 Virginia has decided to learn what much of the country already knows. The 100% unverifiable touch-screen voting systems they have long been using in their public elections are also 100% hackable.
Virginia has decided to learn what much of the country already knows. The 100% unverifiable touch-screen voting systems they have long been using in their public elections are also 100% hackable.
After ignoring the warnings and using them anyway for more than a decade --- and three Presidential elections --- a recent incident on Election Day in 2014 led the Commonwealth to finally do what they should have and could have done long ago: test the machines to find out how vulnerable they actually are.
Well, they finally did so and --- boy howdy! --- did they discover what the rest of us have been warning about for years.
There is a reason, after all, that Virginia was the last state in the union to continue using the WINVote system made by the ironically named Advanced Voting Solutions (AVS). And there is a reason why, after finally bothering to test them, Virginia has now immediately decertified one-fifth of the voting systems used across the state, even though it will leave some jurisdictions scrambling for new ways to hold their primary elections scheduled for early June.
We've been noting problems with the WINVote system almost as long as The BRAD BLOG has been in existence. One example is our short report from 2007, when we discussed problems with the AVS systems before the company eventually went out of business entirely and after the WINVote system had been decertified by Pennsylvania when the company refused to pay the federal testing lab examining a newer version of the system for federal certification. Before those tests were discontinued at the time, we reported, the lab had "found 1,946 source code anomalies, 25 serious documentation problems, and an unauthorized change of motherboards."
As we wrote in 2007, "Elections officials want to ignore those problems." The elections officials in Virginia were precisely among those we were talking about.
But, no more. Once VA officials finally decided to do their own long-overdue security analysis of the systems, "Security deficiencies were identified in multiple areas, including physical controls, network access, operating system controls, data protection, and the voting tally process," according to the 6-page report [PDF] released by the Virginia Information Technologies Agency (VITA) this week.
"The combination of critical vulnerabilities in these areas, along with the ability to remotely modify votes discretely, is considered to present a significant risk. This heightened level of risk has led VITA security staff to conclude that [a] malicious third party could be able to alter votes on these devices," they wrote, adding tersely: "These machines should not remain in service."
The details of the Commonwealth's findings (now that they've looked for them) are so mind-blowingly startling that some Virginia localities who are losing their voting systems are now perfectly happy with the idea that they may have to --- gasp! --- hand count paper ballots in their upcoming elections...


 Blowing Smoke.
Blowing Smoke. 'Green News Report' 5/6/25
'Green News Report' 5/6/25
 SCOTUS Allowing Publicly-Funded Religious Schools 'Would be a Ground-Breaking Disaster': 'BradCast' 5/7/25
SCOTUS Allowing Publicly-Funded Religious Schools 'Would be a Ground-Breaking Disaster': 'BradCast' 5/7/25 Trump Judge Blocks NC GOP Attempt to Steal 2024 State Supreme Court Election: 'BradCast' 5/6/25
Trump Judge Blocks NC GOP Attempt to Steal 2024 State Supreme Court Election: 'BradCast' 5/6/25 Prosecutors Resign After Trump U.S. Attny Strikes Deal With Felon Cop: 'BradCast' 5/5/25
Prosecutors Resign After Trump U.S. Attny Strikes Deal With Felon Cop: 'BradCast' 5/5/25 Sunday 'Good Buy, Dolly!' Toons
Sunday 'Good Buy, Dolly!' Toons Trump Losing Streak Continues into SECOND Hundred Days: 'BradCast' 5/1/25
Trump Losing Streak Continues into SECOND Hundred Days: 'BradCast' 5/1/25 'Green News Report' 5/1/25
'Green News Report' 5/1/25 100 Daze: 'BradCast' 4/30/25
100 Daze: 'BradCast' 4/30/25 Campaign to 'Impeach Trump Again' Gains Fresh Momentum: 'BradCast' 4/29/25
Campaign to 'Impeach Trump Again' Gains Fresh Momentum: 'BradCast' 4/29/25 'Green News Report' 4/29/25
'Green News Report' 4/29/25 And Then They Came for the Judges...: 'BradCast' 4/28/25
And Then They Came for the Judges...: 'BradCast' 4/28/25 Sunday 'Desperation' Toons
Sunday 'Desperation' Toons Trump EPA Guts Enviro Justice Office: 'BradCast' 4/24/25
Trump EPA Guts Enviro Justice Office: 'BradCast' 4/24/25 'Green News Report' 4/24/25
'Green News Report' 4/24/25 Sunday
Sunday  Largest U.S. Broad-caster Hoaxes Viewers to Help Gut FCC Rules: 'BradCast' 4/23/25
Largest U.S. Broad-caster Hoaxes Viewers to Help Gut FCC Rules: 'BradCast' 4/23/25 FCC on Precipice of Ending All Limits on Corp. Control of Local TV Stations
FCC on Precipice of Ending All Limits on Corp. Control of Local TV Stations GOP Earth Day 2025 Hypocrisies and Dilemmas: 'BradCast' 4/22/25
GOP Earth Day 2025 Hypocrisies and Dilemmas: 'BradCast' 4/22/25 Pope Francis Dies, Trump Still Alive and Criming: 'BradCast' 4/21/25
Pope Francis Dies, Trump Still Alive and Criming: 'BradCast' 4/21/25 Soc. Sec. Expert Warns DOGE of Collapse, Privatization: 'BradCast' 4/10/2025
Soc. Sec. Expert Warns DOGE of Collapse, Privatization: 'BradCast' 4/10/2025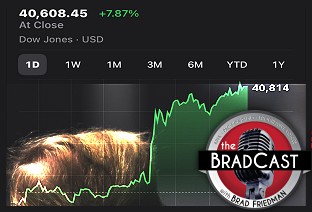 Trump Blinks, Chaos Reigns, Markets Spike Amid Tariff 'Pause': 'BradCast' 4/9/25
Trump Blinks, Chaos Reigns, Markets Spike Amid Tariff 'Pause': 'BradCast' 4/9/25 SCOTUS Deportation Ruling Grimmer Than First Appears: 'BradCast' 4/8/25
SCOTUS Deportation Ruling Grimmer Than First Appears: 'BradCast' 4/8/25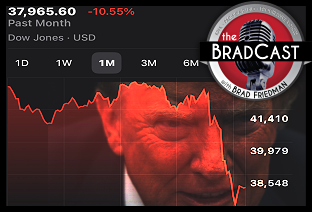 Cliff Diving with Donald: 'BradCast' 4/7/25
Cliff Diving with Donald: 'BradCast' 4/7/25
 VA GOP VOTER REG FRAUDSTER OFF HOOK
VA GOP VOTER REG FRAUDSTER OFF HOOK Criminal GOP Voter Registration Fraud Probe Expanding in VA
Criminal GOP Voter Registration Fraud Probe Expanding in VA DOJ PROBE SOUGHT AFTER VA ARREST
DOJ PROBE SOUGHT AFTER VA ARREST Arrest in VA: GOP Voter Reg Scandal Widens
Arrest in VA: GOP Voter Reg Scandal Widens ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC
ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States'
LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States' 'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States
'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States FINALLY: FOX ON GOP REG FRAUD SCANDAL
FINALLY: FOX ON GOP REG FRAUD SCANDAL COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION
COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL
CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV
Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV  CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM
CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM
CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL
RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV
VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD
RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud
EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud GOP REGISTRATION FRAUD FOUND IN FL
GOP REGISTRATION FRAUD FOUND IN FL



























 Both election integrity advocates and
Both election integrity advocates and  It's been happening for years now. On the day after elections like last Tuesday's, media figures begin navel gazing to figure out how pre-election polls, created by dozens of independent pollsters using dozens of different methodologies, could all find the same thing but turn out to be so wrong once the election results are in.
It's been happening for years now. On the day after elections like last Tuesday's, media figures begin navel gazing to figure out how pre-election polls, created by dozens of independent pollsters using dozens of different methodologies, could all find the same thing but turn out to be so wrong once the election results are in.
 A new
A new 
 Just hours after a similar
Just hours after a similar  Just over a week ago,
Just over a week ago,  Very big news out of a federal court in Wisconsin today, where the state's polling place Photo ID law (Act 23) has now been
Very big news out of a federal court in Wisconsin today, where the state's polling place Photo ID law (Act 23) has now been  A Circuit Court judge has resoundingly rejected Arkansas' new Photo ID restrictions on voting, declaring the law to be "null and void" and in violation of the state's Constitutional right to vote.
A Circuit Court judge has resoundingly rejected Arkansas' new Photo ID restrictions on voting, declaring the law to be "null and void" and in violation of the state's Constitutional right to vote. This week's
This week's 
 Some encouraging news to begin your week, along with apologies to Ian Millhiser for running
Some encouraging news to begin your week, along with apologies to Ian Millhiser for running  Big news on the Big 'Clean Coal' front today, just breaking
Big news on the Big 'Clean Coal' front today, just breaking 












