network, operating system, data, and the vote tally process." Without access to the system source code or anything but off the shelf software tools, they were able to gain access and manipulate every area of the system, including the ability to change every single vote cast on it in a way that would be virtually undetectable by election officials.
Physical: VITA found that "a malicious third party could plug in a device [via one of the system's three USB ports] that provides access to the machine either locally or remotely," in such a way that they could entirely alter or even replace the operating system. The investigators warn that, via this type of access, "it is probable that an attacker could install a device that would allow remote or local access to monitor, modify, or provide unauthorized access to data."
Network: "The wireless cards on the devices provide an attack vector where an external party can access the WINVote devices and modify the data without notice from a nearby location," VITA found. They said that the default configuration broadcasts the system's wireless network name "where it can be easily detected by most devices that have wireless cards," such as smartphones. Perhaps more disturbing: Even with the wireless networking capabilities disabled via the WINVote software's interface, the system still allowed access to its network. The only way the analysts could prevent such access was with the physical removal of the wireless network adapter, though that "rendered the WINVote device unable to execute and administer an election."
Moreover, the systems used an older encryption technology (WEP) which was long ago cracked and discontinued.
But, buckle up, cracking the encryption key wasn't even necessary, since the analysts were able to simply guess the WINVote software's network password very quickly. It was hardcoded into the software and could not be changed. For the record, that password is: "abcde".
In all, the analysts found "eight critical, three high, five medium and two low-risk vulnerabilities" in the networking system, "providing several potential avenues of attack."
Operating System: The WINVote system runs on Windows XP 2002, an operating system which will no longer be supported by Microsoft as of next year. Though many patches have been issued for that operating system over the years, none were found to have been installed on the WINVote machines examined by the testers. "Because of this, the devices are vulnerable to many published exploits."
"The use of a weak password by the devices enabled VITA to crack the password" for the Windows Administrator account --- which was "admin" --- "almost immediately ... Using this account and password, full administrative access to the WINVote operating system was available."
Data: As explained by VITA, "The voting databases on the devices would be a primary target for an attacker. The databases contain information, such as the ballot, the voting location, and (most importantly) the number of votes." The database used is Microsoft Access and the data inside of it is not encrypted. VITA staff was able to access the password to the database "in approximately 10 seconds" and found it to be "shoup", the name of the WINVote manufacturer before it was purchased by the now-defunct AVS.
"This password was used for all of the database files. With the password, it was possible to copy the database files to the security analysis system, open them and modify the voting data," the report explains. After having changed the voting data in the files, the altered data was never noticed by the system.
Vote Talley Process: They saved the best for last. "The primary goal of the WINVote testing was to identify whether votes could be modified remotely without detection by voting staff. To determine whether this was possible, VITA executed a controlled election with the vote tallies for each candidate noted. Before closing out the election, VITA downloaded and modified the database containing the vote tallies for each candidate on a remote security analysis station connected to the ad-hoc network. This modified database was loaded back onto the WINVote device and the election was closed. The compromised vote tallies were reflected in the closed election results, proving that the vote data could be remotely modified. This process test was performed with the wireless network both enabled and disabled through the WINVote software."
In conclusion, the analysts write: "Because the WINVote devices use insecure security protocols, weak passwords, and unpatched software, the WINVote devices operate with a high level of risk. The security testing by VITA proved that the vulnerabilities on the WINVote devices can allow a malicious party to compromise the confidentiality and integrity of voting data."
Other than that --- and the fact that they could have learned all of this a decade ago, had they bothered --- these 100% unverifiable (even if they were secure) touch-screen voting systems work great!
"It's hard to find plain words that convey just how bad the security of this machine is," writes Dan Goodin at Ars Technica. "It's even harder to fathom so many critical defects resided in a line of machines that has played a crucial role in the US' democratic system for so many years."
"If an election was held using the AVS WinVote, and it wasn’t hacked, it was only because no one tried," says e-voting security analyst Jeremy Epstein. "The vulnerabilities were so severe, and so trivial to exploit, that anyone with even a modicum of training could have succeeded. They didn’t need to be in the polling place --- within a few hundred feet (e.g., in the parking lot) is easy, and within a half mile with a rudimentary antenna built using a Pringles can. Further, there are no logs or other records that would indicate if such a thing ever happened, so if an election was hacked any time in the past, we will never know."
Epstein adds: "I’ve been in the security field for 30 years, and it takes a lot to surprise me. But the VITA report really shocked me --- as bad as I thought the problems were likely to be, VITA’s...report showed that they were far worse."
With the system finally decertified, Powhatan County is one of the jurisdictions now scrambling to find a new system to use for their June 9th primary. And while many VA election officials had long fought against the removal of the WINVote system --- for years --- Powhatan's Election Director Karen Alexander is now resigned to finally giving them up, according to NPR, because "The security risk is too high."
She says that her county may borrow equipment from a neighboring county for the upcoming elections or they may do what they could have and should have done years ago, at least if they wanted to actually serve and respect their voters: count hand-marked paper ballots by hand.
If only someone had warned them years ago...
(Snail mail support to "Brad Friedman, 7095 Hollywood Blvd., #594 Los Angeles, CA 90028" always welcome too!)
|


 Bad Court and Election News for Trump is Good News for America: 'BradCast' 3/31/25
Bad Court and Election News for Trump is Good News for America: 'BradCast' 3/31/25 Sunday 'Great Start!' Toons
Sunday 'Great Start!' Toons Vets Push Back at Trump, Musk Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25
Vets Push Back at Trump, Musk Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25 'Green News Report' 3/27/25
'Green News Report' 3/27/25
 Signal Scandal Worsens for Trump, GOP; Big Dem Election Wins in PA: 'BradCast' 3/26
Signal Scandal Worsens for Trump, GOP; Big Dem Election Wins in PA: 'BradCast' 3/26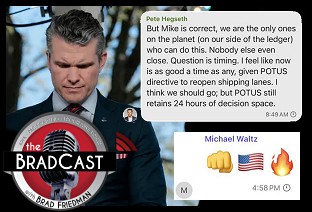 'Emptywheel' on Why Trump NatSec Team Should 'Resign in Disgrace' After Signal Chat Debacle: 'BradCast' 3/25/25
'Emptywheel' on Why Trump NatSec Team Should 'Resign in Disgrace' After Signal Chat Debacle: 'BradCast' 3/25/25 'Green News Report' 3/25/25
'Green News Report' 3/25/25 USPS 'Belongs to the People, Not the Billionaires': 'BradCast' 3/24/25
USPS 'Belongs to the People, Not the Billionaires': 'BradCast' 3/24/25 Sunday 'Suddenly Conceivable' Toons
Sunday 'Suddenly Conceivable' Toons 'Green News Report' 3/20/25
'Green News Report' 3/20/25 We're ALL Voice of America Now: 'BradCast' 3/20/25
We're ALL Voice of America Now: 'BradCast' 3/20/25 What Trump's 'Timber Production Expansion' Means (and Costs): 'BradCast' 3/19/25
What Trump's 'Timber Production Expansion' Means (and Costs): 'BradCast' 3/19/25 Courts Largely Holding Against Trump, Musk Lawlessness: 'BradCast' 3/18/25
Courts Largely Holding Against Trump, Musk Lawlessness: 'BradCast' 3/18/25 Chief VOA Reporter on Outlet Falling Silent First Time Since 1942: 'BradCast' 3/17/25
Chief VOA Reporter on Outlet Falling Silent First Time Since 1942: 'BradCast' 3/17/25 Trump EPA Unveils Plans to Endanger, Sicken Americans: 'BradCast' 3/13/25
Trump EPA Unveils Plans to Endanger, Sicken Americans: 'BradCast' 3/13/25 Trump Nixed Enforce-ment Against 100 Corp. Lawbreakers: 'BradCast' 3/12/25
Trump Nixed Enforce-ment Against 100 Corp. Lawbreakers: 'BradCast' 3/12/25 Bad Day for 'Strongmen': 'BradCast' 3/11
Bad Day for 'Strongmen': 'BradCast' 3/11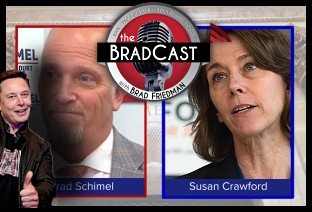 WI Election Could Flip Supreme Court Control, Musk Jumps In: 'BradCast' 3/10
WI Election Could Flip Supreme Court Control, Musk Jumps In: 'BradCast' 3/10
 VA GOP VOTER REG FRAUDSTER OFF HOOK
VA GOP VOTER REG FRAUDSTER OFF HOOK Criminal GOP Voter Registration Fraud Probe Expanding in VA
Criminal GOP Voter Registration Fraud Probe Expanding in VA DOJ PROBE SOUGHT AFTER VA ARREST
DOJ PROBE SOUGHT AFTER VA ARREST Arrest in VA: GOP Voter Reg Scandal Widens
Arrest in VA: GOP Voter Reg Scandal Widens ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC
ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States'
LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States' 'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States
'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States FINALLY: FOX ON GOP REG FRAUD SCANDAL
FINALLY: FOX ON GOP REG FRAUD SCANDAL COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION
COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL
CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV
Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV  CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM
CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM
CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL
RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV
VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD
RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud
EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud GOP REGISTRATION FRAUD FOUND IN FL
GOP REGISTRATION FRAUD FOUND IN FL


































