 In a letter obtained by The BRAD BLOG, Riverside County, California, Supervisor Jeff Stone attempts to move the goal posts concerning the ill-considered challenge he issued to Election Integrity advocates in December during a public, video-taped meeting.
In a letter obtained by The BRAD BLOG, Riverside County, California, Supervisor Jeff Stone attempts to move the goal posts concerning the ill-considered challenge he issued to Election Integrity advocates in December during a public, video-taped meeting.
The letter, sent by Stone on Wednesday to outgoing California Secretary of State Bruce McPherson, attempts to unilaterally create unrealistic (some might say desperate) conditions for a proposed hack test of the county's electronic touch-screen voting machines, made by Sequoia Voting Systems. When Stone initially issued the challenge, he included no such ground rules.
Computer scientists and security experts interviewed by The BRAD BLOG, as well as a number of reports and studies from nationally-recognized bodies, understand what Stone apparently doesn't: the major threat to voting machine malfeasance comes not from a voter walking up to a voting system on Election Day, but rather from insiders who are easily able to gain unsupervised access to the machines.
The letter to McPherson from Stone is posted in full at the end of this article.
As we reported in mid-December, Stone had challenged Election Integrity advocates from Democracy for America-Temecula Valley, during a public meeting of the County Supervisors, to bring in a programmer willing to attempt a hack of Riverside's voting system. His offer was simply "to set up an appointment with one of our machines and I’d like him or her [the programmer] to verify that they can manipulate that machine."
At the time, Stone also said that he was willing to "bet a thousand to one that they cannot do it." (A transcript of the entire, very brief exchange was posted in full in our initial report of the incident, along with links to two different video tapes of the encounter.)
The challenge was accepted the following week by the activists, who announced that noted Finnish computer security expert Harri Hursti had volulnteered to perform the tests. Hursti previously hacked a paper-based Diebold optical-scan voting system in Leon County, Florida, at the end of 2005, and helped to discover alarming vulnerabilities in Diebold touch-screen systems a few months later in Emery County, Utah.
At the same time, a number of other election integrity advocates announced they would stake $1000 for charity on the bet against Stone's $1 million.
 Stone's challenge, as seen in the videos and transcript, specified no ground rules for the hack test, despite what Stone indicates in his letter to McPherson. The Secretary of State recently lost his election bid to the incoming Debra Bowen, who will take office this coming Monday. McPherson had been much criticized for his lax testing of voting systems and his close relationship with a number of voting machine companies such as Diebold. He had also been quite friendly with the all-Republican Board of Supervisors in Riverside, The BRAD BLOG has learned from sources on the ground. Bowen has been an outspoken critic of McPherson's rubber-stamp certification of electronic voting systems in the state as well as the lack of adequate security standards specified for their use.
Stone's challenge, as seen in the videos and transcript, specified no ground rules for the hack test, despite what Stone indicates in his letter to McPherson. The Secretary of State recently lost his election bid to the incoming Debra Bowen, who will take office this coming Monday. McPherson had been much criticized for his lax testing of voting systems and his close relationship with a number of voting machine companies such as Diebold. He had also been quite friendly with the all-Republican Board of Supervisors in Riverside, The BRAD BLOG has learned from sources on the ground. Bowen has been an outspoken critic of McPherson's rubber-stamp certification of electronic voting systems in the state as well as the lack of adequate security standards specified for their use.
In his letter --- notably sent to McPherson and not to Bowen --- Stone creates a number of ground rules which were neither specified at the time of the challenge, nor the norm for standard security and vulnerability testing of computer software and hardware. He incorrectly characterizes the December exchange with Election Integrity advocate Maxine Ewig this way, unilaterally creating absurd conditions for the testing in the process...
Stone's reference to being "prohibited from...reaching around the back of the machine" is a direct reference to one of the already-known security vulnerabilities of Sequoia's touch-screen voting systems; specifically the "Yellow Button" on the back of the machines which, if pressed in a simple sequence, allows voters to cast as many votes as they like. The BRAD BLOG broke that story in the week prior to the November election.
Despite Stone's newly invented restrictions, actual experts familiar with security testing of such systems say that vulnerability testing is conducted quite differently in the real world.
Dr. Herbert F. Thompson, Chief Security Strategist for Security Innovation, who also worked with Hursti on the Leon County, Florida hack of the Diebold optical-scan system, explained to The BRAD BLOG recently that security testers first try and gain access to systems "in the same way that someone hoping to insert malicious code might attempt to access the machines. The most direct avenue," he explained, "would be to try and exploit insider access such as an election official or poll worker might have."
Thompson is the author of 12 books on computer security including How to Break Software Security: Effective Techniques for Security Testing and The Software Vulnerability Guide.
Another computer scientist and security expert familiar with both electronic voting systems and their certification procedures at both the state and federal level wrote to us after reading the letter to say that he finds Stone's expectations to be unrealistic and uninformed, but not necessarily unusual.
"This, of course, represents the most common of misunderstandings --- that voting system security means invulnerability to attacks by voters. Voters are not the problem," the scientist wrote, requesting anonymity due to close relationships with authorities in his state.
"The much more serious and difficult security problems involve protecting the system from errors or potential malicious acts by insiders, including [voting machine] vendor employees, employees of county election agencies, contractors, and poll workers," he explained.
In Riverside County, where pre-programmed, election-ready touch-screen systems are sent home with pollworkers on overnight "sleepovers" days before the election, as well as unsecurely stored in various polling locations the night before the election, a would-be hacker might have plenty of time to attempt to exploit the systems.
Additionally, election officials and employees of the voting machine companies could gain lengthy and unrestricted access to the supposedly "secure" voting systems before they are used on Election Day.
These are the type of real-world conditions, both scientists explained, that professional testers would seek in their attempts to mimic potential exploits from the "black hats."
Indeed, insider access to the voting systems has been one of the top concerns expressed in a number of reports, including a landmark 2006 study by NYU's Brennan Center for Justice and a National Commission on Federal Election Reform, co-chaired by James A. Baker III and former President Jimmy Carter in 2005.
The final report of the Baker/Carter commission found that, "Software can be modified maliciously before being installed into individual voting machines. There is no reason to trust insiders in the election industry any more than in other industries."
The computer scientist who wrote to The BRAD BLOG after reviewing Stone's letter also alluded to the common insider threats seen in industries other than E-voting. "In financial institutions, intelligence agencies, and most other security situations, the most challenging security threats are almost always from insider malfeasance."
The expressed written intent of Stone's letter seems to be to inquire as to whether McPherson concurs that such a test would be "in compliance with all State and Federal laws and regulations."
While we don't have an answer from McPherson, an official from Bowen's office replied to our query on that point that they are unaware, at this time, of any such state or federal regulations that would bar such an independent analysis of a voting machine by an expert with the approval of county officials.
Finally, Stone writes the following early on in his letter:
Setting aside the last sentence for the moment, which is silly beyond description... on the first sentence, clainming that previous "hacking experiments" having allowed testers "unlimited resources and time with the voting unit and software," Stone is just plain wrong.
In the aforementioned 2005 hack of the Diebold system in Leon County, Florida, by Hursti and Thompson, the two computer security professionals were given no such "unlimited" access or "time with the voting unit." In fact, the machine used in the live hack test --- as seen in the HBO documentary Hacking Democracy --- was chosen by random lot just moments before the test was actually done. Hursti, who wrote the code that flipped the mock election during the test, was never even allowed inside the same room while the exploited optical-scan system was in use.
Riverside election integrity advocate Tom Courbat told us that Stone's statement was "like NASA saying 'we don't want to test those O-Rings, it'll only undermine the astronauts' confidence in their space craft'."
"The system is either secure or it is not," Courbat said. "What is this nonsense about vulnerability testing harming voter confidence?"
 As Stone desperately works to find a way to extricate himself from his own ill-conceived mess, he would do well to simply consider instead that he, and his fellow supervisors and county election officials, have been wrong all along. And the truth is that they too have no faith in the security of their own voting systems. That, despite so many years of denial to the contrary.
As Stone desperately works to find a way to extricate himself from his own ill-conceived mess, he would do well to simply consider instead that he, and his fellow supervisors and county election officials, have been wrong all along. And the truth is that they too have no faith in the security of their own voting systems. That, despite so many years of denial to the contrary.
In truth, it's folks like Stone and other voting machine apologists like his fellow County Supervisors and Riverside's Registrar of Voters, Barbara Dunmore, whose disingenuous actions, statements, and complete lack of transparency --- to quote Stone --- "generate distrust in the democratic process and discourage voters from participating in elections."
Stone's hilarious letter to McPherson follows in full below...




 Vets Push Back at Trump, Musk Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25
Vets Push Back at Trump, Musk Plan to Slash Health Care, 80K V.A. Jobs: 'BradCast' 3/27/25 'Green News Report' 3/27/25
'Green News Report' 3/27/25
 Signal Scandal Worsens for Trump, GOP; Big Election Victories for Dems in PA: 'BradCast' 3/26/25
Signal Scandal Worsens for Trump, GOP; Big Election Victories for Dems in PA: 'BradCast' 3/26/25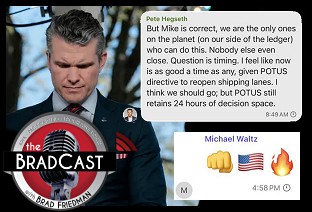 'Emptywheel' on Why Trump NatSec Team Should 'Resign in Disgrace' After Signal Chat Debacle: 'BradCast' 3/25/25
'Emptywheel' on Why Trump NatSec Team Should 'Resign in Disgrace' After Signal Chat Debacle: 'BradCast' 3/25/25 'Green News Report' 3/25/25
'Green News Report' 3/25/25 Postal Workers Union Prez: USPS 'Belongs to the People, Not the Billionaires':
Postal Workers Union Prez: USPS 'Belongs to the People, Not the Billionaires': Sunday 'Suddenly Conceivable' Toons
Sunday 'Suddenly Conceivable' Toons We're ALL Voice of America Now: 'BradCast' 3/20/25
We're ALL Voice of America Now: 'BradCast' 3/20/25 'Green News Report' 3/20/25
'Green News Report' 3/20/25 What Trump's 'Timber Production Expansion' Means (and Costs): 'BradCast' 3/19/25
What Trump's 'Timber Production Expansion' Means (and Costs): 'BradCast' 3/19/25 Courts Largely Holding Against Trump, Musk Lawlessness: 'BradCast' 3/18/25
Courts Largely Holding Against Trump, Musk Lawlessness: 'BradCast' 3/18/25 'Green News Report' 3/18/25
'Green News Report' 3/18/25 Chief VOA Reporter on Outlet Falling Silent First Time Since 1942: 'BradCast' 3/17/25
Chief VOA Reporter on Outlet Falling Silent First Time Since 1942: 'BradCast' 3/17/25 Sunday 'The Usual' Toons
Sunday 'The Usual' Toons 'Green News Report' 3/13/25
'Green News Report' 3/13/25 Trump EPA Unveils Plans to Endanger, Sicken Americans: 'BradCast' 3/13/25
Trump EPA Unveils Plans to Endanger, Sicken Americans: 'BradCast' 3/13/25 Trump Nixed Enforce-ment Against 100 Corp. Lawbreakers: 'BradCast' 3/12/25
Trump Nixed Enforce-ment Against 100 Corp. Lawbreakers: 'BradCast' 3/12/25 Bad Day for 'Strongmen': 'BradCast' 3/11
Bad Day for 'Strongmen': 'BradCast' 3/11 WI Election Could Flip Supreme Court Control, Musk Jumps In: 'BradCast' 3/10
WI Election Could Flip Supreme Court Control, Musk Jumps In: 'BradCast' 3/10 'What Else Could a Russian Asset Do That Trump Hasn't?': 'BradCast' 3/6/25
'What Else Could a Russian Asset Do That Trump Hasn't?': 'BradCast' 3/6/25 The Longest, Dullest, Most Lie-Filled 'SOTU' Ever: 'BradCast' 3/5/25
The Longest, Dullest, Most Lie-Filled 'SOTU' Ever: 'BradCast' 3/5/25 Trump Bad for Biz... and Farmers... and Nat'l Parks... and...: 'BradCast' 3/4/25
Trump Bad for Biz... and Farmers... and Nat'l Parks... and...: 'BradCast' 3/4/25 Trump Targeting 50% Cuts, Office Closures at Social Security: 'BradCast' 3/3/25
Trump Targeting 50% Cuts, Office Closures at Social Security: 'BradCast' 3/3/25
 VA GOP VOTER REG FRAUDSTER OFF HOOK
VA GOP VOTER REG FRAUDSTER OFF HOOK Criminal GOP Voter Registration Fraud Probe Expanding in VA
Criminal GOP Voter Registration Fraud Probe Expanding in VA DOJ PROBE SOUGHT AFTER VA ARREST
DOJ PROBE SOUGHT AFTER VA ARREST Arrest in VA: GOP Voter Reg Scandal Widens
Arrest in VA: GOP Voter Reg Scandal Widens ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC
ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States'
LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States' 'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States
'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States FINALLY: FOX ON GOP REG FRAUD SCANDAL
FINALLY: FOX ON GOP REG FRAUD SCANDAL COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION
COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL
CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV
Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV  CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM
CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM
CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL
RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV
VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD
RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud
EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud GOP REGISTRATION FRAUD FOUND IN FL
GOP REGISTRATION FRAUD FOUND IN FL


































